Day four in the Advent of Cyber 3 (2021), and Santa's account is in-accessible. Oh no - that's not good, as he expects som urgent travel itinerary for his route over Christmas. McSysAdmin managed to reset everyone's access except Santa's. We need to help bruteforcing access to the account.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHAckMe's Advent of Cyber - Day 4: Fuzzing with Burp Suite.
Day 4 - Santa's Running Behind
Today's challenge is all about fuzzing. Using the application "Burp Suite", we can automate the bruteforcing on a website POST login-page and try many username/password combinations using lists of common usernames and common passwords.
The Challenge
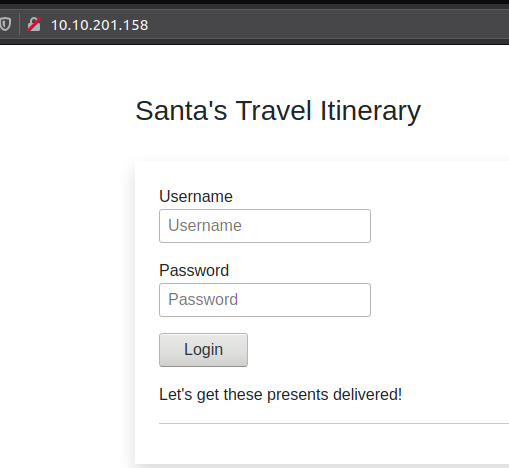
Firstly we open the webpage in the browser for the TryHackMe-box we are provided, and we can see a login screen.
Then we are going to prepare Burpsuite for the fuzzing. This is done by starting Burpsuite with a "Temporary project" and using defaults. Under the "Proxy"-tab, we need to ensure that "Intercept" is on so we can capture the HTTP-requests. Then in Firefox, we are going to enable "FoxyProxy" setting it to "Burp" so that all requests / responses is forwarded through Burpsuite.
Now we provide a bogus username/password and try yo login. This ensures that we now have the correct HTTP-request in Burpsuite that we can use for fuzzing. Looking at the "Proxy"-tab, we now see the POST-request that the browser was sending:
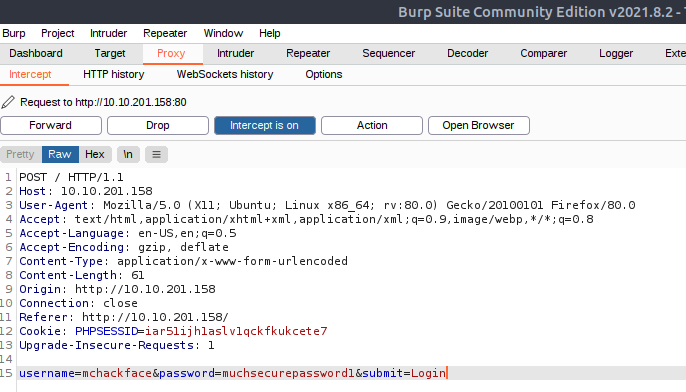
At the bottom of the request, we can see the POST-data that we are going to Intercept. This done by right-clicking and "Send to Intruder" and then change to the "Intruder"-tab.
Here we will go to "Positions" and click Clear $-button on the right to un-select all positions. As we know from the challenge that Santa's username is "santa", we can change the field "username" to that on the last line. Then we want to mark the value for "password" and click Add $on the right to mark a position to fuzz on. Furthermore, we will make sure that the Attack type at the top is set to "Sniper".
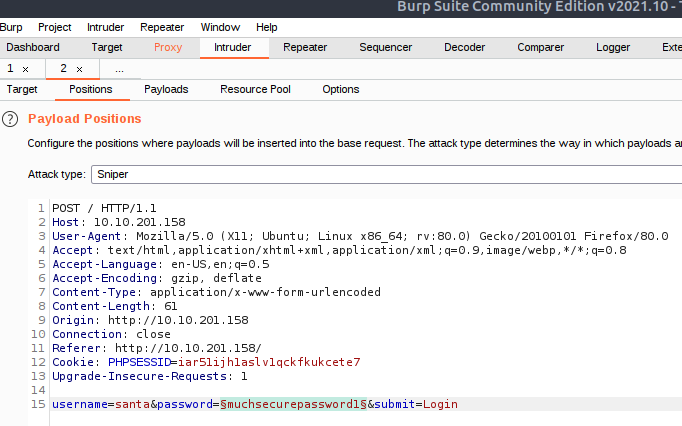
We now need to instruct Burpsuite what we want to fuzz in the marked password-position. This is done in the "Payloads"-pane.
In the "Payload Options" we'll select "Load ..." and open the provided file /root/Rooms/AoC3/Day4/passwords.txt. And with that, we should be ready for pressing the button on the top-right "Start attack", starting the automated fuzzing.
Burpsuite now fuzzes over all the payloads, and giving us information on what was returned. As seen in the picture below, most of the payloads returned a status-code of 200 meaning success. But looking further into the response, it is easy to see that we get a error-page for invalid username/password.
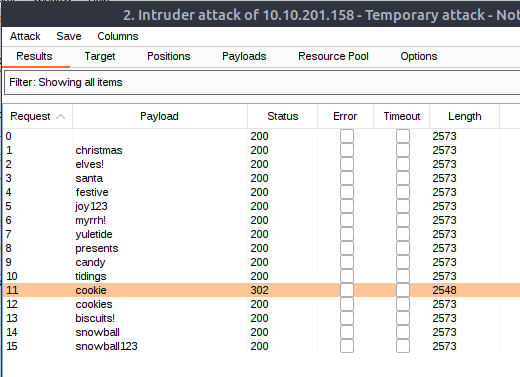
But - there is one payload that is different than the others. It both gives us a status-code of 302 meaning "Found" and has a different length than all the others. This is a clear sign on a successful fuzz. And sure enough, providing the payload-password as the answer in the challenge is the right one. We can even go to the page in the browser, turn off "FoxyProxy" and try logging in with the username "Santa" and the password "cookie".