Day 21 in the Advent of Cyber 3 (2021). Grinch Enterprises have been very sneaky this year - using multiple attack vectors (both know and unknown) to wreak havoc across the Best Festival Company. It's 4 days from Christmas and there's still so much work to do! McBlue, the only technical person, has suggested using automation and tooling to detect malicious files across the network.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe - Advent of Cyber 3 Day 21.
Day 21 - Needles In Computer Stacks
YARA is an awesome multi-platform tool for matching patterns of interest, searching after IOC's and what-not. With Yara you build rules defining stings and patterns you want to search for, and conditions defining how they interact - e.g. using and, or and not operators.
See the official documentation at https://yara.readthedocs.io/en/stable/index.html for a lot more. Also the GitHub repository https://github.com/InQuest/awesome-yara has a very awesome collection of community-rules, open source-rules, tools and more.
The Challenge
While deploying the attached machine for the challenge, we are given a testfile to work with - as yesterdays challenge, this is an EICAR test-file.
Following the challenge, we create a Yara-rule file following the standard-syntax.
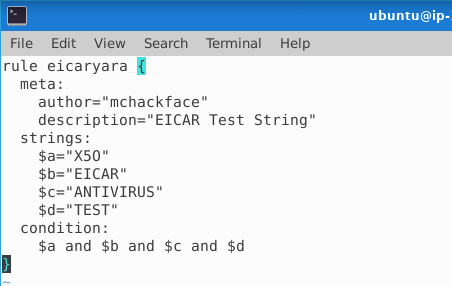
This rule defines four strings ($a ,$b, $c and $d) that are conditioned to all be present in a file before the rule is triggered as "found". We can run the rule check for the file with:
yara eicaryara testfileFor the first question - if we change the first string in $a from a large O to a zero 0, the rule would no longer match on the testfile as not all the strings is found. But if we change the operator in the condition between $a and $b ... to use the or ($a or $b ...), we now checks for string $aor the rest.
When running the yara command it is possible to add the flag -m to get display of the specific rule that was triggered (it is possible to have multiple rules within the same rules-file).
For the third question, we have to look at the syntax for the rules. Information about authors, descriptions and more, are present under the meta: section which is the metadata-section.
If we want to negate the output-result and only see the rules that did not match, then the flag -n can be used.
The last question, we change the rule to have a zero in the $a string, but also still have all and-operators. This will not match the testfile as it has to match on all the strings. Running the yara command with the -c flag returns a count-output of hits. In this case, where not all strings are present, we do not get any hits.