Going forward, the next challenge in the Intermediary category is called "Zoomer". We are provided with a file called zoomer.jpg and the text "Are you a Zoomer?".
First things first, downloading the file and run a file command to see if the file-extension is correct.
user@hostname:~/CTF/NC3/2021-12/Øvet/Zoomer$ file zoomer.jpg
zoomer.jpg: JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=4, xresolution=62, yresolution=70, resolutionunit=2], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], Exif Standard: [], baseline, precision 8, 1567x961, components 3
Okay - so the file is indeed a JPEG image. Though it seems a bit odd - almost like it contains multiple images? We can also verify that with hexdump -C | less and look for multiple "Exif" stings, we can try a binwalk or similar. But firstly lets take a closer look at the EXIF-data. Sometimes in CTF's, the flags could be hidden in there.
To do so, we are going to use the tool exiftool which can be installed via:
sudo apt -y install libimage-exiftool-perl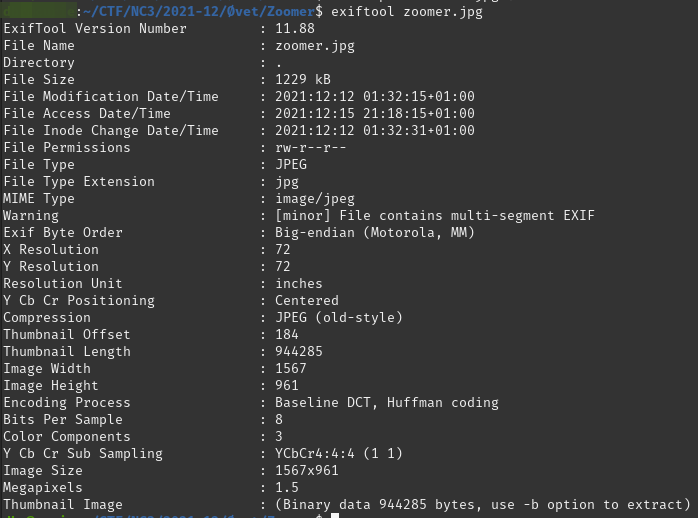
Looking at the EXIF-data, we can't see anything interesting - just that it looks like there are thumbnail image included in the file. That could be the suspicious sting we saw in the file command.
As seen in the screenshot, we should be able to run exiftool with the -b flag to extract the thumbnail image. I tried that, but it just seemed weird and didn't work properly. What about the tool binwalk? That is a quite nice tool to scan binary images for embedded files and extract them as well.
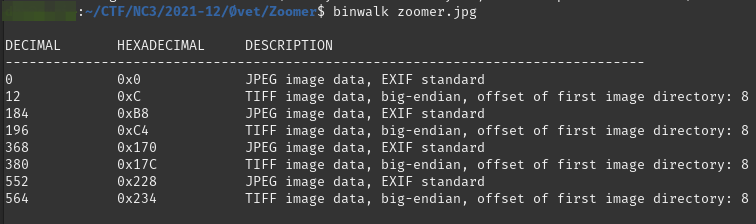
Alright, so it seems that we were right in that there are multiple files embedded in the image. binwalk has the -e flag we can use to extract the embedded files. Though I had issues with getting that to work properly. I might not know binwalk good enough - maybe there are ways to work further with that, define the places in the binary specific for extract or similar.
Then I tried foremost which is a similar tool for extracting embedded files. It produces an output directory with the extracted files categorized in file-extension directories. Yay - that worked! Now, looking at the extracted image, it seems very much the same, and running a bunch of recursive commands, it just didn't seem to be the correct way to get to the image/information we wanted.
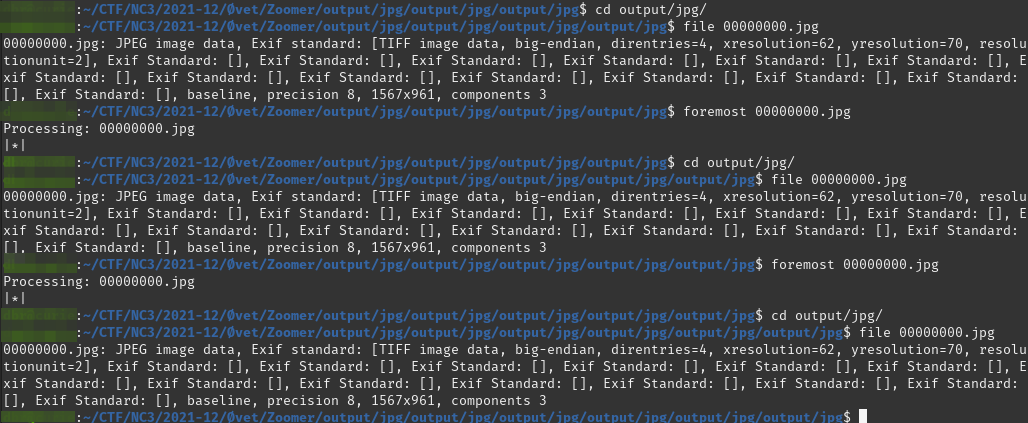
Hmm, what to do now? Clearly something is not 100% correct in our extracting-method for the embedded files. In a brief moment I remembered that CyberChef also has some extraction-tools. What about trying that?
So I did. I uploaded the first foremost extracted image to CyberChef and created a recipe with the "Extract Files" operator. And would you look at that! We have found a tiny image located in the file containing our flag.
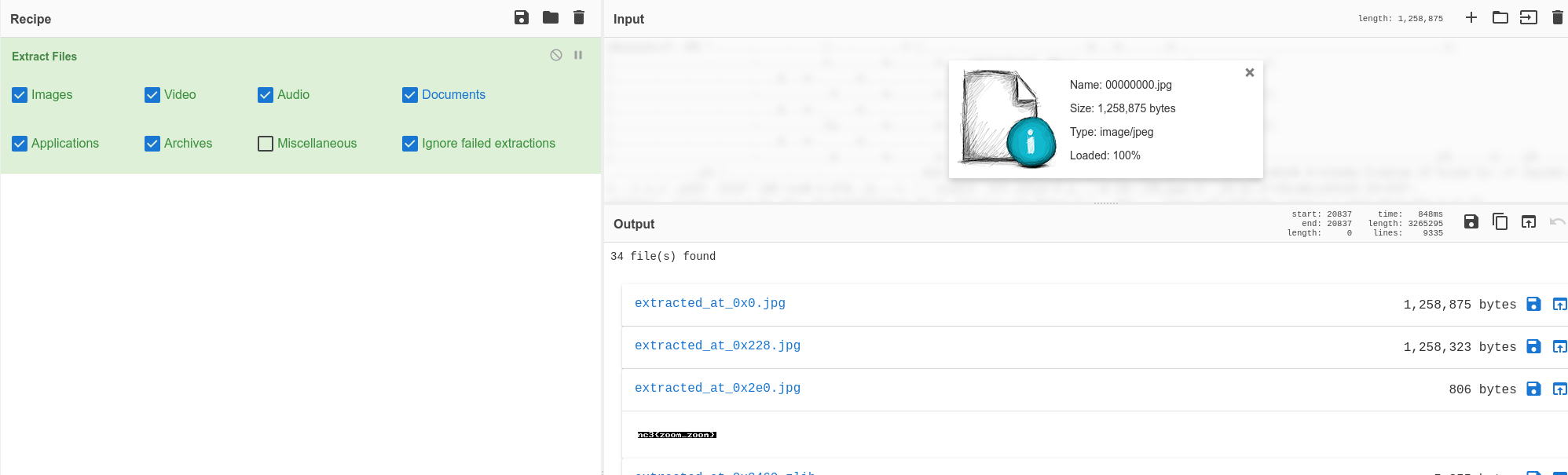
Flag:
nc3{zoom_zoom}Writing this write-up, I was again thinking about why I wasn't able to extract the correct file from the image. Looking at the placement of the file 0x2E0 reported by CyberChef and a file-length of 806 bytes. This is not listed in the first binwalk we performed. So what if the file was "so embedded" that it was kind of hidden? Maybe with some bad or wrong file-descriptors in the binary so when we tried to use automated tools, they was not able to detect the file? Or at least something like that. To detect that, we probably had to dig into the file with tools like hexer for HEX-editing. And deep dive into the file-format/-structure for JPEG images like we did for ZIP-files in the "ZipFil"-challenge from the GuidePoint CTF in august.