Day nine in the Advent of Cyber 3 (2021). Today McSkidy has found a large amount of traffic is entering one system on the network and wants to investigate the packet capture of it.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Advent of Cyber Day 9: Packet Analysis with Wireshark.
Day 9 - Where Is All This Data Going
When traffic is passing on the network, this is done in small chunks of "packets" withholding the data and many other meta-information for the protocols to ensure the correct data is delivered to the correct machine, application and even e.g. browser-tab.
With a "packet sniffer", "Network Sensor" and similar, this traffic can be captured for analysis and deeper investigations into suspicious behaviours, known adversaries and of cause for troubleshooting.
The Challenge
We are provided with a packet-capture file of the type .PCAP. This can be opened with different tools, but we are going to use one of the most used tools out there - Wireshark.
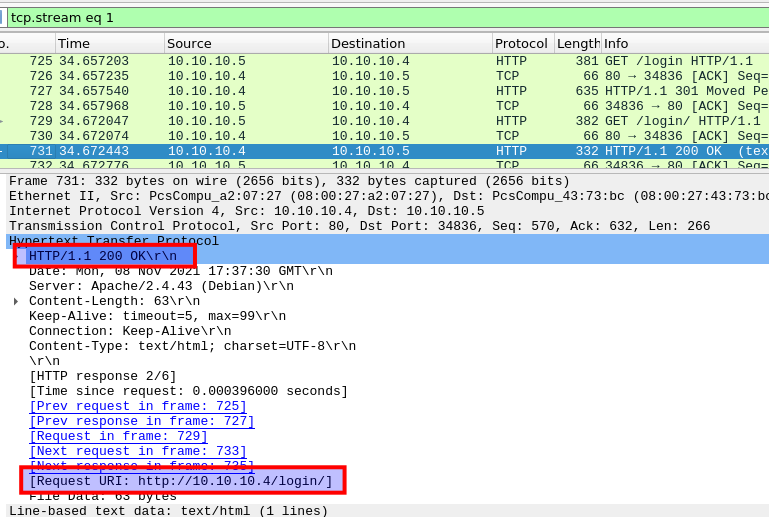
The first question is for finding the first directory which was found on the server. To find this, we apply a filtering-option so to only see the HTTP GET requests: http.request.method == GET. Then we can see the first requested directory is /login and following the HTTP-stream (right-click --> Follow --> HTTP Stream) we can see that the webserver responds with a success status-code thous telling us that this is indeed the first directory found on the server.
Then we are tasked to figure out the username and password used to logon the webpage was. As this seems to be clear HTTP and not HTTPS the traffic-data is not encrypted by default and this should be possible by finding the correct packet and looking at the form-data.
So we change our filtering to search for POST-requests with http.request.method == POST and look for a packet for the login-page.
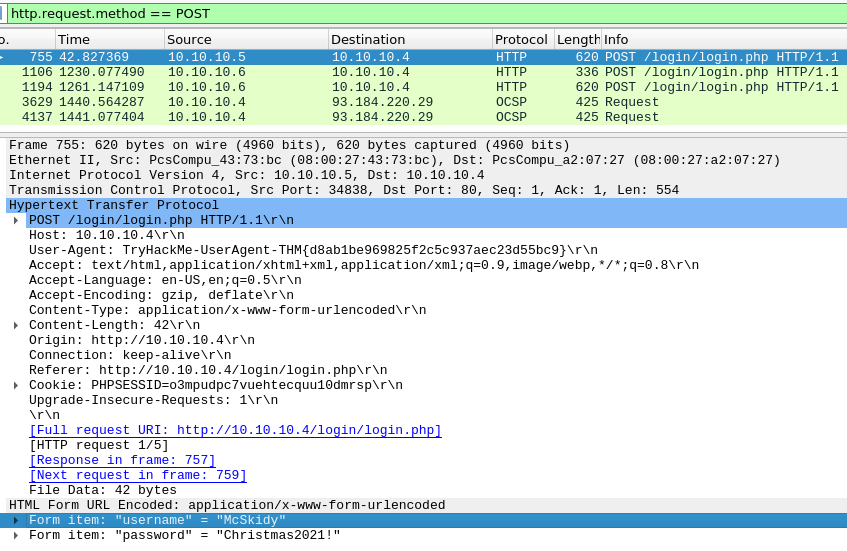
This also gives us the answer for the next question, as we look for the User-Agent provided in the same request-packet.
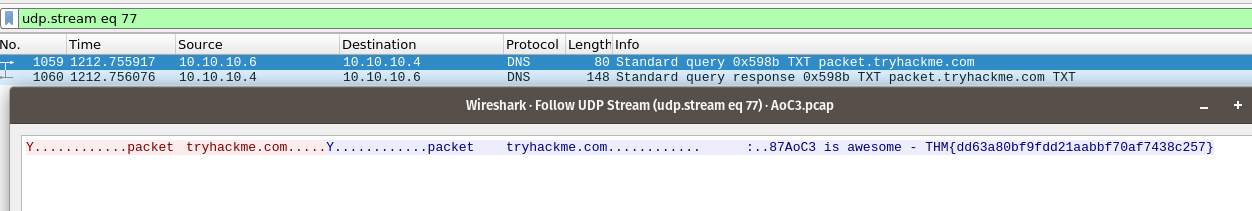
Okay, now on to DNS. We are informed that a DNS request for a TXT Resource Record has been made, and that we have to find the flag in the response to that. We change the filtering to DNS to only see DNS-protocol related packets and look for the TXT-request. When that is found, we follow the UDP Stream (right-click --> Follow --> UDP Stream) and we are presented with the data.
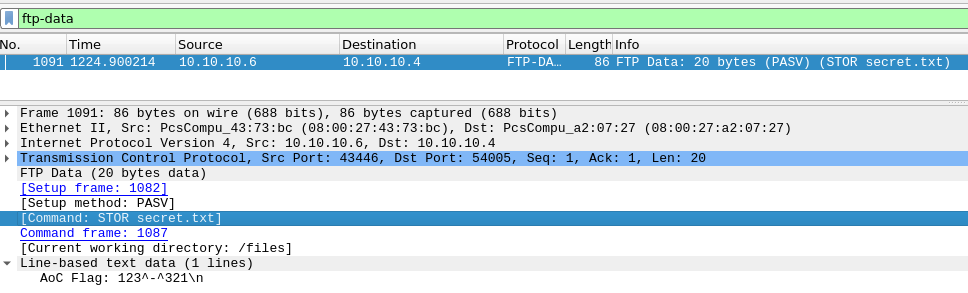
Next up, is FTP. The classic FTP-protocol is not encrypted, so to find the password used for authentication is trivial. Filtering for the FTP-protocol with ftp and then looking for a request-packet for PASS and we have the used password.
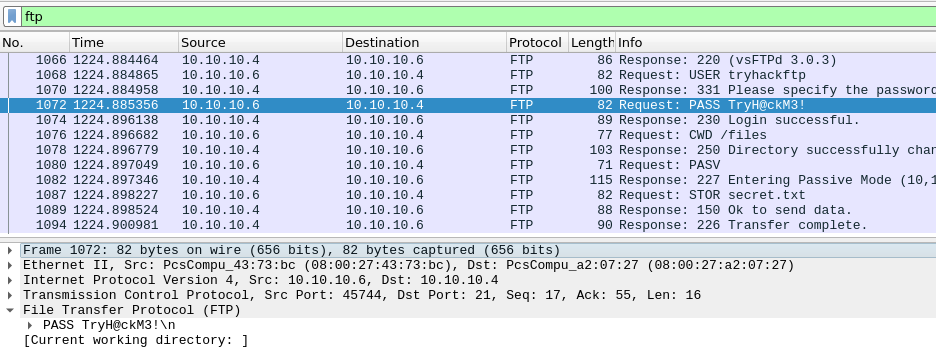
And then we only have the last two answers to find. Here we are still tasked with looking into FTP, but this time for the data. The FTP-protocol uses two streams/ports - one for control commands and one for the transferred data. So yet again, we change our filtering to ftp-data and see just one packet for a single file. Under the "Command"-section of the packets protocol-metadata we see that the command STOR was used to upload the file "secret.txt" and for the last question, we can see the content of the file under "Line-based text data".