TryHackMe - a learning-website excellent for learning and widen ones knowledge in Cyber Security, is having an Advent of Cyber running through the entire christmas. Every day, a new challenge is released with various topics as Web Exploitation, Network Exploitation, OSINT, Cloud Hacking and Defensive Blue Teaming.
This year I'm going to participate in the challenge and write small, and hopefully, interesting writeups on the experience and work to successfully nail all the challenges. TryHackMe's Advent of Christmas can be found at https://tryhackme.com/christmas - where more info is found, the excellent story about elf McSkidy is started (She is the CISO of the Best Festival Company and is in charge of defending Christmas and Santa against The Grinch's malicious cyber-activities) and even prices can be seen. Who knows - we might even get lucky at the end 🙂
Day 1 - Save The Gifts
The Grinch has tampered with the IMS (Inventory Management System) and now toys are produced all wrong. We are to help McSkidy undoing the malicious activities and learn about a web exploitation type called "IDOR", which stands for "Insecure Direct Object reference".
IDOR vulnerabilities is a common website-vulnerability where the developer has put too much trust into user-supplied data. Or given the user a kind of Information Disclosure ability, where id's and similar can be used in fuzzing and gaining access to data that might not be intended for the user - for example another's users profile, hidden/secured pages and so on.
These vulnerabilities often comes in user-supplied GET-data, Session-cookies or other cookies, and variables in POST-forms and similar.
See more on this type of vulnerabilities here: OWASP
The Website
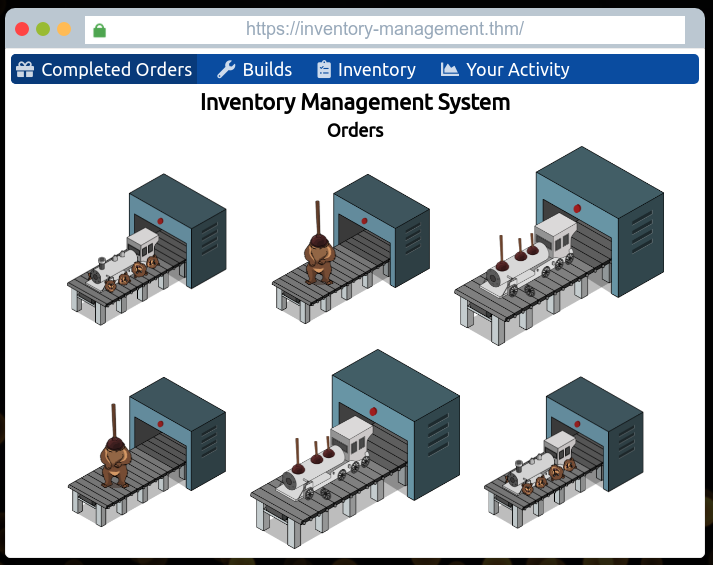
Looking at the first page on the website we are provided, we see the toy orders that are being made all wrong:
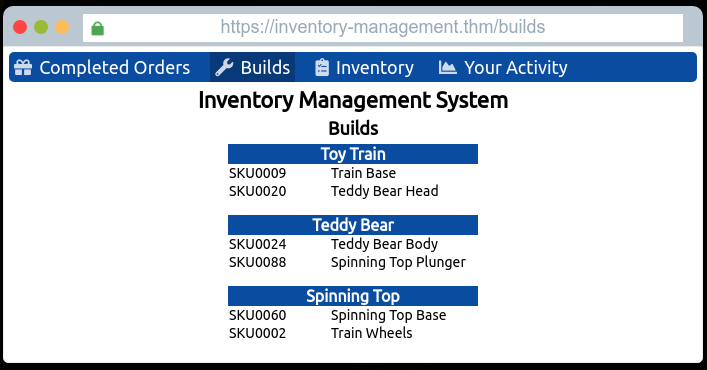
Further we can see the different toy builds and the different SKU-numbers they consist of (and also why the completed orders are all wrong):
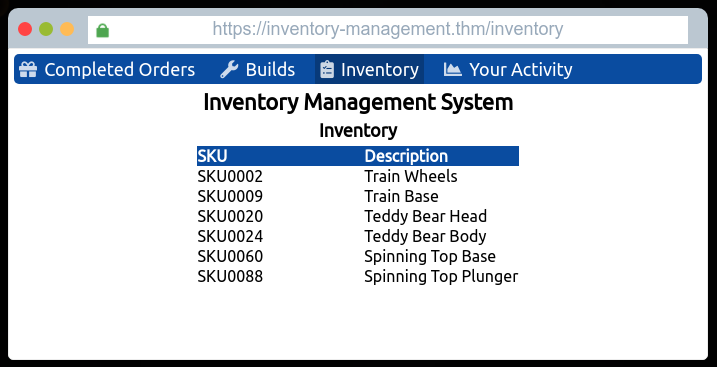
Looking at the next page, we can see all the inventory for the Best Festival Company:
And finally, at the "Your Activity"-page we can see a user-profile for McSkidy - but also, that the user-id is part of the GET-parameter of the website-request:
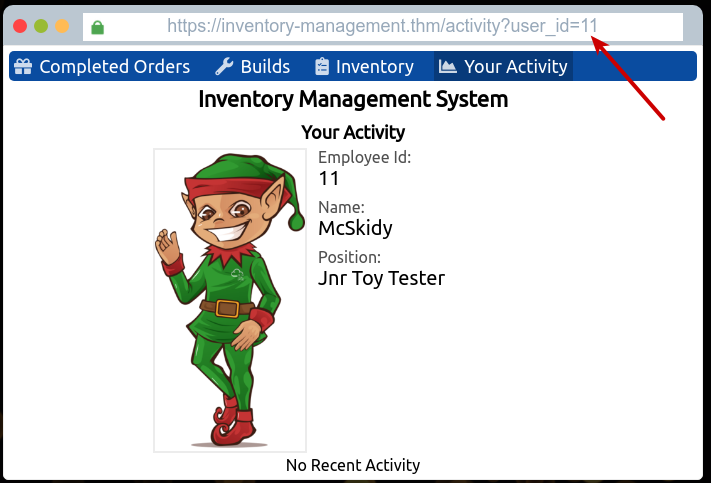
Trying different numbers, and quickly we can see that this IDOR vulnerability gives us access to see other users profile, and even their resent activities.
Answering the Questions
Not giving away any flags or similar, answering the first three questions about Santa's, McStrocker's and the account responsible for the tampering's positions in the company is done by exploiting the IDOR vulnerability and fuzzing the user-id's within 1-20 as we are explained in the task.
Furthermore, we get a flag when reverting all the Resent Actions by the account responsible for tampering.
This concludes the challenge for day one: