The last challenge I had time for, was the DangerZone 1/4. In total, the DangerZone challenge is comprised of 4 parts with this one in the intermediary category and the rest in the "Hard"-category. As I'm participating in TryHackMe's Advent of Cyber 3, Christmas is quickly coming and all the work Log4Shell has added to an already filled calendar - well, time is short.
So let us fill it with fun 🙂
Just as the WEB-challenges in the beginner-category, this challenge is hosted in a room at TryHackMe - https://tryhackme.com/room/dangerzone. It is called a "Boot2Root" so the main objective would be to gain full access to the machine, and in the process capture the four flags.
At TryHackMe we only get the text "Are you ready for The DangerZone?!" - not much help from that. This means we are going to perform some enumeration on the provided machine-IP to figure the next steps out.
The first thing I did, was to load up the site in a browser. Nothing special - just an image. Perhaps some interesting information's in the HTML-source?
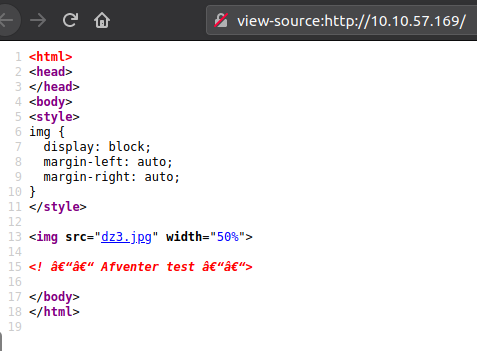
Okay that was not a lot. In the comment though, we see the message "Awaits test". This is suspicious, but a quick manual enumeration on the site with adding /test/, ?test=mchackface, ?page=test or similar didn't reveal anything. So now to the more interesting enumeration with nmap. First we start with a quick scan via the below command:
nmap -sT -p- 10.10.57.169This returns with the three ports 22, 80 and 60080. Interesting. At port 80 we already saw the webpage suggesting something about "test". Okay, so after this I made a bit more elaborate enumeration on the three ports:
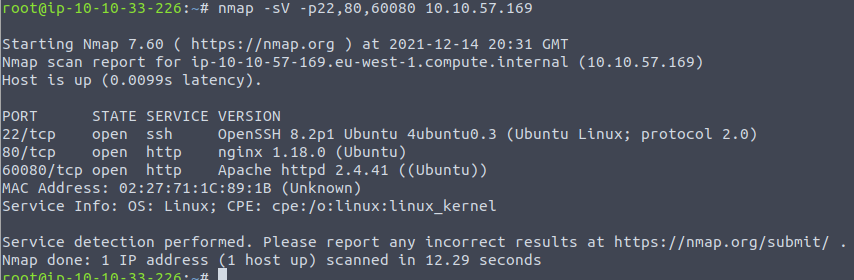
The most interesting port right now is that weird port 60080 where we see Apache Httpd running as the service.
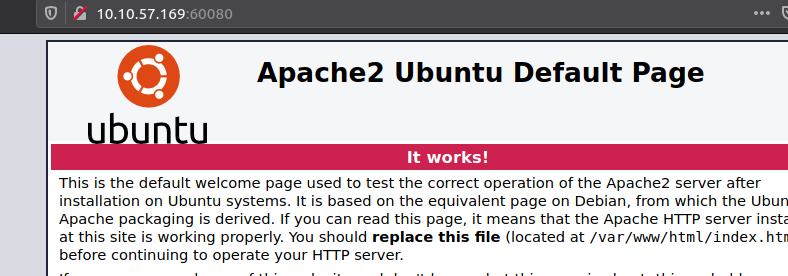
Looking at the port in a browser just shows us the default page from the installation of the application. Running through the HTML-source didn't reveal anything, so either this is a decoy or we have to perform a bit of fuzzing to find/reveal pages or similar.
To do that, I'm going to use a tool called gobuster - it's very similar to dirbuster but a bit faster.
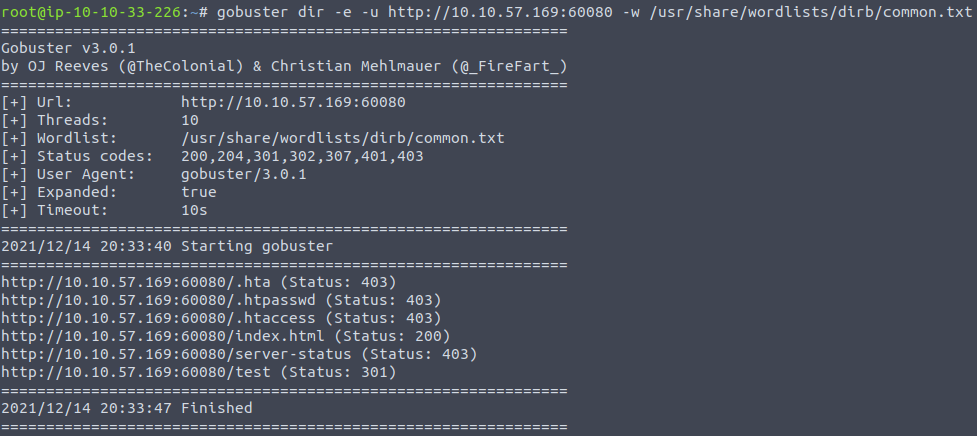
Okay - so we have a directory called /test on this port. Related to the first site we saw, that is very interesting. Opening that site in the browser reveals the same image again, though this time with the text "Under construction!" beneath it. And again, nothing of interest in the HTML-source.
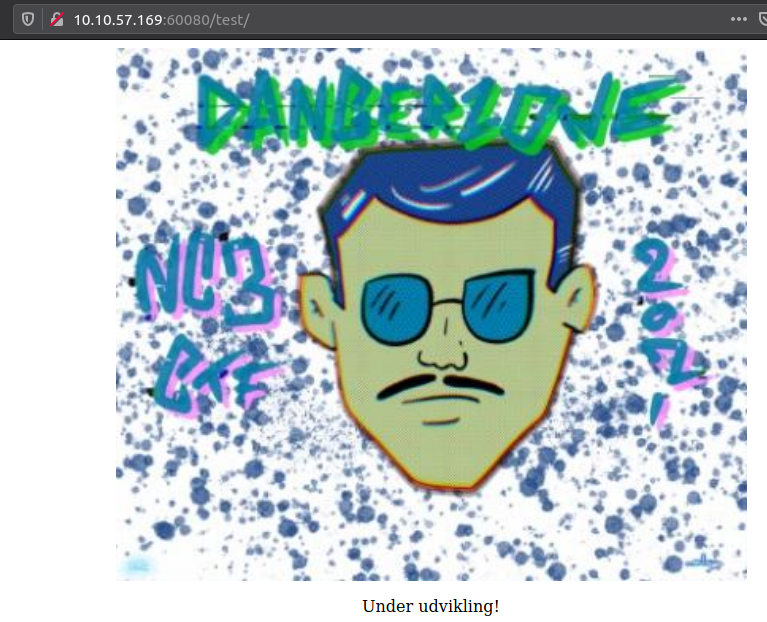
With nothing overly interesting here, we are going to perform another fuzzing. This time for the /test directory.
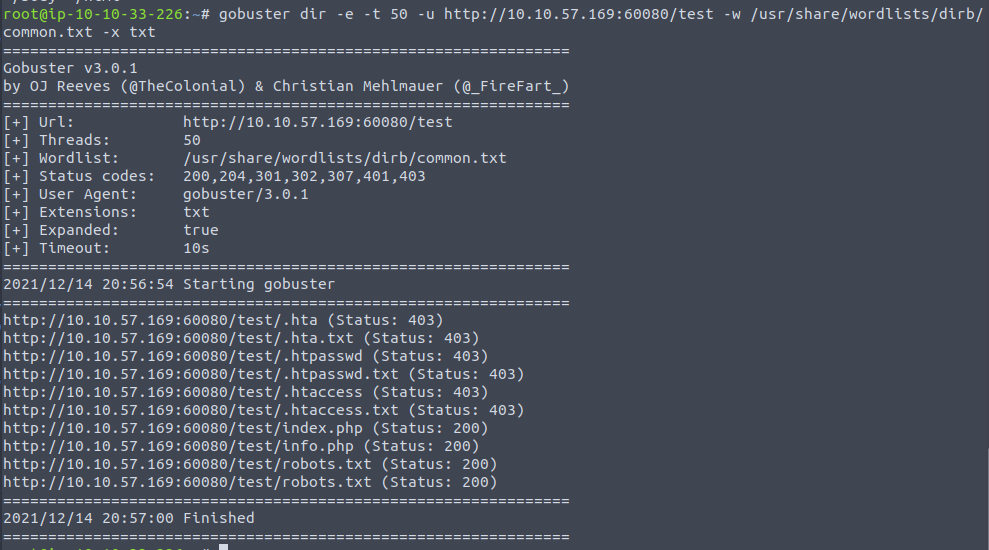
Uh - more interesting things found. Looking at the status codes of 200 OK, we see a page named info.php and a classic robots.txt. Robots-files are files used to instruct web-crawlers how to e.g. index the page, what pages are not allowed to be indexed for e.g. search-engines etc. (though it is just "advise" or "wishes" from the site-owner - the crawlers are not forced to follow them). From the .php-extension on the info.php page we also know that PHP is running on the application.
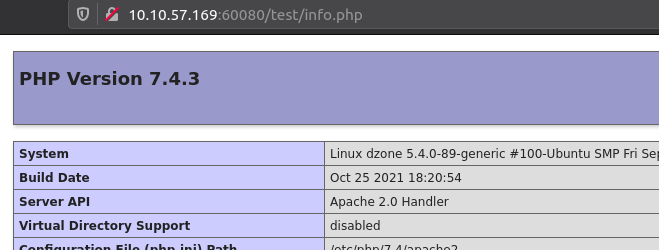
Looking at the info.php-page in the browser we see that the phpinfo();-function in PHP has been used to show all the information for the PHP-environment. This is really interesting information we most definitely are going to use at some point. Though, no flags or directly leads to our first flag seems to be present on the page.
But looking further at the robots.txt, we see a much strange directory that is disallowed and the webmasters tries hiding.
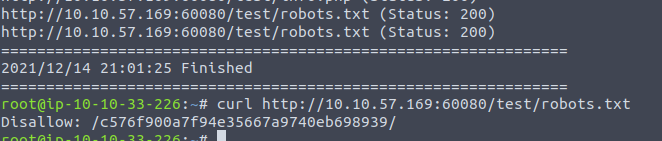
Next thing up is for sure taking a look at that place:
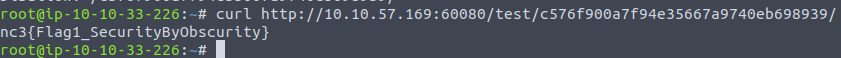
Yay! We found our first flag in the DangerZone Boot3Root!
Unfortunately that was all I had time for in the NC3 CTF2021 this time around. It has been really fun to participate in the CTF, the challenges has been interesting and next year we're going full dive!
Some of the challenges left sounds very interesting, and it seems that the DangerZone challenge is still up in the TryHackMe room - maybe after new years, I can find time to look further into the challenge. Not the CTF, but just for the fun of it 😉
And hey - 72nd place out of at least 404-teams with the limited time-frame and the very late start. I'll take that as a win!
