Day 13 in the Advent of Cyber 2023. The proposed merger and suspicious activities have kept all teams busy and engaged. So that the Best Festival Company's systems are safeguarded in the future against malicious attacks, McSkidy assigns The B Team, led by McHoneyBell, to research and investigate mitigation and proactive security.
The team's efforts will be channelled into the company's defensive security process. You are part of the team – a security researcher tasked with gathering information on defence and mitigation efforts.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Youtube - CyberInsights.
Day 13 - To the Pots, Through the Walls
When defending in depth as we went through in yesterday's challence, two common practices is as well to implement one or more firewalls and "trip-wires" like HoneyPots.
Firewalls are one of the most important pieces in securing an infrastructure or system from adversaries or threat actors, and most of them are even able to alert of suspicious behaviours. Palo Alto has a quick explainer of the various types of firewalls - but for the overall understanding; A firewall is a gate-keeper investigating all network packets entering and leaving through the firewall. We can then configure it with various rules, and depending on the type of firewall, we can allow or deny traffic to flow. This way, we can ensure only allowed endpoints and network segments can communicate with specified endpoints and network segments.
HoneyPot is a type of deception technology, created to be a very interesting piece for adversaries, threat actors and other malicious intruders. By luring them into the HoneyPot, we can get alerts triggering investigation and incident response. They're mimicking true systems and often looks vulnerable on the surface for this purpose, and when accessed working like "trip-wires" in the infrastructure alerting the SOC or CSIRT about suspicious activities.
The Challenge
In the challenge we're given a Linux machine where we're tasked with working on the host-based firewall installed called "uncomplicated firewall (ufw)", as well as a HoneyPot-system.
The first three questions are answered by reading through today's challenge description. Firstly, the security model that is being used to analyse the breach and defence strategies is the diamond model. Then threat hunting is the defence capability used for actively searching for signs of malicious activities and lastly, "firewall and honeypot" is the answer for which two main infrastructure focuses within this challenge.
The next question is for the command used in ufw to block traffic. Through the challenge we're tasked to configure some firewall rules, enable the firewall and looking at the status. Performing these commands as seen below, we know that deny is used to block traffic.
vantwinkle@ip-10-10-124-102:~$ sudo ufw status
Status: inactive
vantwinkle@ip-10-10-124-102:~$ sudo ufw default allow outgoing
Default outgoing policy changed to 'allow'
(be sure to update your rules accordingly)
vantwinkle@ip-10-10-124-102:~$ sudo ufw default deny incoming
Default incoming policy changed to 'deny'
(be sure to update your rules accordingly)
vantwinkle@ip-10-10-124-102:~$ sudo ufw allow 22/tcp
Rules updated
Rules updated (v6)
vantwinkle@ip-10-10-124-102:~$ sudo ufw deny from 192.168.100.25
Rules updated
vantwinkle@ip-10-10-124-102:~$ sudo ufw deny in on eth0 from 192.168.100.26
Rules updated
vantwinkle@ip-10-10-124-102:~$ sudo ufw enable
Command may disrupt existing ssh connections. Proceed with operation (y|n)? y
Firewall is active and enabled on system startup
vantwinkle@ip-10-10-124-102:~$ sudo ufw status verbose
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp ALLOW IN Anywhere
Anywhere DENY IN 192.168.100.25
Anywhere on eth0 DENY IN 192.168.100.26
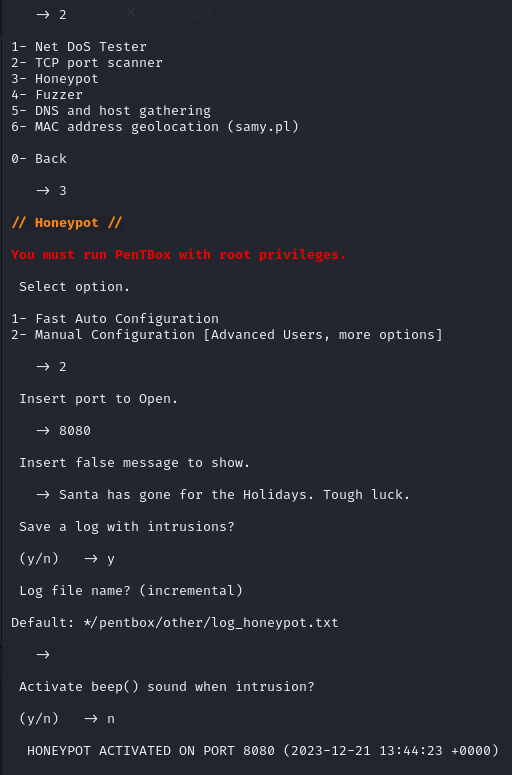
22/tcp (v6) ALLOW IN Anywhere (v6) Going through the challenge tasks, we're now tasked with setting up a network honeypot using PenTBox. Running the pentbox.rb from the installation and then configure the required network pot by selection 2 then 3 and finalizing by configuring the network honeypot manually (2) using port 8080, a custom message and then saving an alert-logfile and disabling the bell.
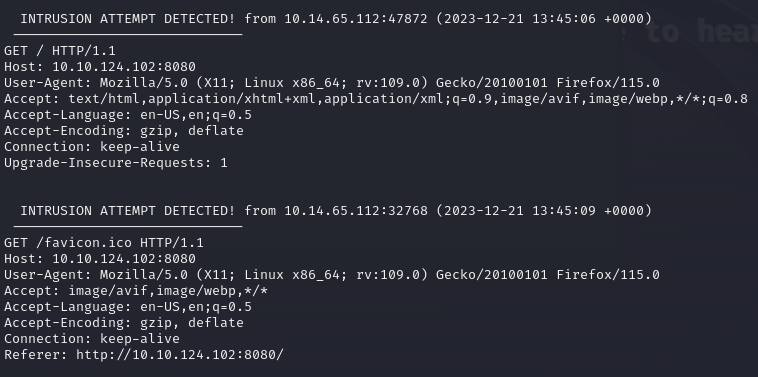
With the network honeypot configured, we then access it in a browser to see that we get the custom message we configured.
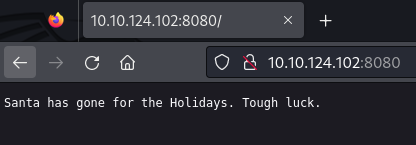
Accessing the HoneyPot as as well triggered an alert.
The last part of today's challenge is to answer the last question, asking us for the flag hidden on a website that Van Twinkle as secured with the firewall. We're instructed to run the command sudo /home/vantwinkle/Van_Twinkle_rules.sh for this part.
Investigating the rules added is the first step to understand where the website might be hidden.
vantwinkle@ip-10-10-124-102:~$ sudo ufw status verbose
Status: active
Logging: on (low)
Default: allow (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
80/tcp ALLOW IN Anywhere
22/tcp ALLOW IN Anywhere
21/tcp DENY IN Anywhere
8088 DENY IN Anywhere
8090/tcp DENY IN Anywhere
80/tcp (v6) ALLOW IN Anywhere (v6)
22/tcp (v6) ALLOW IN Anywhere (v6)
21/tcp (v6) DENY IN Anywhere (v6)
8088 (v6) DENY IN Anywhere (v6)
8090/tcp (v6) DENY IN Anywhere (v6) We can see three interesting paths - port 21/tcp normally used for FTP, 8088 and 8090/tcp. We know that we're searching for a website so the ports 8088 and 8090 are the most interesting here. And further knowing that website traffic normally is TCP, we can change the rule to allow traffic on 8090/tcp via the command sudo ufw allow 8090/tcp. In a browser we then access http://10.10.124.102:8090 and we get a website presented. Scrolling a bit, and a post called "Santa's Challenge" we do get the flag presented for us.