Day 18 in the Advent of Cyber 3 (2021). Grinch Enterprises has been gloating about their attack on an underground forum. We know they were specifically targeting organizations in a campaign they've themed "Advent of Cyber" (AOC) - what a frustrating coincidence. Tracing the user back over time - we also encountered a reference to using AWS Elastic Container Registry (ECR) to store container images they use as infrastructure in their attacks.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe! Advent of Cyber - Day 18.
Day 18 - Playing With Containers
Today's challenge is all about getting some knowledge on container-technology and Docker in particular. The more traditional way of virtualizing are via virtual machines. Here we emulate an entire machine, giving it a full-fleched set of capabilities. But this is also a bit "heavy".
Containerization gives us the ability to build and pack applications etc. in smaller "containers". These, when run, acts like an operating system tailored for the specific application. The container relies on the host-system for the "overhead"-functionality (networking, I/O, etc.) and have a container-daemon running that provides the necessary functions via proxying. This also create security-barriers, ensures the containers are light-weight and that all containers from the same image are alike.
When these container-images are built, they follow the Open Container Initiative Distribution Specification. After they are built you can share the container-images via local/private channels, use Dockerhub (for docker) or cloud-services like AWS ECR (Elastic Container Registry) with the possibility for both public and private repositories.
The Challenge
Our first question is for the command used for listing all the images stored in the local container registry - aka the images pulled from various repositories. This is done with the command docker images, and we can see on the TryHackMe AttackBox, there are multiple images available.
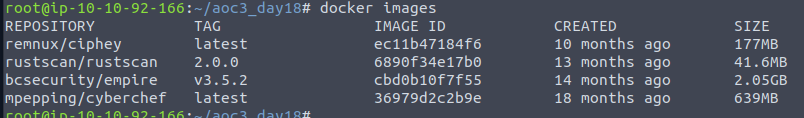
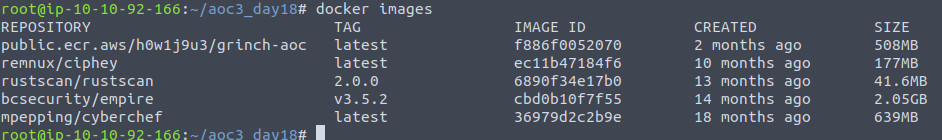
With the challenge we are told that the Grinch Enterprises has a docker image in the AWS ECR taht we could take a look at. So to do that, we need to fetch the image with a docker pull <image>-command. We can then verify that the image was fetched by issuing the image-listing again.
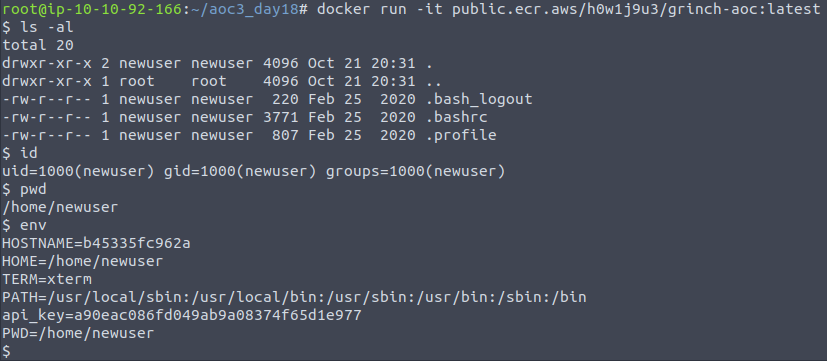
When performing enumeration or similar for containers, one of the interesting things we can do as a start, is to start a terminal in the container, which gives us the ability to "poke-around" and get a feeling of what it is, what's available etc.
To do so, we issue the command:
docker run -it <image>This gives us an interactive terminal inside the container, where we can perform some quick commands to get an idea of the directory we are in, the user we are privileged with and the environment variables.
Seeing the below output, we can see a api_key in the environment variables - something that is very popular in containers to use as the environment variables can be changed and administered when starting containers. Though here, it has been "baked in" with the image and therefore provides us with some information disclosure the Grinch Enterprises might not be to fond of.
The next thing to do in a container-investigation, is to look at the image itself. To be able to do that, we need the image file archive so we can extract the files. In docker we can do this with the command:
docker save -o <save-to-this-file>.tar <image>When the image has been saved to a .tar file, we can use tar -xvf <file> to extract it.
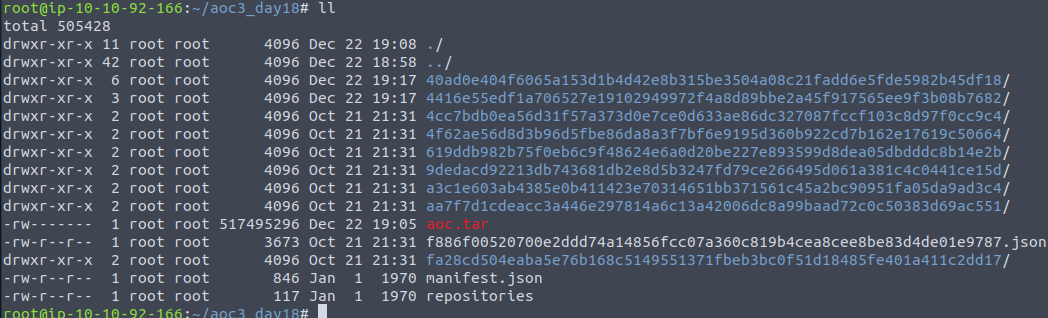
We can see plenty of files and folders. One of the more interesting is the manifest.json file as this is giving us lots of information about the build. This file tells us about the different layers the images has been built with. And the file is also out answer for the third question.
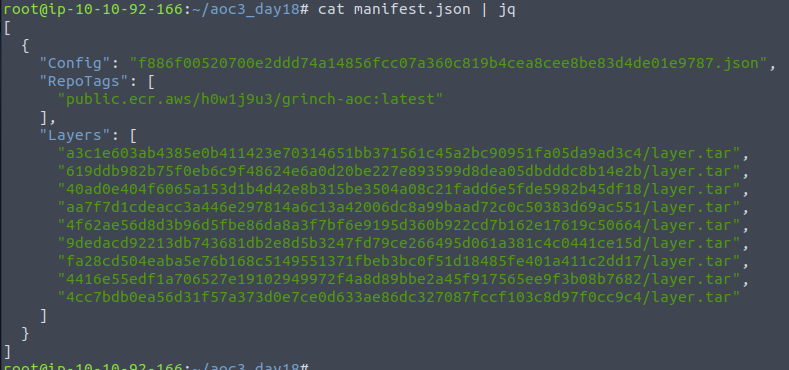
The first interesting information is the "Config" - this file, also found in the extracted directory, represents the underlying configurations and commands used to build the container image. This can sometimes give us information we could use to enumerate the different pieces of the container etc.
Looking at the config-json, we see an interesting command where envconsul from Hasicorp on GitHub is cloned and used.
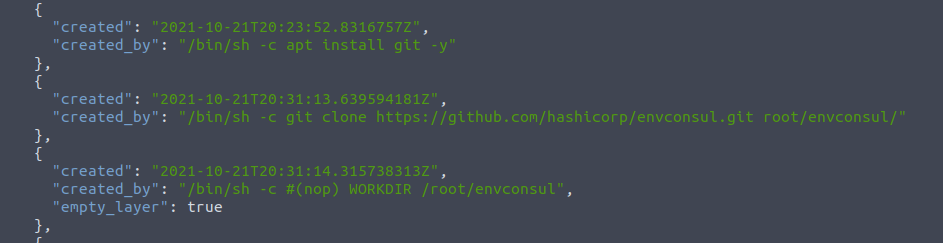
Looking at the documentation for that application, https://github.com/hashicorp/envconsul, we get the information that this has something with the environment variables etc. This could be interesting. Therefore, we will go looking into the sub-layer for the container to find the configuration information's etc. for this envconsul.
All the sub-layers have their own directory, so starting from the top, we can go in, perform an extraction of the layer.tar file using the same tar -xvf as before, and then see what's inside. Already on the second directory we seems to have found the layer we wanted.
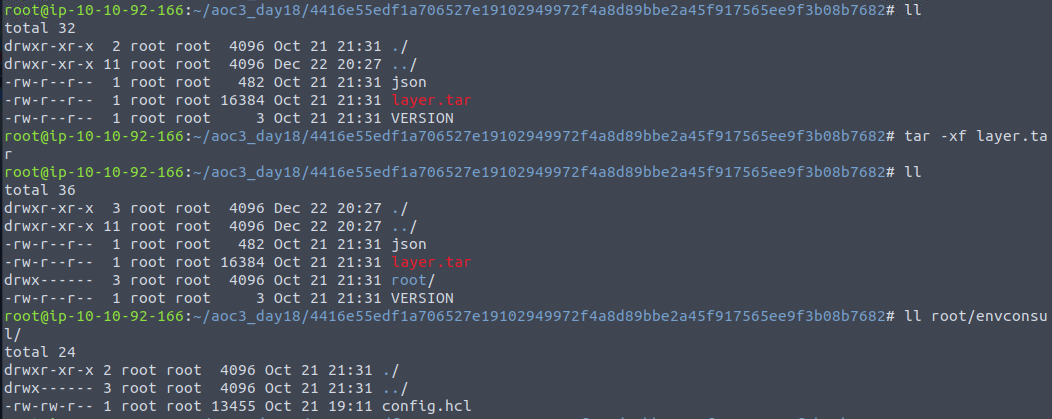
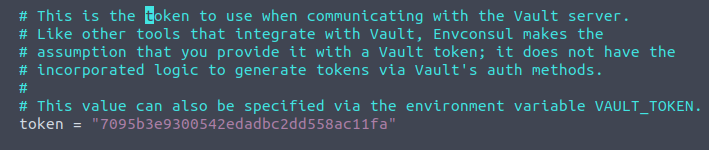
As we can see, when extracted we are provided with a root directory with a envconsul directory inside. In here we find a config.hcl-file, that we can open with vim and perform a search for "token" as this is what we are asked for in the final question. To do so in vim you type /token<Enter> on the keyboard, and we see a token-value. Again something not good having in public container-images as this is sensitive information disclosure, that could lead to a compromise of some sort.