Day five in the Advent of Cyber 3 (2021). Another day Grinch Enterprises has been a thorn in the eye of McSkidy. The Elf Forum has been manipulated and now all mentions of Christmas has changed to Buttmas! Grinch Enterprices has one bad admin account, they use to provide all this horror on an Elf Forum where all should be joy and excitement about Christmas.
With this account, they where able to install a plugin changing all Christmas mentions to Buttmas. We need to help taking over the bad Grinch admin-account and disable the plugin to restore the Christmas joy.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at TryHackMe's Advent of Cyber - Day 5: Web Exploitation - Cross-site Scripting (XSS) Explained.
Day 5 - Pesky Elf Forum
The challenge today relies on Cross-Site Scripting (XSS) vulnerability. XSS is a type of injection, in which malicious scripts are injected on vulnerable sites. This could be used to steal a victim's cookies taking over session-cookies (remember the challenge from day 2.), running keyloggers, redirecting the user to malicious websites or similar.
There is multiple distinct types of XSS - DOM, Refelected, Stored and Blind.
DOM: Is a less well-known type where re response resources from the webserver is all benign, but changes to the DOM environment directly in the clients browser.
Refelected: This type of XSS happens when user-supplied data in a request is included in the webpage-source without any validation. So e.g. GET-data that shown as part of the webpage - changing that to include javascript, and you have XSS.
Stored: Here the malicious script is stored by the webserver - e.g. in a database or similar. And then included as part of the webpage, when retrieved. This cloud be a blog allowing for comments or similar.
Blind: Much like the stored type, the malicious script/payload is stored on the webserver, but not visible when working or able to test yourself first. For example a contact form where XSS could be possible in the message-field or similar.
See more about XSS on OWASP.
The Challenge
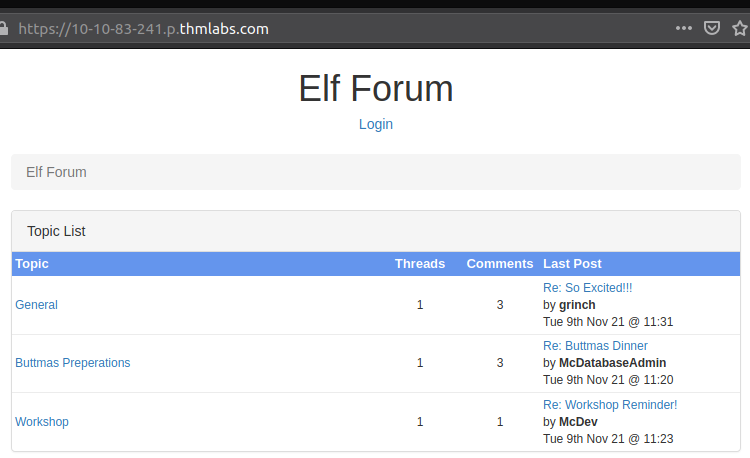
After starting the challenge-machine, we open the website https://MACHINE_IP.p.thmlaps.com, and we immediately see the Elf Forum and the horror that has occurred.
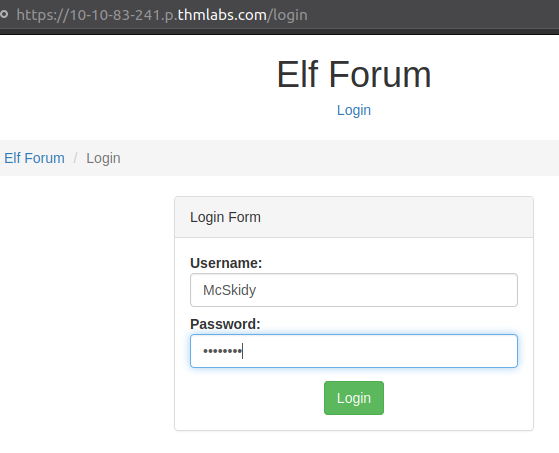
We are then instructed in the challenge to click the Login-button at the top and log in with the username McSkidy and with the password password.
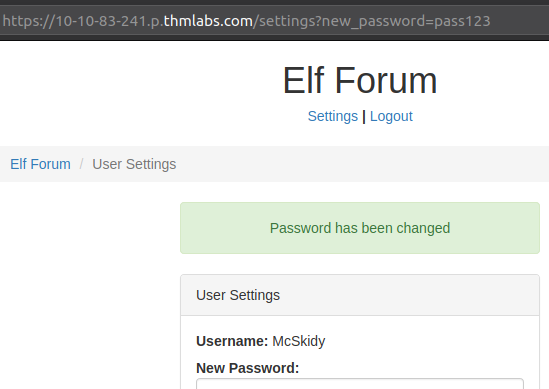
Now we are logged in, we have to go to the Settings-page, where we are able to change the password for our user. But looking at the GET-request data in the address-bar of the browser (see picture below), when changing password the new password is sent to the server via the request and there seems not to be any validation on the user or similar. So, if Grinch's bad admin-account where to access the website with the same parameter, the password would be changed.
Back at the forum, we are able to leave comments. Comments are saved in the database, so maybe we can use it for XSS? Testing with simple HTML can show us that HTML-tags are not stripped away, telling us that XSS could be possible.
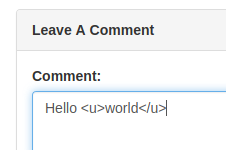
So, with the javascript code wrapped in HTML should then work by fetching the change-password page for everyone access the blog-post with the "malicious" comment in.
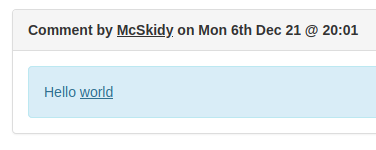
<script>fetch('/settings?new_password=pass123');</script>Adding that in a comment, and we see the code is not wrapped but interpreted as code.
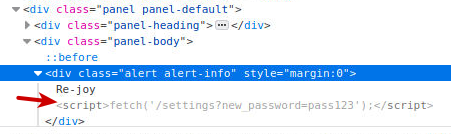
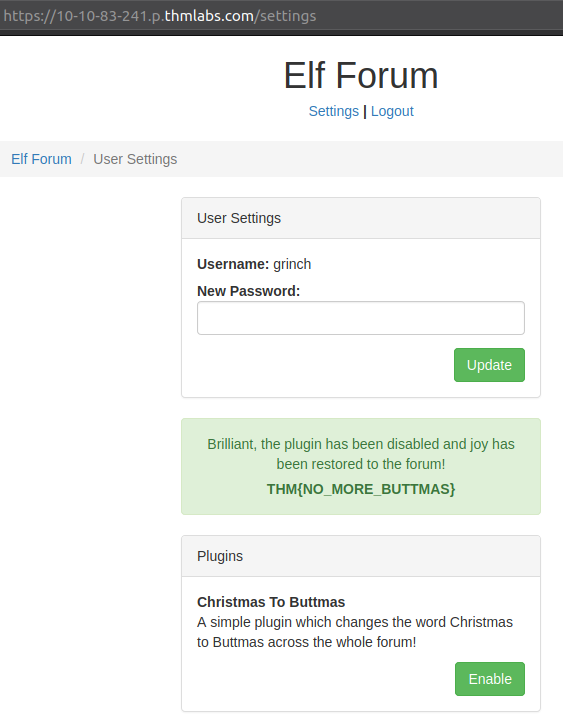
After a bit of waiting, we can logout and try logging ind with the username grinchand our provided password pass123 - and behold, we are able to log on the Grinch's bad admin-account. Now it's just as easy as going to the Settings-page and click "Disable" to the malicious plugin and the challenge flag is revealed.