Day 8 in the Advent of Cyber 2023. The drama unfolds as the Best Festival Company and AntarctiCrafts merger wraps up! Tracy McGreedy, now a grumpy regional manager, secretly plans sabotage. His sidekick, Van Sprinkles, hesitantly kicks off a cyber attack - but guess what? Van Sprinkles is having second thoughts and helps McSkidy's team bust McGreedy's evil scheme!
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - John Hammond.
Day 8 - Have a Holly, Jolly Byte!
Storage devices, USB sticks, harddisks and alike, all contain valuable information that we as blue teamers can utilize to analyze and investigate cause of actions for a threat actor or whatever someone have done on a machine. They often contain information about old deleted files, artifacts on accessed objects and more. These artifacts we can analyze via forensics-tools and gain an insight into what have happened on the system.
The Challenge
In today's challenge, we are tasked to investigate a suspicious USB that one of the employees had found on the ground in the parking lot and decided to attach a company-machine in the office. We're provided a Microsoft Windows analyst-machine witth FTK Imager installed and the USB attached via a write-blocker.
Firstly we're asked to find the C2 (command-and-control) domain used with the malware located on the device. We start by attaching the evidence item as a physical drive and then start to explore what kind of files and more that are on the device.
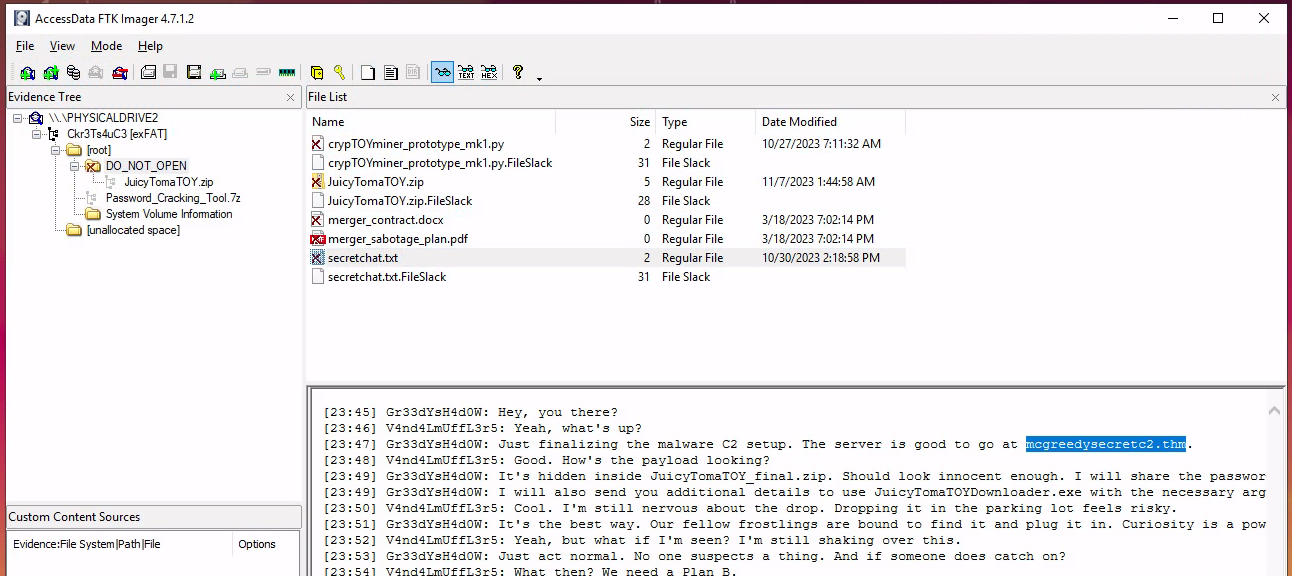
As seen in the image below, we quickly see that an interesting folder called DO_NOT_OPEN has been deleted (marked by the x in the folder-logo), and in here we see some interesting files. Taking a deeper look into the secretchat.txt we quickly see that this file contains a chat between our threat actors. In the chat, they have written which domain they intend to use, and we got the answer for the first question.
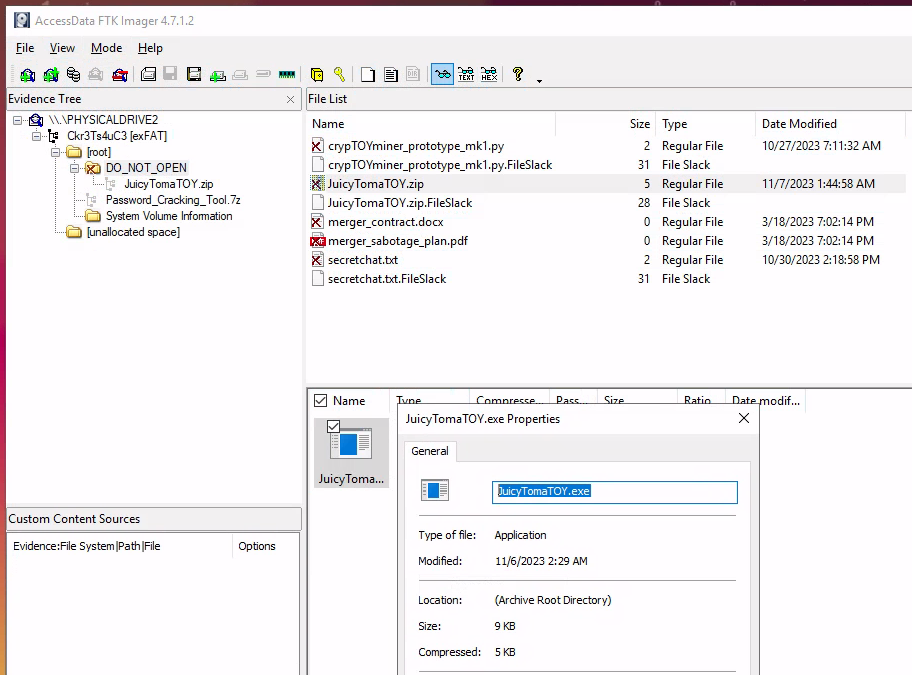
Next up, we need to figure out the filename for a file within a deleted zip archive. From the previous answer we already seen a zip archive in the DO_NOT_OPEN folder that was deleted named JuicyTomaTOY.zip. Clicking on the deleted zip archive in the file list, and we quickly sees the content of the zip archive and the name of the file.
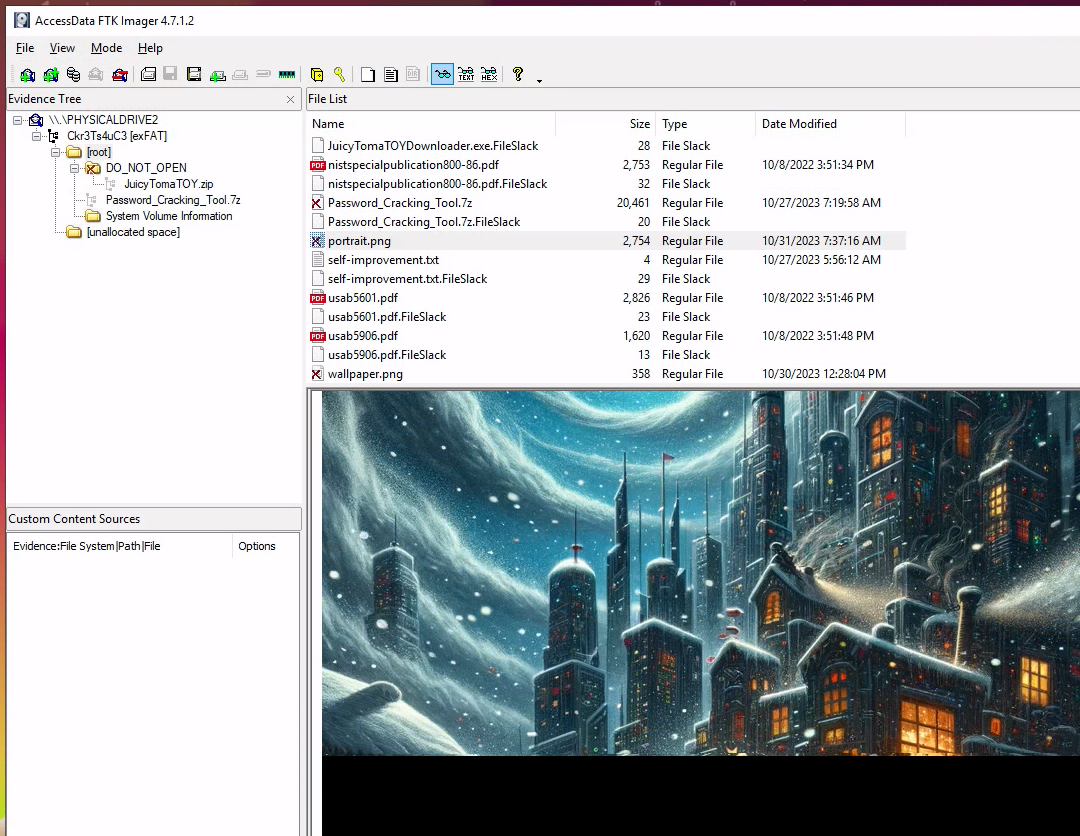
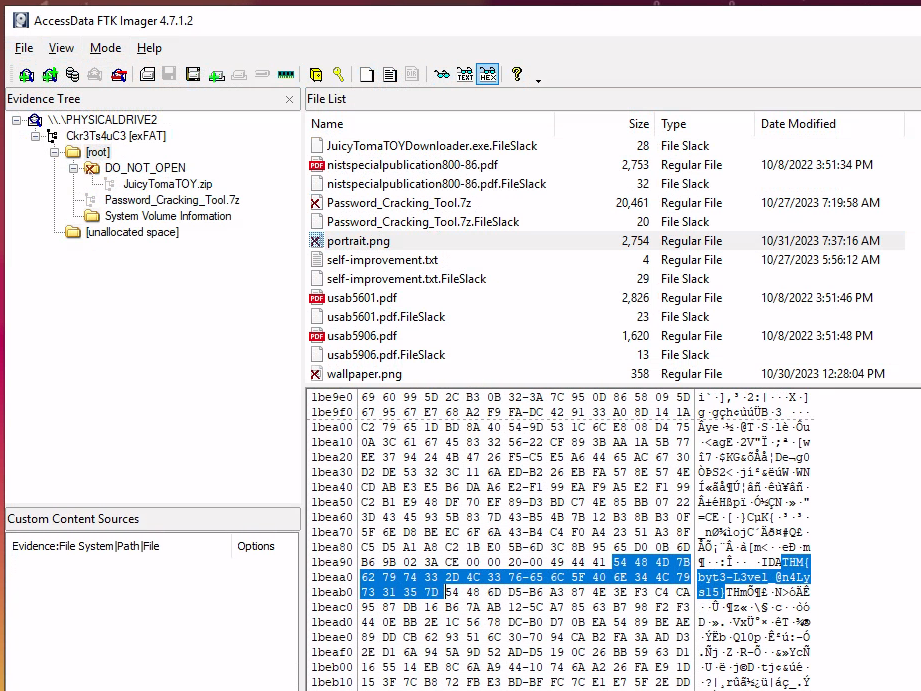
In the third question, we need to find a flag within a deleted PNG-file. Looking around and we found two deleted PNG files in the root-directory of the USB-drive. And taking a look at the first image portrait.png, we can see that it looks like the image is malformed and just shows black at the bottom. It doesn't look right, so let's start by investigating this image deeper.
Switching the file content viewer in FTK Imager to HEX and we can search through the content via [Ctrl]+F for any occurences of THM{ which we know the flags starts with. And there it is - ready to be copied as the answer.
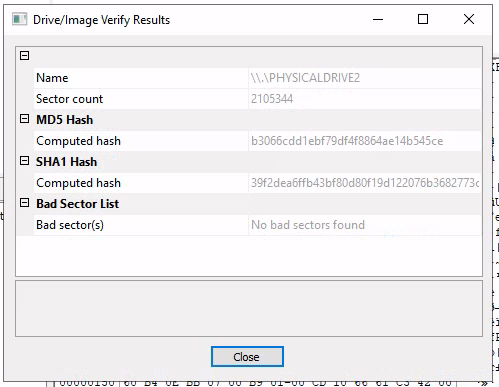
The last question is an important step in securing evidence and the Chain of Custody, which is very important if the file and the forensics are ever to be tried in court. Creating a hash of the device ensures that we know the "version" and therefore can guarantee that we haven't tampered with the evidence etc. In FTK Imager we need to click on the evidence device in the evidence tree, then click File > Verify Drive/Image.... It will now calculate the MD5 and SHA1 hashes of the device (this can take some time based on the size and processor).