Day 16 in the Advent of Cyber 3 (2021). Grinch Enterprises has decided to use the Best Festival Company to try their new ransomware service. McSkidy wants our help to gather information about this ransomware gang, that she can use and share with the the security community.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Advent of Cyber Day 16: OSINT.
Day 16 - Ransomware Madness
OSINT, or Open Source Intelligence, are the art of collecting and obtaining information from free and public sources. Adversaries and offensive teams often use OSINT to perform their initial reconnaissance and gather information about their target, known attack vectors, things to use in phishing, social engineering and more. Agencies, defender teams and law enforcement also leverage OSINT to gather intelligence and information about threat actors and adversaries that they can use and share in the security community to be prepared for attacks, enable them for better detection, to arrest the bad hackers and more.
The Challenge
This challenge start with an obtained ransomware note:
!!! ВАЖНЫЙ !!!
Ваши файлы были зашифрованы Гринчем. Мы используем самые современные технологии шифрования.
Чтобы получить доступ к своим файлам, обратитесь к оператору Grinch Enterprises.
Ваш личный идентификационный идентификатор: «b288b97e-665d-4105-a3b2-666da90db14b».
С оператором, назначенным для вашего дела, можно связаться как "GrinchWho31" на всех платформах.
!!! ВАЖНЫЙ !!!To my knowledge, this looks a lot like cyrillic characters - e.g. used in the Russian language. Let's try a Google Translate to get an idea of the ransomware note.
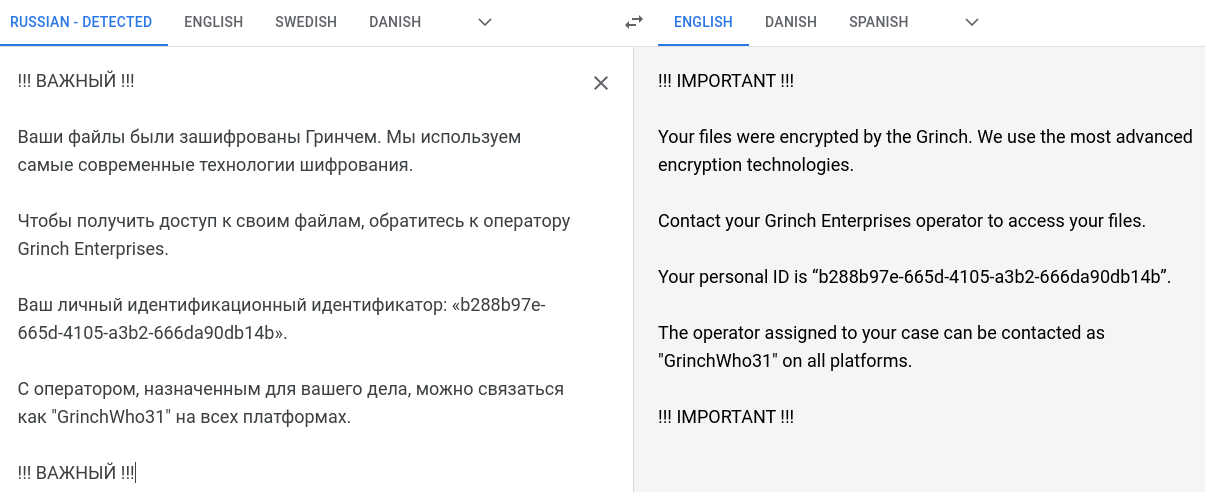
Alright - it seems we are on the right track. Already in the note, we are given the answer for the first question "What is the operator's username" - GrinchWho31.
Next up, we are tasked to figure out what social media the username is associated with. We could start by manually checking, searching on Google in high hopes - or we could leverage some of the cool tools that the security community has build. One very quick'n'dirty, is the webpage: https://whatsmyname.app/
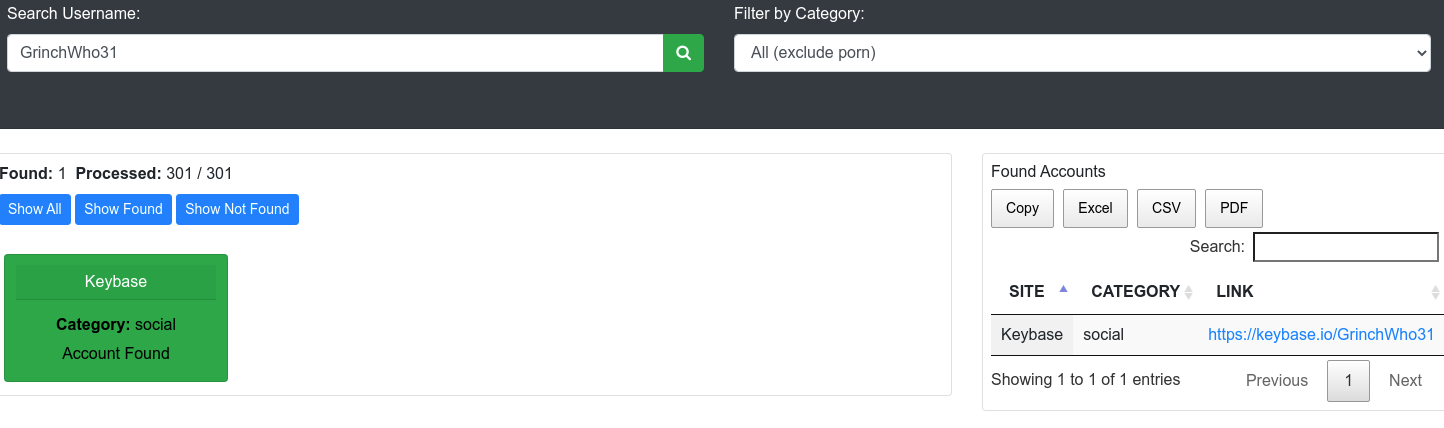
So we know with certainty that the operator has an keybase.io account. Keybase.io is a messaging and file-sharing platform providing its users with end-to-end encryption and more.
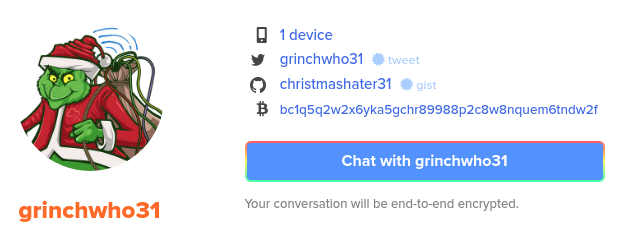
Looking at the keybase.io-account for the operator, we see that the operator has connected a twitter-account. And looking at the twitter-account, we clearly sees that this is a real persona-account associated with the username that we saw earlier. And with that we have the answer for the next question.
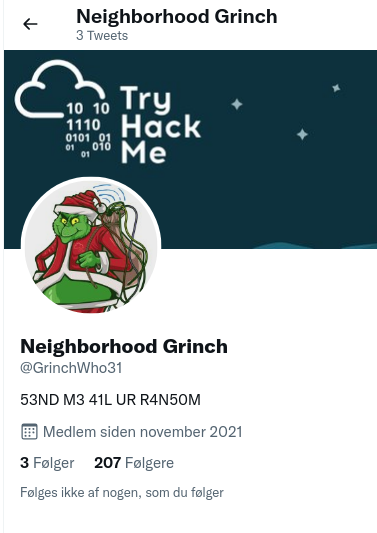
When you use keybase.io, you have a cryptographic identifier used to e.g. link other platforms to the keybase.io-profile. On twitter we can see this identifier in the single tweet the operator has published, and we have the answer for the question. As we know - this identifier is associated with keybase.io, which is the next answer.

We are then questioned with what the bitcoin address of the operator is. As we saw earlier on the keybase.io profile, the operator has already claimed a bitcoin-addr, and with that - a question is answered.
A bit more tricky is the next question. Because, where is that bitcoin address leaked from? We see the address on the keybase.io site, but that is not the answer.
Nothing interesting is found in the twitter-account that we found, but on the keybase.io we also see a linked GitHub-account.
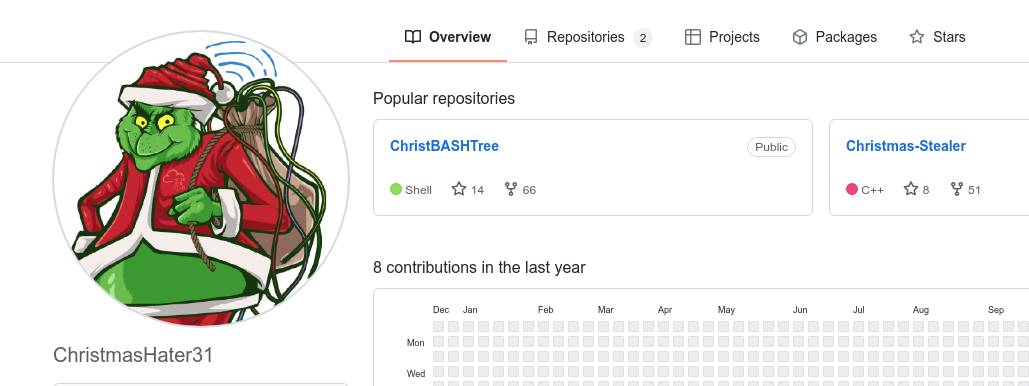
On GitHub we see two repositories - "Christmas-Stealer" as C++ code and "ChristBASHTree" as shell/bash-code. Taking a look on the "Christmas-Stealer" we see a single file ransom.cpp, we see a reference to the Bitcoin-addr. Using "github" as the answer for the question, and we are indeed correct.
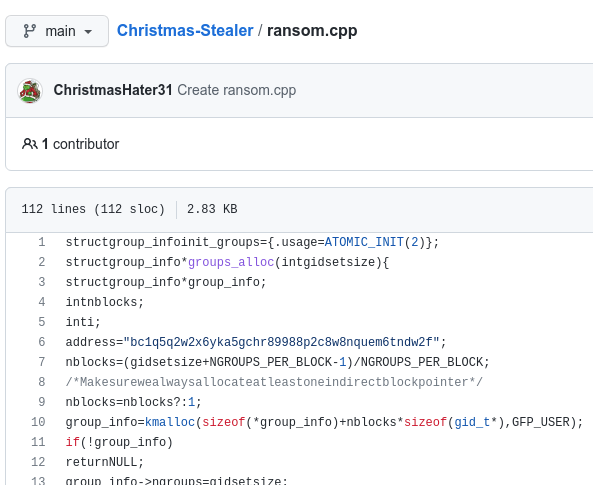
Finally we are tasked with finding the personal email and real name of the operator. Knowing that the operator has a GitHub, the operator might have performed some information leaking in the versioning that they was either not aware of, or thought that is wasn't public.
In the other repository of the user, "ChristBASHTree", looking at the commit-history we quickly find the latest commit where the user removed name and email - just forgetting that when it first was committed and uploaded to GitHub, the history is preserved and we are able to find that information.
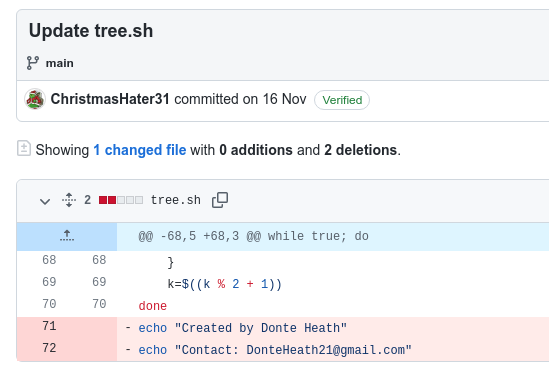
And with that - OSINT has been performed and we have answered all the questions in todays challenge.