Day ten in the Advent of Cyber 3 (2021). After all these nefarious activities seen by the Grinch Enterprises, McSkidy wants to perform an internal security assessment to try figure out how they were able to penetrate the Best Festival Company's network and infrastructure.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe! Advent of Cyber 3 - DAY10 | Offensive is The Best Defense.
Day 10 - Offensive Is The Best Defence
nmap is a powerful tool used for enumerating and performing network scannings. With this, it's possible to gain knowledge into which ports, services etc. that are remotely available on a server or machine. This information can be used in e.g. security assessments and pen-testnings.
The Challenge
The challenge today, is all about helping McSkidy performing a security assessment for a machine, by enumerating on how Grinch Enterprises might was able to infiltrate the machine.
With the Attack-machine deployed, we are asked to number the ports in the 1-100 range, are open. This is quickly looked up with the command:
nmap -sT <MACHINE_IP>This command performs a scan of the 1000 most common ports using the full TCP-handshake.
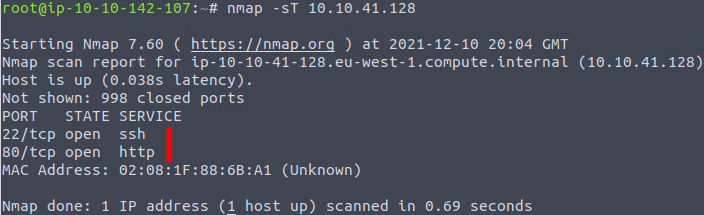
We are then asked to provide the port number for the lowest number and then the service-name for the highest of the two. Both information obtained with the first command as seen in the picture above.
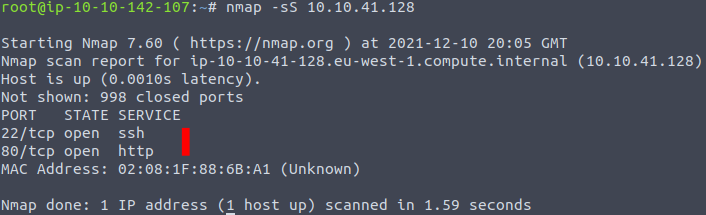
Then we are asked to perform the same scan again, but using the -sS flag. This flag makes nmap only perform a SYN-scan, meaning that only the first part of the TCP-handshake is performed, making it harder for the webserver/company to figure out what had happened. As seen in the picture below, we get the same results as before.
Okay, now we need to look into what service-version is running on the webserver's port 80. This can be done with the flag -sV which is a flag instructing nmap to perform a service-enumeration. Most services default to provide "banners" where application name, versionnumer and more often is disclosed. In a hardened environment, this should always be disabled. But lets see if we can perform a "banner-grabbing" and retrieve the information.
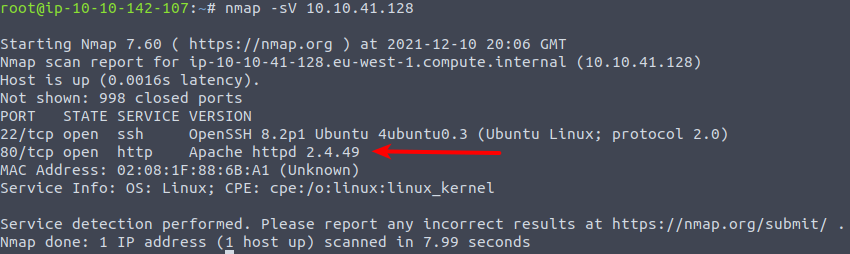
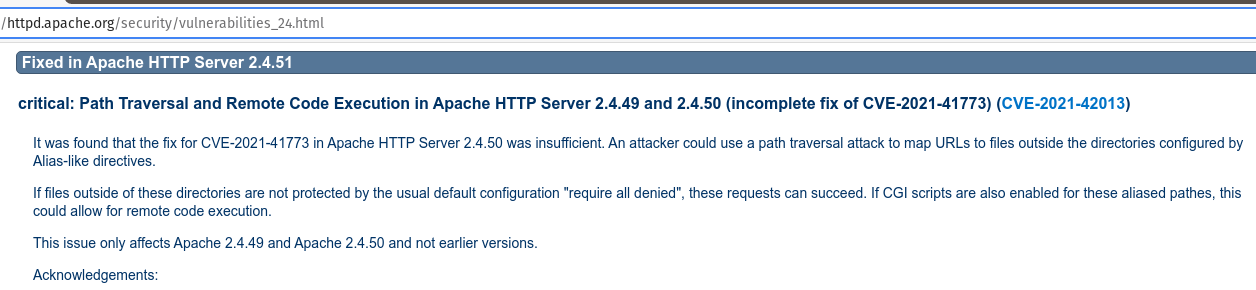
Now that we know the version numbering of the webserver application, we can go search on the Internet to look for vulnerabilities that could be used in nefarious attacks by adversaries. Looking at the release-notes on Apache's webpage, we quickly find "path traversal" and "Remote Code Execution" vulnerabilities patched in later version - vulnerabilities that indeed could lead to a full compromise of the webserver. And with that, the answer for the next question.
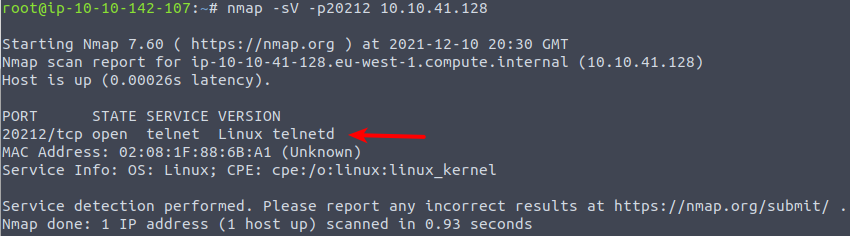
McSkidy is afraid that Grinch Enterprises have left a backdoor on the system and wants us to see if and suspicious services is listening on open ports. To do so, we need to scan all 65.535 available ports - something that can be done by adding the flag -p- to our nmap-command. Let's perform a full TCP-scan.
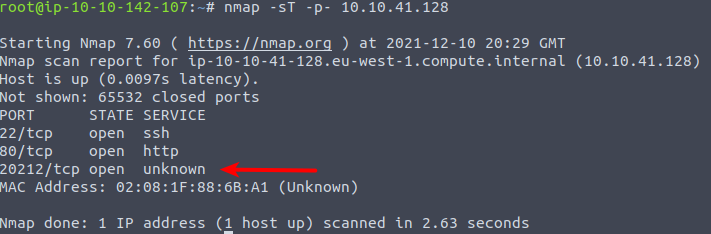
And would you look at that! Most definitely a very suspicious port is open with a service behind listening for connections. This gives us the answer on that question.
But, what service is listening? We can use the -sV again to figure that out, and as we are only interested in that specific port, let's specify that with -p20212.