Day 12 in the Advent of Cyber 3 (2021). Grinch Enterprises has been leaving traces of how their hackers have been accessing data from the systems. How are they accessing the systems? We need to help figure that out, to help stopping Grinch Enterprises messing with Christmas.
WARNING: Spoilers and challenge-answers are provided in the following writeup.
Official walk-through video is as well available at Advent of Cyber 3 (2021) - Day 12 - Sharing Without Caring - TryHackMe.
Day 12 - Sharing Without Caring
A system has been noticed generating unusual traffic. We are tasked to use nmap, a great network scanning tool, to enumerate the system and figure out what could be the issue at hand.
Furthermore, we are enlightened with the information of NFS-protocol (Network File System). This protocol is commonly used to share files between machines over the network, make directories/filesystems mountable over the network and more.
The Challenge
The challenge today starts with starting the Attack-machine holding the machine for us. The first task is to perform a nmap-scan, where we are told to use the -Pn-flag as the machine is a Windows-machine. This is to ensure we are not waiting forever to receive ping-answers, as Windows machines are configured by default to not answer these.
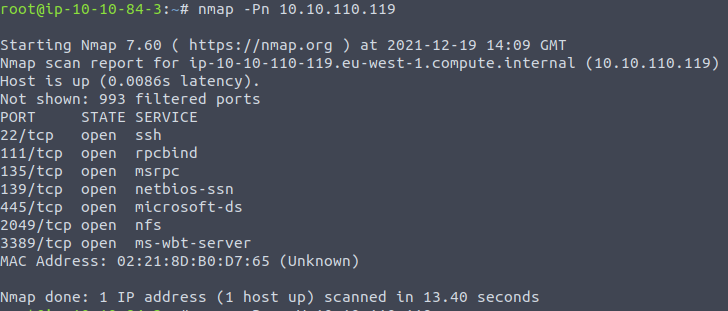
We now have the answers for the two first questions - how many TCP-ports are open, and which port is NFS using. As a bonus, we also can see that NFS is using its standard port of 2049.
So now we can try enumerating what shares, or exports as they are called for NFS, are provided by the server. This is done with the tool showmounts (be aware that this tool will not work for NFS version 4).
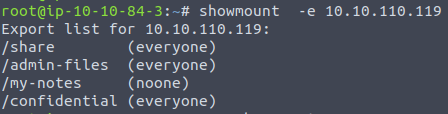
This gives us the answer for the following two questions - how many shares is there and how many are reported as "everyone"?
Shares, or exports, noted as "everyone" are always interesting for pentesting as they are readily available for all uses with access to the network. For a security-standpoint, this is not very safe and you should always ensure some kind of authentication and authorization for shares/exports created.
We can now try mounting the shares to get access to the content of those. This is done by firstly creating a directory (mkdir <directory-name>) and the use the mount command like so:
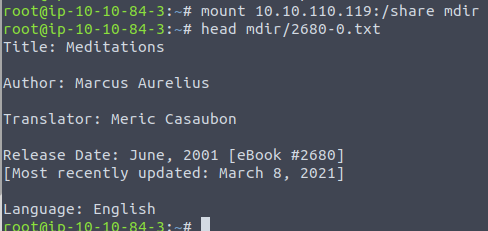
mount 10.10.110.119:/share mdirOkay, so with the /share mounted into the directory mdir we can use normal filesystem-commands to interact with the share. The question for what the title for the file 2680-0.txt inside the /share-share can then be found via e.g. head.
With that answered, we have to find the share that Grinch Enterprises has saved a private key for SSH authentication.We can create a new directory for mounting when running through, or we could just reuse our already created directory. To do so, the old mounted share has to be removed first. This is performed with the command umount mdir.
Running through the shares, we find the interesting id_rsa files in the share /confidential.
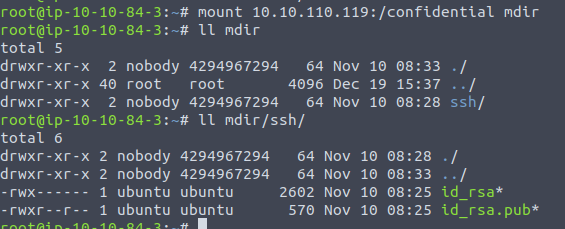
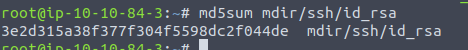
The final task then, is to calculate the MD5-hash for the id_rsa-file.