Day 18 in the Advent of Cyber 2023. McGreedy is very greedy and doesn't let go of any chance to earn some extra elf bucks. During the investigation of an insider threat, the Blue Team found a production server that was using unexpectedly high resources. It might be a cryptominer. They narrowed it down to a single unapproved suspicious process. It has to be eliminated to ensure that company resources are not misused. For this, they must find all the nooks and crannies where the process might have embedded itself and remove it.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - Alh4zr3d.
Day 18 - A Gift That Keeps on Giving
When performing Incident Response, one of the important steps in the process is to eradicate any verified pieces of malware, backdoors and so on. On Linux there can be multiple ways to automatically start processes, and it's important to scrutinize each and every one to make sure that the threat is fully eradicated.
The Challenge
In today's challenge we're given access to a Ubuntu Linux machine that have a cryptominer installed. We are firstly asked to name the service that respawns the process each time it's killed. By using the command htop we can quickly see the process that consumes a lot of the CPU in the machine.
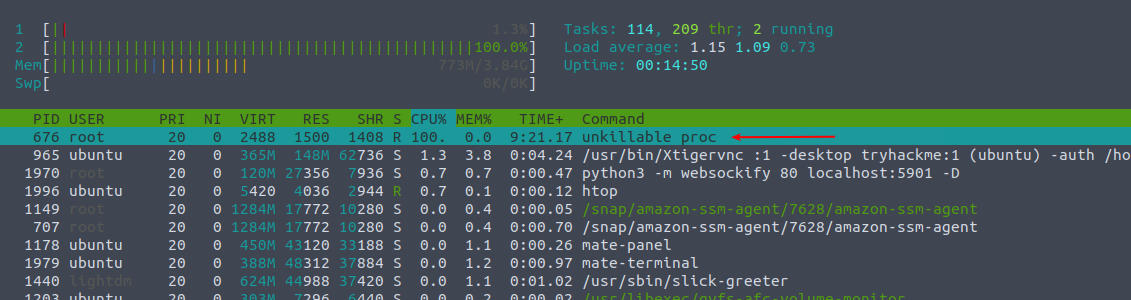
To make sure that unkillable proc is indeed the process we're looking at, we can kill it with the command sudo kill <PID> noting that it has the PID of 676. Running htop again, we can see that it has respawned with a new PID.
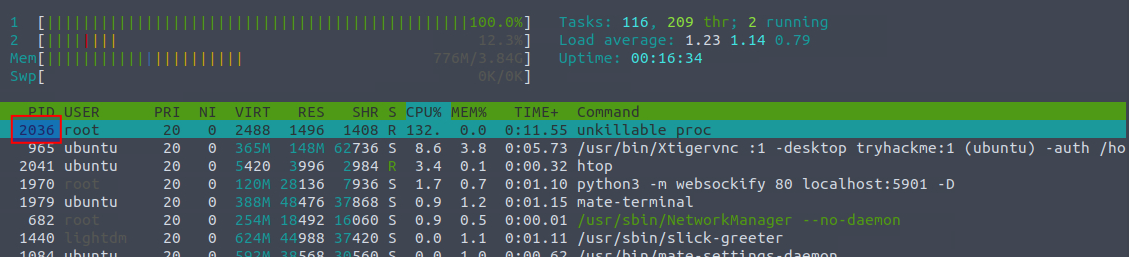
So, we need to figure out where it respawnes from. In Linux there are two common ways of doing so - crontab and systemd. A quick look on sudo ctontab -l -u root as we in htop can see that it is root running the process and using -l to list, we cannot see anything configured. Taking a look in /etc/crontab we also not see anything suspicious, and going through the content of /etc/cron.d/ doesn't reveal any suspicious content either. We saw the process being respawned almost at the same time as we killed it, so looking at the content of /etc/cron.daily, /etc/cron.hourly, /etc/cron.monthly, and /etc/cron.weekly would most likely not reveal anything for us.
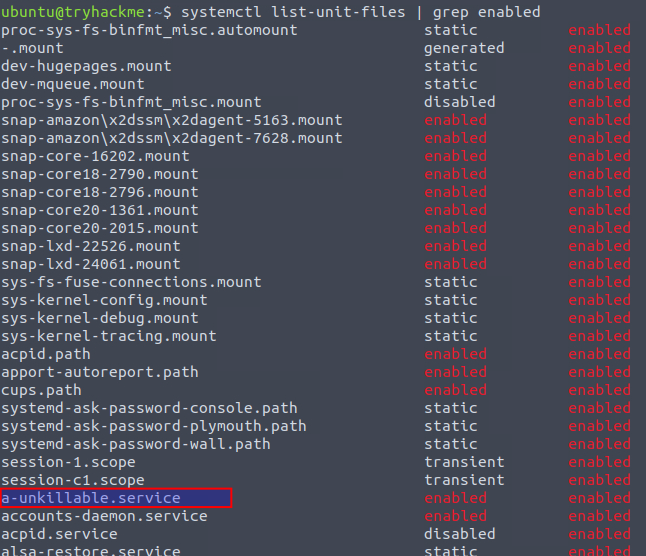
Next, taking a look at systemd via the command systemctl list-unit-files and grepping for enabled unit-files, we can see a service called a-unkillable.service that seems very suspicious and not part of a normal system. And with that, we've found the answer to the first question.
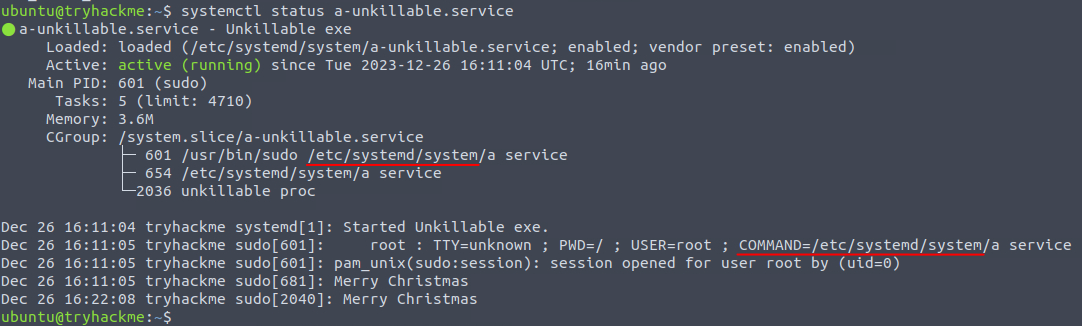
We are then asked for the path where the process and service is running. We can issue the command systemctl status a-unkillable.service to get information about the systemd service including the path.
For good measure we can eradicate the cryptominer by firstly stopping the service, then disable it so it will not start again after e.g. a reboot, and removing the service-file and command and finally reloading the systemd to update its library of unit files.
ubuntu@tryhackme:~$ sudo systemctl stop a-unkillable.service
ubuntu@tryhackme:~$ sudo systemctl disable a-unkillable.service
Removed /etc/systemd/system/multi-user.target.wants/a-unkillable.service.
ubuntu@tryhackme:~$ sudo rm -rf /etc/systemd/system/a
ubuntu@tryhackme:~$ sudo rm -rf /etc/systemd/system/a-unkillable.service
ubuntu@tryhackme:~$ sudo systemctl daemon-reload