For the fifth year in a row, NC3 (National Cyber Crime Center) under the danish police are hosting a Christmas CTF in the classic Jeopardy-style. With 22 challenges, the fun should be plentiful as we saw in the GuidePoint CTF in August.
The CTF started the 25th of November, but as I'm participating in the TryHackMe's "Advent of Cyber 3" this holiday-season and full-steam ahead on my day-to-day work, I was not able to attend the CTF for the first few weeks. That leaves us with only five days until the end - and with most of them being normal weekdays. Let's see how far we can get - at least we're going to have fun!
One of the interesting part of participating in CTF's, are not just the challenge-solving and the learning-outcomes from that; But also the collection of information and data used in writing write-ups afterwards. Doing so, ensures that the gained knowledge stick, and that I (and others) have the ability to look back on the solving's later, when a similar challenge or even real-life tasks as DFIR (Digital Forensics), Incident Responses and other blue-team tasks arises on the day-to-day work.
NC3 CTF Challenge-board
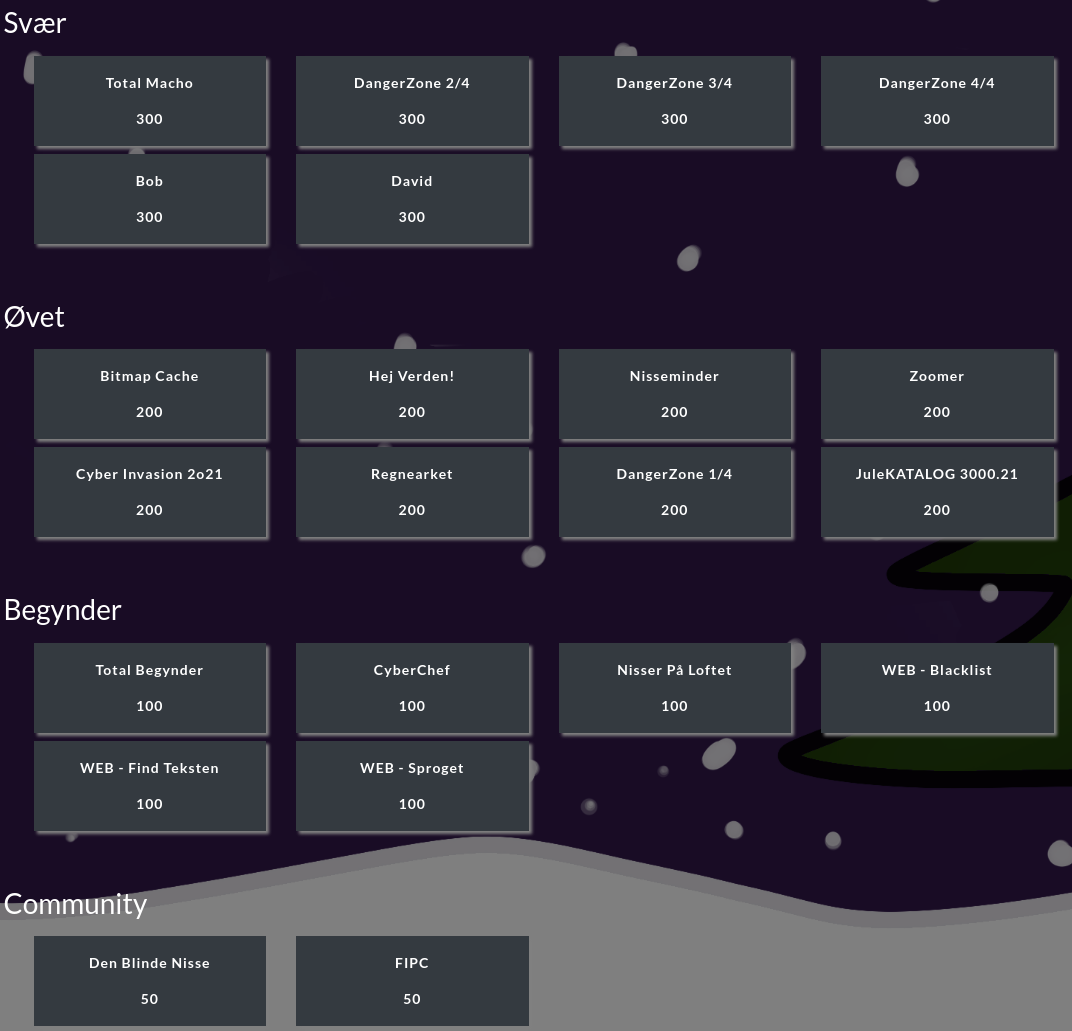
As we can see on the challenge-board above, the challenges are categorized by their difficulty. In this blog-post we are going to look at the challenges in the "Beginner" ("Begynder") category as most of these are fairly strait forward to work on.
Challenge category "beginner"
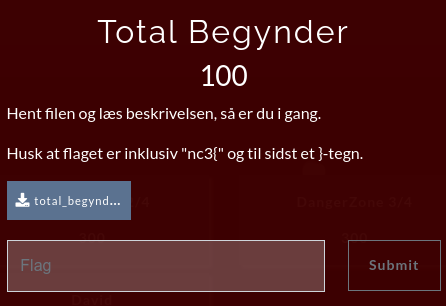
Total Begynder
In the challenge, as seen in the picture below, we are provided with a .txt-file and the information to download the file, read it and remember that flags includes the nc3{...} parts.
We are in the file greeted with an example of a flag nc3{dette_er_flaget} and then the question is we can find the flag in the below listed text.
}ted_ederalk_gej{3cnThis looks very much reversed, so a quick use of CyberChef, and we are provided the flag as we use a Reverse-function.
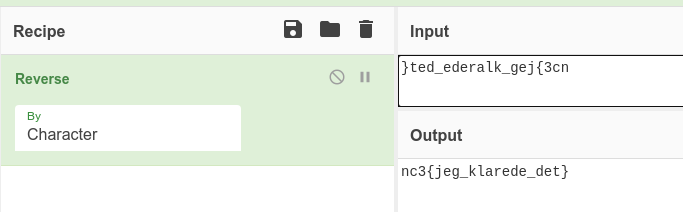
Flag
nc3{jeg_klarede_det}CyberChef
Again, for the next challenge, we are provided a .txt-file. This time we are told that "CyberChef" is a very nice tool, that we should try.
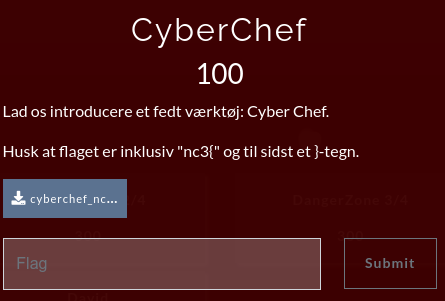
So let us do that. The provided string in the text-file seems to be encoded in base64, as all the characters are alpha-numeric ASCII, and we even see a equal-sign at the end being a common character for padding base64-strings into the required length (sequences of 8-bit bytes).
NmU2MzMzN2I2YTY1Njc1ZjYyNzI3NTY3NjU3MjYzNzk2MjY1NzI2MzY4NjU2NjVmMzQ1ZjY0NjE1Zjc3MzE2ZTdhN2Q=Decoding the base64 reveals another seemly random string of characters - this time only numbers and the letters A-F.
6e63337b6a65675f6272756765726379626572636865665f345f64615f77316e7a7dThis looks a lot like a classic HEX-string, as hexadecimal is known as "base 16". This means that there are 16 different entities within the format. Our normal numbers from 0-9 are called "base 10" as there are 10 different entities.
With that thesis, we apply a HEX-decoder and we are provided a readable flag.
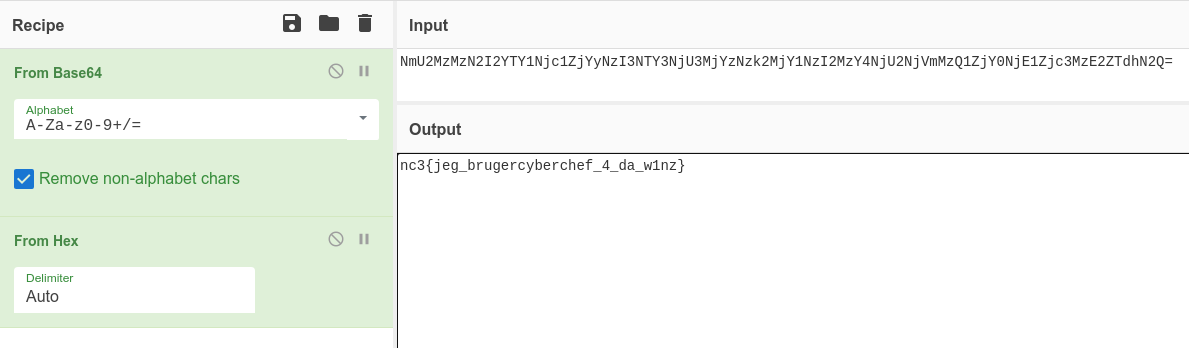
Flag
nc3{jeg_brugercyberchef_4_da_w1nz}Nisser På Loftet
"Elfs In the Attic" is the next challenge we are going to take a look at.
Again we are provided with a .txt-file, this time with something looking much like some sort of an array and maybe a key below?
Er det bare os, der har fået nisser på loftet, eller giver det her rent faktisk god mening?:
0 = 3
1 = n
2 = {
3 = c
4 = }
5 = _
6 = c
7 = u
8 = d
9 = r
1302651758094Converting the numbers and the relations into a proper Python-array and then perform a simple and quick for-loop to pick the characters in the same order as the "key" in the bottom of the file. And we are provided with the flag.
#!/usr/bin/env python3
array = ('3', 'n', '{', 'c', '}', '_', 'c', 'u', 'd', 'r')
sample_key=(1,3,0,2,6,5,1,7,5,8,0,9,4)
flag = ""
for key in sample_key:
flag += array[key]
print(flag)Flag
nc3{c_nu_d3r}WEB - Blacklist
For the last three challenges in the Beginner-category, it seems that we are going to work with some sort of Web Exploitation or similar.
The description for this challenge point us in the direction of TryHAckMe.com where the challenge is hosted in a free-room https://tryhackme.com/room/nc3ctf2021web. Then we are informed to access the website on port 3001 of the attached attack-box.
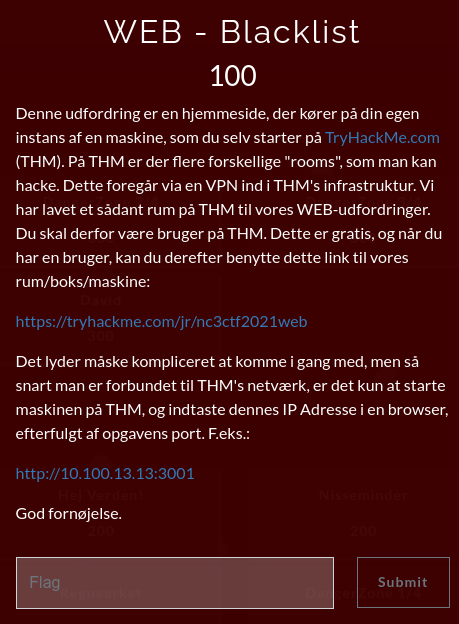
When we access the website, we are greeted with the challenge. An input-field is provided and we are tasked to get the string #nc3ctf2021 through a filtering-system to retrieve the flag. As we can see, we are provided with the code behind the site and they have inserted the most relevant part right on the page. See the full page-code, if curious.
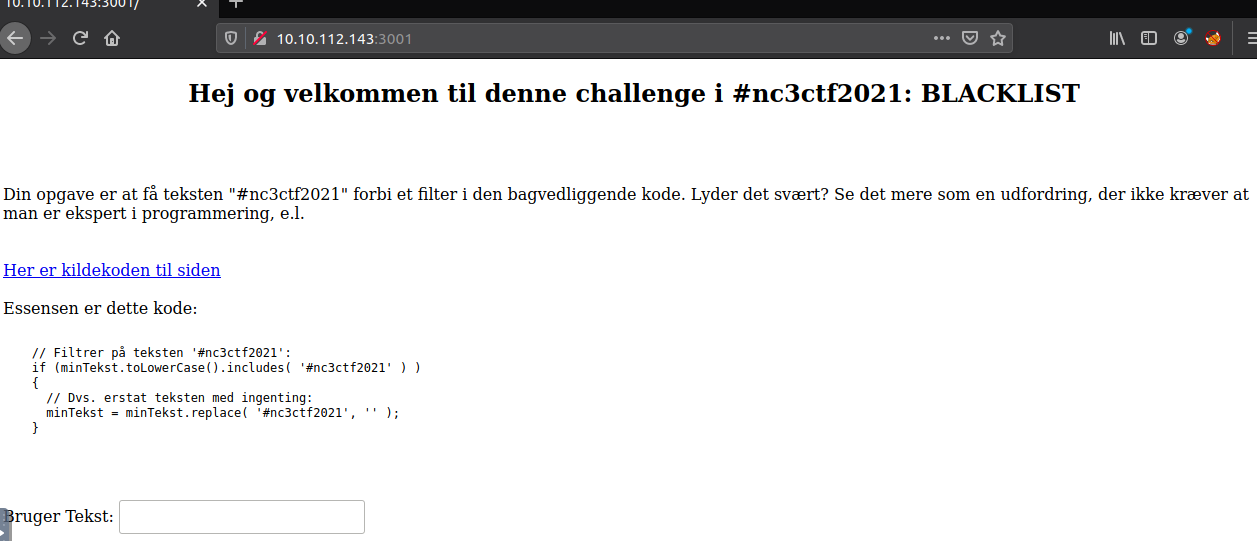
Looking at the full code, we see usages of const xxx, app.use(), app.listen() and similar - this looks very much like node.js. We see almost the same in the "Hello World"-example on the website https://nodejs.org/en/docs/guides/getting-started-guide/. We can see that the code is filtered using an if-statement looking for the string using the .includes() string-function. So looking at that function from javascript, we see that it searches for the provided string and returns a boolean true or false. If the string is found it will use the .replace() string-function - and looking at this function online, we clearly sees that it only replaces the first instance of the string.
With that information we know that we just need to insert the string twice. Then the first instance will be removed and the latter should remain.
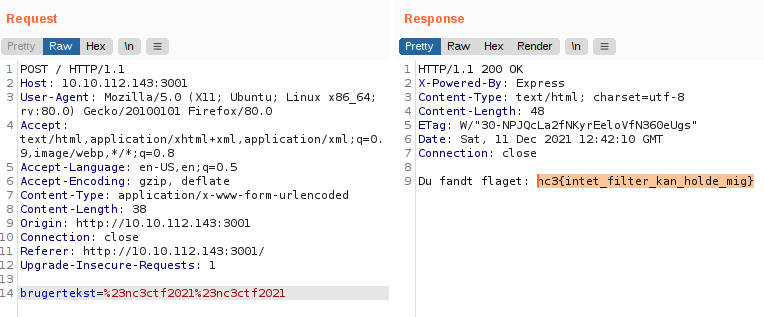
Flag
nc3{intet_filter_kan_holde_mig}WEB - Find Teksten
"Find the text" yet another challenge hosted at TryHackMe.com, found as task two in the same room as the previous challenge.
This time we are tasked to access the website at port 3002 where we are greeted with nice graphics and the text "Find the text".
Nothing seems obvious on the visible part of the webpage, so the next logical step is to look at the source-code for the page. This can be done via the developer-tools often opened by the button F12 or by right-clicking and choose "Show source-code". A quick look, and we found the flag.
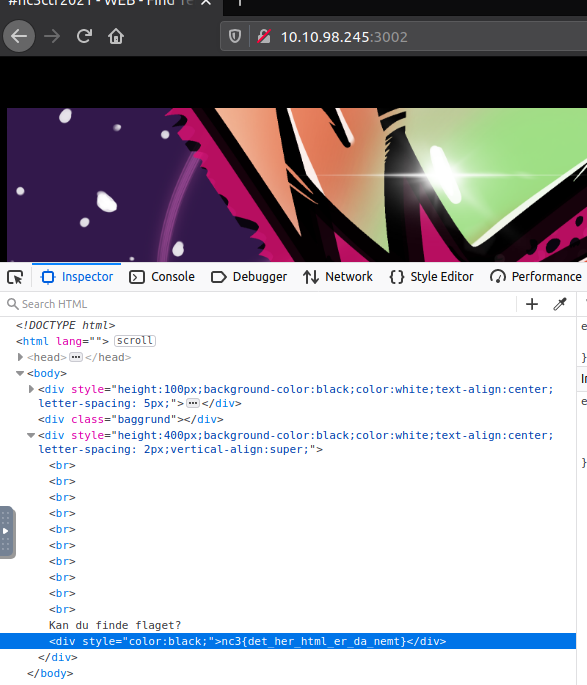
Flag
nc3{det_her_html_er_da_nemt}WEB - Sproget
"The Language" is the last challenge in the beginner-category and is hosted on TryHackMe.com in the same free room as the last two challenges.
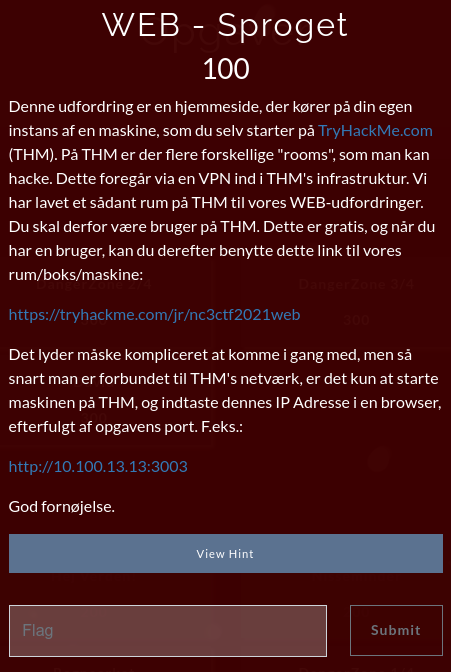
We find the challenge-website at the port 3003. We aren't getting a lot of information other than "The Language fits danish". Looking closer we see a GET-parameter sprog that is set to dansk.
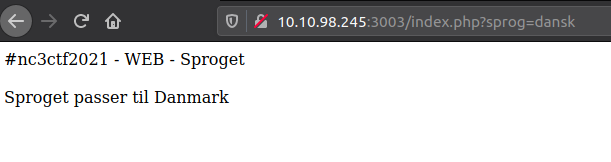
Taking a look at the source for the webpage does not reveal a lot to us. Though a link is provided.
Okay, maybe the link can provide us with more knowledge as part of our reconnaissance for information's we can use in defeating this challenge.
Oh... Well, nice played, CTF-builder.. 😀
Let us quickly move on! We still have the GET parameter to investigate. We start by just filling it with nonsense to see what happens.
A lot of information is now at hand. Firstly, we now know that this is a PHP-site, that it is configured to show PHP-errors (something that is not recommended for production-servers), that the value of the GET-parameter is parsed into a path for the function include() and that the main-page is located in the filesystem at /var/www/html/index.php. That is a handful of interesting information's.
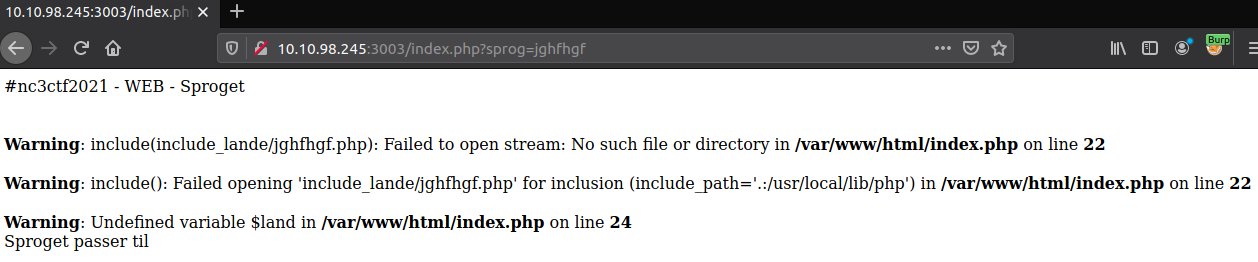
Dealing with the include() PHP-function, could we have some LFI (Local File Inclusion) vulnerability ready for us? We know that we can control at least part of the path provided to the function, but not if the information is parsed in some way or another. Furthermore, we can see that there should be a directory called include_lande ("include_countries") in the same path as the main index.php.
What happens if we just try accessing that endpoint?
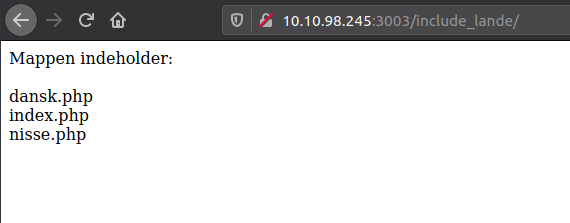
Oh, nice! We have some sort of directory-listing and can see three files. The first one dansk.php give sense as the GET-parameter is set to dansk when we visit the main-page. But what is nisse.php ("elf.php")? That seems suspicious.
Changing the GET-parameter value to nisse in Burpsuite and sending the request reveals the flag for this challenge.
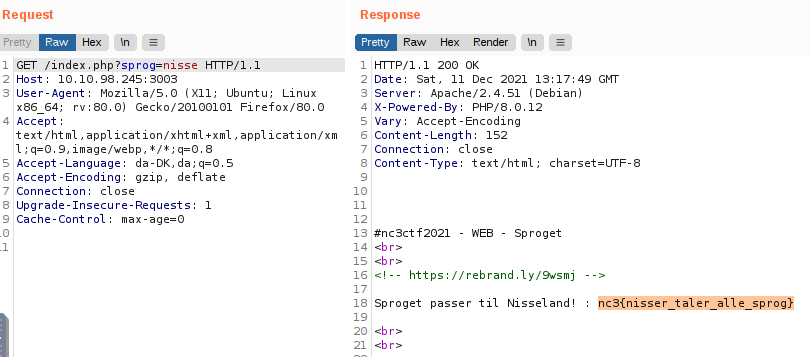
Flag
nc3{nisser_taler_alle_sprog}