Day 20 in the Advent of Cyber 3 (2021). McPayroll is processing the bonuses for all the hardworking elves. One of the Elves has sent McPayroll a file that they're claiming contains their updated payment information. The only problem is that she doesn't recognize the Elf - could this be a sneaky attack from Grinch Enterprises to cause more havoc?
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe! Advent of Cyber 3 - DAY 20 - What's the worst that could Happen?.
Day 20 - What's the Worst That Could Happen?
We are tasked to help McSkidy with a file analysis. Often adversaries try to gain initial foothold by delivering malicious and nefarious files to employees and what not. These malicious files can be analyzed in a sandboxed environment for safety.
The Challenge
In static file analysis, CTF's and alike, when presented with a file - it is always a good idea to investigate what type of file it really is. The file extension can from time to time try to fool the user into thinking it is a benign txt-file, when it actually was an executable or something similar. This first step also ensures that we start the file analysis in the right direction and not wasting too much time on non-beneficial work.
As with the challenge from yesterday, we are going to start the attached AttackBox, providing us with the files for the challenge. With the machine started, we are asked to look at the file testfile on the Desktop.
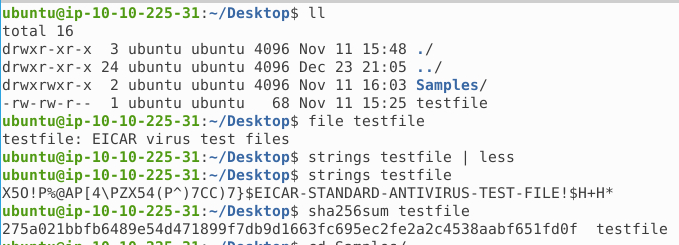
So the first step is running the file command. Here we see that this is a special file-type called "EICAR". Being in the cyber security field, we know that this is a special file created with the sole purpose of being flagged by antivirus-applications. This e.g. for testing the functionality, ensuring the system is working, testing your procedures etc. See more about the file at https://www.eicar.org/?page_id=3950
Another easy step, is to run the command strings this works for all file-types and returns the strings in the file. For binaries this technique is useful for getting a quick'n'dirty looke into the ins and outs of the file. Often it can show IOC's, clues of what the binary has of functions etc.
Running strings on the testfile and we see one large string, that is the answer for the second question.
Next up, we are going to calculate the hash of the file via the command sha256sum. Doing this, gives us a nice small hash-representation of the file, that we can use to enrich our investigation. Maybe others in the security community have seen the same file before and so on. One popular place for sharing this information, is https://virustotal.com/. We can search for the hash on the site, upload a file to check and then see plenty of information on different antivirus-applications and their take on the file, sandbox-detections, and community-provided assessments.
To answer the next question, we search for the file hash on virustotal.com and find the following page: https://www.virustotal.com/gui/file/275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f/
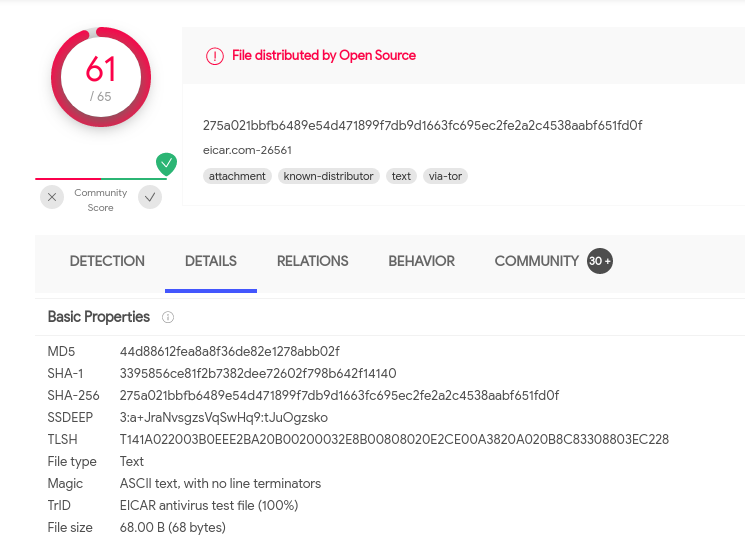
On here we can find the first seen-date under the "Details"-pane, and as well see the classification Microsoft has given the file under the "Detection"-pane.
For answering the last two questions we are guided to https://www.eicar.org/?page_id=3950. Where a quick look finds the answer for what the file was used to be called (named after the inventor) and the maximum length of characters in an EICAR-file as per definition.