Day three in the Advent of Cyber 3 (2021) we have a serious problem. Grinch Enterprises has tried to block all communications between anyone at the Best Festival Company. They've locked everyone out of their email systems and McSysAdmin has also lost access to the admin panel.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Try Hack Me: Advent of Cyber 2021 - Day 3.
Day 3 - Christmas Blackout
Today's challenge is Content Discovery and Default Authentications. When a webserver is serving you a website, this website often consist of multiple ressources - images, files folders etc. Furthermore, there is often some sort of admin-page/-dashboard or similar associated with websites. E.g. for all WordPress sites, an example.org/wp-login/ page is available. This page, when logged in, gives access to perform administrative tasks for the site.
These resources is often hidden and not intended for access by users or at least by non-authenticated users. By enumerating on websites to find these resources, we can learn a lot about the website, gain access to folders and files not intended for access and potentially gain information's that we could use for further looking into the systems.
When finding "hidden" admin-pages etc. you often are presented with some sort of log on. When administrators install applications etc., they sometimes forget to disable, remove of change default credentials. Default credentials are often created on applications by its developers to give the administrators an easy start on using the applications. But if not removed or changed, these can be a potentially huge vulnerability, as default credentials often is very easy to guess or find in documentation.
The Challenge
To help McSkidy and McSysAdmin with the email systems, we are going to enumerate on the provided webserver to see if we can figure out where the admin-panel is.
To do so, we're going to use a small application called dirbuster. This application can automate the enumeration for us, so we don't have to check every single resource that we could think of manually. dirbuster requires a "wordlist" of common resources to check and test. We can create and provide our own, or better, we can provide wordlist from SecLists. SecLists is a phenomenal resource created for pentesters withholding many wordlists, default credentials and more, that we can use in our enumeration.
So, the following command is setting up dirbuster to enumerate on the specified TryHackMe-box using the common.txt wordlist from SecLists under "Discovery" and "Web-Content".
dirb http://10.10.161.129 /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txtRunning this command takes some time, but as it goes we see that some interesting resources has been found - e.g. "/admin". That sounds like something we should look further into. The full output can be seen here:
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Dec 5 19:03:53 2021
URL_BASE: http://10.10.161.129/
WORDLIST_FILES: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
-----------------
GENERATED WORDS: 4654
---- Scanning URL: http://10.10.161.129/ ----
==> DIRECTORY: http://10.10.161.129/admin/
==> DIRECTORY: http://10.10.161.129/assets/
+ http://10.10.161.129/index.html (CODE:200|SIZE:5061)
==> DIRECTORY: http://10.10.161.129/javascript/
+ http://10.10.161.129/server-status (CODE:403|SIZE:278)
---- Entering directory: http://10.10.161.129/admin/ ----
==> DIRECTORY: http://10.10.161.129/admin/assets/
+ http://10.10.161.129/admin/index.html (CODE:200|SIZE:2251)
---- Entering directory: http://10.10.161.129/assets/ ----
==> DIRECTORY: http://10.10.161.129/assets/css/
==> DIRECTORY: http://10.10.161.129/assets/fonts/
==> DIRECTORY: http://10.10.161.129/assets/img/
==> DIRECTORY: http://10.10.161.129/assets/js/
---- Entering directory: http://10.10.161.129/javascript/ ----
==> DIRECTORY: http://10.10.161.129/javascript/jquery/
---- Entering directory: http://10.10.161.129/admin/assets/ ----
==> DIRECTORY: http://10.10.161.129/admin/assets/css/
==> DIRECTORY: http://10.10.161.129/admin/assets/js/
---- Entering directory: http://10.10.161.129/assets/css/ ----
---- Entering directory: http://10.10.161.129/assets/fonts/ ----
---- Entering directory: http://10.10.161.129/assets/img/ ----
---- Entering directory: http://10.10.161.129/assets/js/ ----
---- Entering directory: http://10.10.161.129/javascript/jquery/ ----
+ http://10.10.161.129/javascript/jquery/jquery (CODE:200|SIZE:271809)
---- Entering directory: http://10.10.161.129/admin/assets/css/ ----
---- Entering directory: http://10.10.161.129/admin/assets/js/ ----
-----------------
END_TIME: Sun Dec 5 19:04:31 2021
DOWNLOADED: 55848 - FOUND: 4Another tool we can use for the same purpose, is gobuster. I kind of like this tool, as it seems to be a tad faster - at least if only instructed to enumerate for the current directory as seen below (of cause dirbuster could be told to not run recursively by adding the flag -r):
root@ip-10-10-100-250:~# gobuster dir -u http://10.10.161.129 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.161.129
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/12/05 19:05:48 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/admin (Status: 301)
/.hta (Status: 403)
/assets (Status: 301)
/index.html (Status: 200)
/javascript (Status: 301)
/server-status (Status: 403)
===============================================================
2021/12/05 19:05:52 Finished
===============================================================With these automatic enumerations, we now have the answer for the first question as the most interesting path is admin.
Opening the webpage in the browser shows us the default email system page.
But our enumeration/fuzzing has found the /admin - let's try that page.
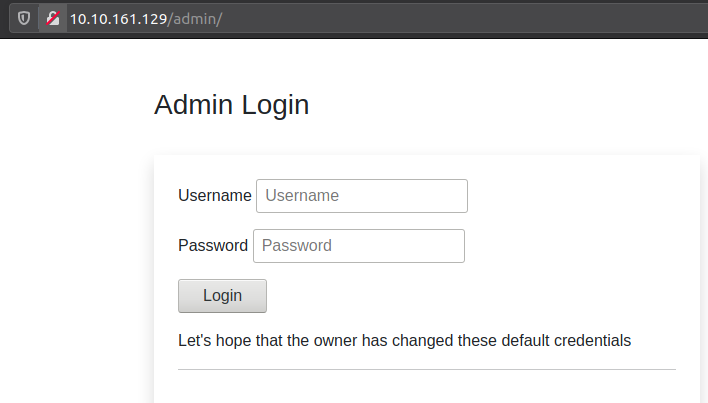
Uhu - that is interesting. For the next question in the challenge, we are tasked to try logging in to the account for the user "administrator" by fuzzing default credentials.
Again, this can be done automatic using an application as e.g. Burp Suite, but maybe we can get lucky by doing a small manual fuzzing. The first password interesting is "administrator" - yes, the exact same as the user (very common for default credentials). And would you look at that - it worked:
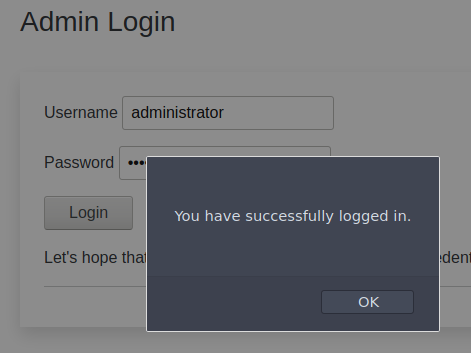
We now have the answer for question two and pressing "OK" we are redirected into the Admin Page, where the flag for the last question is visible.
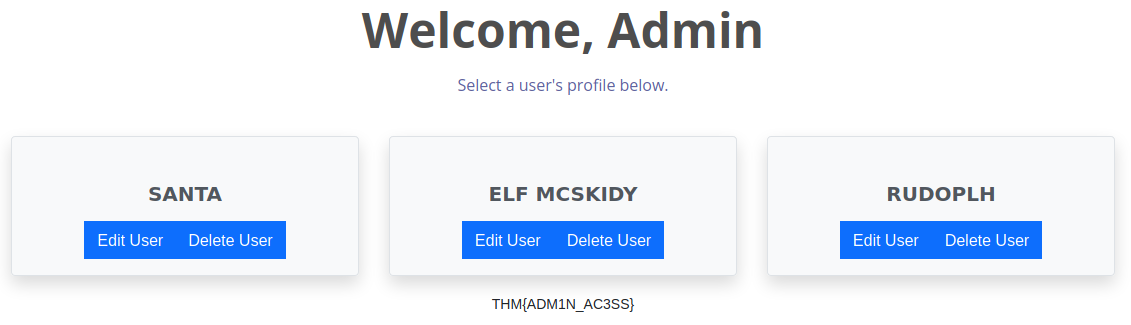
Using a little enumeration and fuzzing, we got access to the admin page for the system. When performing pentesting, these skills and workflows are essential in getting knowledge into the systems you are pentesting, as you gather information's in a process called reconnaissance - though the default credentials fuzzing is more of a brute force attack than purely reconnaissance (for that it would have been looking into the applications documentation to find default credentials).