The first real challenge at the GuidePoint CTF August 2021 I looked at, was "Hexible".
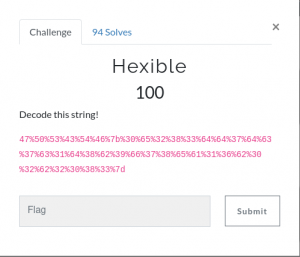
With the "Hexible" challenge we are given a string to decode.
47%50%53%43%54%46%7b%30%65%32%38%33%64%64%37%64%63%37%63%31%64%38%62%39%66%37%38%65%61%31%36%62%30%32%62%32%30%38%33%7dTo a start all the "%" signs seems strange and out of place - funny how they almost is used as delimiters between to character-groups. If we remove them, we are left with an alphanumeric string very much resembling HEX. Performing a HEX-decode on the remaining string, reveals the flag.
We do excatly that in the below tinker.py python-script for this challenge.
#!/usr/bin/env python3
from binascii import unhexlify
data = "47%50%53%43%54%46%7b%30%65%32%38%33%64%64%37%64%63%37%63%31%64%38%62%39%66%37%38%65%61%31%36%62%30%32%62%32%30%38%33%7d"
hexes = ''.join(data.split("%"))
print(unhexlify(hexes))Well - that was a fun little start to the CTF. Not overly complicated with a bit of knowledge around datastructures and how data is looking when encoded in different styles.
FLAG
GPSCTF{0e283dd7dc7c1d8b9f78ea16b02b2083}